Write a Java program called AverageAge that includes an integer array called ages [] that stores the following ages; 23,56,67,12,45. Compute the average age in the array and display this output using a JOptionPane statement
Answers
The Java program "AverageAge" computes the average age from an integer array and displays it using a JOptionPane dialog. It calculates the sum of ages, computes the average, and presents the result.
import javax.swing.JOptionPane;
public class AverageAge {
public static void main(String[] args) {
int[] ages = {23, 56, 67, 12, 45};
int sum = 0;
for (int age : ages) {
sum += age;
}
double average = (double) sum / ages.length;
String message = "The average age is: " + average;
JOptionPane.showMessageDialog(null, message);
}
}
This program initializes an integer array called ages with the provided ages. It then calculates the sum of all ages by iterating over the array using an enhanced for loop. The average age is computed by dividing the sum by the length of the array. Finally, the average age is displayed using a JOptionPane.showMessageDialog statement.
know more about array here: brainly.com/question/17353323
#SPJ11
Related Questions
Annie has a three year old laptop. She is giving it a full service before selling it on. (a) Annie runs some 'Disk Health' utility software to check for any problems with her HDD. (i) Define what is meant by utility software.
Answers
Utility computer program could be a sort of computer program that gives particular usefulness to help with the upkeep as well as the administration of a computer framework.
What is utility software?Utility computer program is computer program planned to assist analyze, arrange, optimize or keep up a computer. It is utilized to back the computer foundation - in differentiate to application program, which is pointed at specifically performing assignments that advantage standard clients
Therefore the use of MS Word is an case of application computer program created by the company Microsoft. It permits clients to sort and spare archives. It is accommodating as well for making records.
Learn more about utility software from
https://brainly.com/question/30365102
#SPJ1
Write a static method reOrder56(int[] nums) that return an array that contains exactly the same numbers as the given array, but has been reorderd so that every 5 is immediately followed by a 6. You may choose to move every other number with the exception of 5; You are not to move 5. The array contains the same number of 5's and 6's, every 5 has a number after it that is not a 5, and a 6 appears in the array before any 6.
Answers
Answer:
Follows are the code to the given question:
static int[] reOrder56(int[] nums)//defining a static method reOrder56 that holds an array in parameter
{
int x,y;//defining integer variables
for(x=0;x<nums.length;x++)//using for loop that counts array
{
if(nums[x]==5 && nums[x+1]!=6) //defining if block checks arry values
{
for(y=0;y<nums.length;y++)//use for loop to count array value again
{
if(nums[y]==6 && nums[y-1]!=5)//defining if block checks arry values
{
nums[y] = nums[x+1];//swap the array element value
nums[x+1] = 6;//holing value in array
break;//break the condition
}
}
}
}
}
Explanation:
In this code, a static method "reOrder56" is declared that takes an integer array "nums" in its parameter, and inside the method, two integer variable "x, y" is defined, which is used in the nested loop.
In the first loop, it holds array values and uses the if block to check the array element value and define another loop to check the same condition, and this block, swap the value and holds the value in the array and breaks the condition.
Which online article citation is correctly formatted according to MLA standards?
A) Oh, Inae. "Dude Who Fell Asleep During Yankees Game Sung MLB, ESPN For $10 Million." The Hillington Post.
The Huffington Post.com, 12 July 2014. Web. 7 July 2014.
B) Oh, Inae. "Dude Who Fell Asleep During Yankees Game Suing MLB, ESPN For S10 Million," The Huthington Post, 7
July 2014. Web. 12 July 2014
C) Oh, Inae. "Dude Who Fel Asleep During Yankees Game Suing MLB, ESPN For $10 Million." The Huffington Post
The Huffington Post.com. 7 July 2014. Web. 12 July 2014.
D) "Dude Who Fell Asleep During Yankees Game Suing MLB, ESPN For $10 Million" The Huffington Post. The
Huffington Post.com, 7 July 2014. Web. 12 July 2014
Answers
Answer:
A is the answer
Explanation:
Hope this helps!! Please consider marking brainliest!!!
Answer: Its C
Explanation:
Sorry Im late :/
The following algorithm accepts 3 integer values from the user, and then prints the maximum value entered. Some lines are missing.
Complete the program by inserting instructions after Line 4
1. OUTPUT (“Please enter 3 values. “)
2. Input (x, y, z)
3. MaxValue x
4. IF y > MaxValue THEN
MaxValue y
Answers
Answer:
1. OUTPUT (“Please enter 3 values. “)
2. Input (x, y, z)
3. MaxValue = x
4. IF y > MaxValue THEN
5. MaxValue = y
6. IF z > MaxValue THEN
7. MaxValue = z
8. OUTPUT("Maximum value is: ", MaxValue)
problem 1. (40 points) consider the following relational database: student ( student number , name ) course ( course number , year , semester , classroom ) registration ( ? ? ? ) (a) (10 points) identify an appropriate primary key for each of the student and course relations. assume that (i) each student is assigned a unique number, (ii) for each combination of year and semester (e.g., 2023 spring), each course is assigned a unique course number, and (iii) a course with a certain course number (e.g., csi 410) may have been offered multiple times (e.g., 2022 fall and 2023 spring). explain why the primary key that you have chosen for the course relation is a candidate key. (b) (10 points) given your choice of primary keys for the student and course relations, identify appropriate attributes for the registration relation. this registration relation must store data regarding the courses that each student has taken. assume that a student may have taken a course (e.g., csi 410) multiple times (e.g., 2022 spring and 2022 fall). also, identify an appropriate primary key for the registration relation. (c) (10 points) given your choice of primary keys, identify all of the foreign keys. for each foreign key, specify the referencing and referenced relations. (d) (10 points) describe a situation where an attempt to update the registration relation violates a foreign key constraint. explain why your answer is correct.
Answers
Removing a row from a foreign key table while leaving the related entry in the primary key table intact.
Using a referential integrity rule will prevent you from adding data to table Y that cannot be linked to data in table X. In order to maintain referential integrity, any records that are linked to a removed record from table X must also be deleted. A database is considered to be in referential integrity when all values for all foreign keys are valid. Foreign keys are a column or set of columns in a table that must contain values that correspond to at least one of the main key or unique key values of a row in its parent table. The necessary entry from the linked primary key table must still be present when removing a row from a database with foreign keys.
Learn more about Referential integrity here:
https://brainly.com/question/29534597
#SPJ4
what has occurred when a user accesses resources in an unauthorized way?
Answers
A security breach has occurred when a user accesses resources in an unauthorized way.
When a user accesses resources in an unauthorized way, it means that they have bypassed the intended security measures and gained unauthorized access to sensitive information, systems, or resources. This can happen through various methods such as exploiting vulnerabilities, using stolen credentials, or employing unauthorized techniques to gain access.
Unauthorized access poses a significant security risk as it can lead to data breaches, privacy violations, loss of confidentiality, and potential damage to systems and networks. It is crucial for organizations to have robust security measures in place, including access controls, authentication mechanisms, and monitoring systems, to prevent and detect unauthorized access attempts.
You can learn more about security breach at
brainly.com/question/4425414
#SPJ11
What is the importance of renaming layers in GIMP?
Answers
Answer:
They allow for a more organized workspace. Specially in larger projects, having properly named layers helps keep things organized an sane.
Explanation:
Suppose we are using a three-message mutual authentication protocol, andAlice initiates contact with Bob. Suppose we wish Bob to be a stateless server, and thereforeit is inconvenient to require him to remember the challenge he sent to Alice. Lets modify theexchange so that Alice sends the challenge back to Bob, along with the encrypted challenge. So the protocol is:Step 1: Alice send a message [I’m Alice] to Bob. Step 2: Bob sends a random number, R. Step 3: Alice sends a message [R,KAlice−Bob{R}]. Is this protocol secure?
Answers
No, this protocol is not secure. A secure mutual authentication protocol must, among other things, support mutual authentication, which allows both parties to confirm the identities of one another.
Due to the fact that Bob cannot recall the challenge he gave to Alice, he is unable to confirm Alice's identity using this protocol. As a result, an attacker can read Alice and Bob's messages and then pretend to be Alice to Bob by simply playing back the message that Alice originally sent.
This problem can be resolved by changing the protocol so that Bob sends a challenge along with the random number R, and Alice must respond with the challenge as well. This way, Bob can verify Alice's identity by checking if the challenge in Alice's response matches the one he sent earlier.
For such more question on protocol:
https://brainly.com/question/8156649
#SPJ11
Fill in the blanks to complete the “countdown” function. This function should begin at the “start” variable, which is an integer that is passed to the function, and count down to 0. Complete the code so that a function call like “countdown(2)” will return the numbers “2,1,0”.
Answers
Answer:
Check the code down below
Explanation:
You can use this code:
for i in range(5,-1,-1):
print(i)
This will print:
5
4
3
2
1
0
5 is changeable by the way!
The complete the “countdown” function. This function should begin at the “start” variable, which is an integer that is passed to the function, and count down to 0 is in the explanation part.
What is programming?The process of creating a set of instructions that tells a computer how to perform a task is known as programming.
Computer programming languages such as JavaScript, Python, and C++ can be used to create programs.
Here is the code to complete the “countdown” function:
def countdown(start):
for i in range(start, -1, -1):
print(i, end=",")
The countdown function takes an integer start as an argument and counts down from start to 0 using a for loop.
The range function is used to generate an integer sequence from start to 0, with a step size of -1. (i.e., counting backwards).
Thus, each integer in the sequence, separated by commas, is printed using the print function.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ2
your sdi nitrox diver certification allows you to use nitrox mixtures whose oxygen content ranges as high as 40 percent (ean40)?
Answers
Your sdi nitrox diver certification allows you to use nitrox mixtures whose oxygen content ranges as high as 40 percent (ean40).
The above statement is True.
What is a nitrox mixture?
Any mixture of nitrogen and oxygen gases, excluding trace gases, is referred to as nitrox. Included in this is atmospheric air, which consists largely of argon but also contains around 21% oxygen, 78% nitrogen, and 1% other gases.
Nitrox is a tool that can be useful when used properly, but deadly when not, just like every other piece of equipment and information a diver carries. With everything else being equal and the gas supply permitting, the nitrox has the goal to extend your no-stop dive time so that you can have longer dives and/or shorter surface intervals.
To learn more about nitrox, use the link given
https://brainly.com/question/28343107
#SPJ4
Which of the following choices is not an example of a typical post-installation task?
A. Format the boot volume
B. Activate Windows Server
C. Assign a computer name
D. Assign a static IP address
Answers
Post-Installation Activities. removing the Software. Recognizing the Deinstallation software from workstations is uninstalled. Remove the Local OEE from the Deployment Server.
Describe post-installation?Post-Installation refers to the time following the Installation Visit and ending with the Customer's receipt of the first bill generated by a smart meter for meters in the credit mode or the first vend for meters in the prepayment method.
In construction, what is post installation?The term "Post-Installation Period" refers to the time period that starts on the day that the required Specified Assets are finally installed at the Goleta Facility and lasts for a year after that.
To know more about Post-Installation Activities visit :-
https://brainly.com/question/13814331
#SPJ4
write a function called missing letters that takes a string parameter and returns a new string with all the letters of the alphabet that are not in the argument string. the letters in the returned string should be in alphabetical order
Answers
To write a function called missingLetters that takes a string parameter and returns a new string with all the letters of the alphabet that are not in the argument string, you can use the following code:
// Create a string of all the letters in the alphabet
const alphabet = 'abcdefghijklmnopqrstuvwxyz';
// Declare an empty string
let result = '';
// Iterate through alphabet and check if each letter exists in str
for (let i = 0; i < alphabet.length; i++) {
let currentLetter = alphabet[i];
if (!str.includes(currentLetter)) {
result += currentLetter;
}
}
// Return the sorted result
return result.split('').sort().join('');
}
Learn more about programming: https://brainly.com/question/26134656
#SPJ11
in the lectures, there is an example of web server using multi-threading. it creates a new thread to serve every request. suppose you like to limit the resource consumption by allowing no more than 100 active threads simultaneously, how do you modify the code to realize this limit?
Answers
A style of program execution known as "multithreading" enables the creation of many threads that can run concurrently and independently while sharing process resources. If allocated to their own CPU core, threads may be able to operate in full parallel, depending on the hardware.
Performance is the main justification for adding threads to a program.
There is a web server example employing multi-threading in the lectures. In order to fulfill each request, it starts a new thread. How would the code be modified if you wanted to implement a limit of 100 active threads at a time to reduce resource consumption?
In this scenario, we may monitor the quantity of newly created threads.
To learn more about Multithreading refer to:
https://brainly.com/question/13155644
#SPJ4
To a traditional computer, one means
and zero means
O a. on, off
O b. up, down
O c. plus, minus
O d.right, left
Answers
a.on , off
In most computer processors, electron movement is controlled by tiny switches that turn this flow of electricity on and off...zero represents off and one represents on
7.2 code practice edhesive. I need help!!
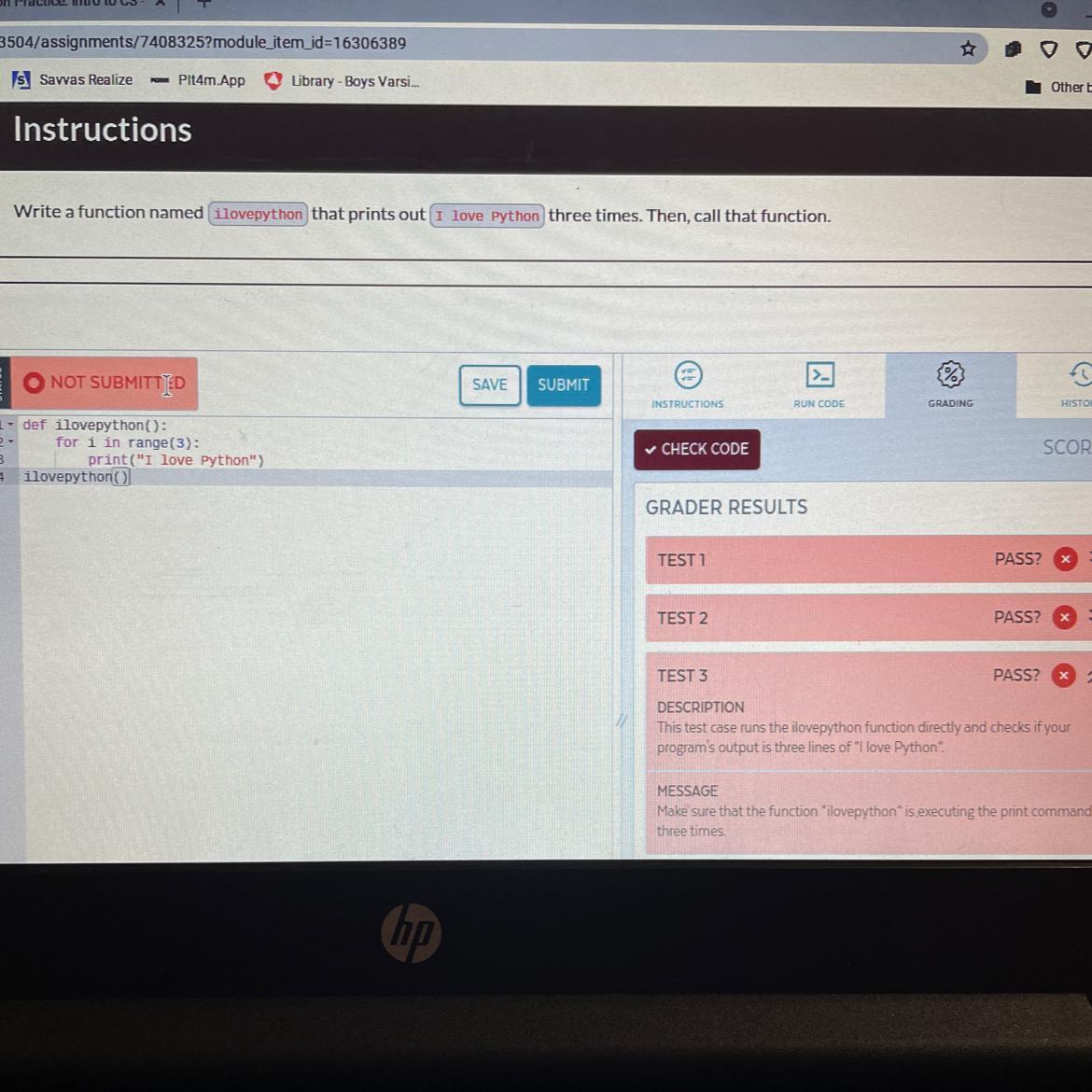
Answers
Answer:
It already looks right so I don't know why it's not working but try it this way?
Explanation:
def ilovepython():
for i in range(1, 4):
print("I love Python")
ilovepython()
Henry wants to use handheld computers to take customers' orders in her restaurant. He is thinking of using custom written, open source software. Describe what is meant by custom written software.
Answers
Answer: See explanation
Explanation:
Custom written software refers to the software that's developed for some particular organization or users. It's crates in order to meet the unique requirements of a business.
Since Henry is thinking of using custom written, open source software, then a custom written software will be used. Examples of custom written software will be automated invoicing, bug tracking software, E-commerce software solutions etc.
List three ideas for checking in with your progress and recognizing completion on your actions.
Answers
One idea for checking in with your progress and recognizing completion on your action is to set specific milestones or targets along the way and regularly evaluate your progress towards them.
How can you effectively track your progress and acknowledge completion of your action?To effectively track your progress and acknowledge completion of your action, it is important to establish clear milestones or targets that can serve as checkpoints. Break down your overall goal into smaller, measurable objectives that can be achieved incrementally.
Regularly assess your progress by comparing your actual achievements against these milestones. This will provide you with a tangible way to track your advancement and ensure that you stay on track. Once you reach a milestone or successfully complete a specific objective, take the time to acknowledge and celebrate your achievement.
Read more about action check
brainly.com/question/30698367
#SPJ1
Which term best describes the output of the integer division operator?
Difference
Fraction
Quotient
Remainder
Sum
Answers
Answer: Quotient
Explanation:
Write a Java program which declares and populates an array with some values (at least 5 values). Then it should call a method passing it the array. The method should modify the array values using a loop. Lastly, after the program calls the method, it should display the modified array contents to the console.
Answers
Answer:
CODE IN JAVA :
import java.util.*;
public class Main
{
public static void modifyArray(int[] arr, int n){
for(int i = 0; i < n; i++){
arr[i] = -1; // each value is modified to -1
}
}
public static void main(String[] args) {
int n;
System.out.print("Enter size of array(atleast 5): ");
Scanner sc = new Scanner(System.in);
n = sc.nextInt();
int array[] = new int[n]; // array with size n declared
// populating the array
System.out.print("Enter array elements: ");
for(int i = 0; i < n; i++){
array[i] = sc.nextInt();
}
// modifying array via a function
modifyArray(array, n);
// printing array values after modifiction
System.out.print("Array after modification: ");
for(int i = 0; i < n; i++){
System.out.print(array[i] + " "); // space separated
}
}
}
Explanation:
7.6 lesson practice edhesive
Answers
Question 5: Which category best represents: a student has a friend who's
parent is a teacher at their school. The student uses his friend to obtain the
teachers username and password. Grades end up getting changed in the
digital grading system and it is soon discovered that the teacher also has the
same password in their family's online banking system.
A. illegal file sharing
B. software pirating
C. cyber bullying
D. identity theft
E. it's just not right or responsible.
Answers
Answer:
E
Explanation:
it's not right and it is also irresponsible and the teacher shouldn't have used that as her bank details and also that student's mother is Bankrupt by now
What are benefits of using AWS Organizations? (Choose two.) O Replaces existing AWS Identity and Access Management (IAM) policies with service control policies (SCPs), which are simpler to manageO Provides the ability to create groups of accounts and then attach policies to a group O Provides the ability to create an unlimited number of nested organizational units (OUs) to support your desired structure O Simplifies automating account creation and management by using APIsO Prevents any restrictions from being put on the root user that is associated with the main organization in an account
Answers
The benefits of using AWS Organizations are that it provides the ability to create groups of accounts and then attach policies to a group, and Simplifies automating account creation and management by using APIs. Thus, option 2nd and 4th are correct.
What are AWS Organizations?AWS Organizations is a service that allows you to merge numerous AWS accounts into a single organization that you establish and administer centrally. AWS Organizations features account administration and unified invoicing tools, allowing you to better meet the business's financial, security, and compliance requirements.
The advantages of utilizing AWS Organizations are that it allows you to build groups of accounts and then connect policies to them, and it simplifies account creation and maintenance by leveraging APIs. As a result, options 2nd and 4th are correct.
Learn more about AWS Organizations here:
https://brainly.com/question/30176139
#SPJ1
a) Show that ¬(p∨(¬p∧q)) and ¬p∧¬q are logically equivalent by using series of logical equivalence. (3 marks)
b) Determine whether (p∧q)→(p∨q) is a tautology. (4 marks)
c) With the aid of a truth table, convert the expression (¬p→q)∧(¬q∨r) into Disjunction Normal Form (DNF) (5 marks)
Answers
a) To show that ¬(p∨(¬p∧q)) and ¬p∧¬q are logically equivalent, we can use a series of logical equivalences:
¬(p∨(¬p∧q)) (De Morgan's Law)
≡ ¬p∧¬(¬p∧q) (De Morgan's Law)
≡ ¬p∧(p∨¬q) (Double Negation)
≡ (¬p∧p)∨(¬p∧¬q) (Distributive Law)
≡ False∨(¬p∧¬q) (Negation Law)
≡ ¬p∧¬q (Identity Law)
Therefore, ¬(p∨(¬p∧q)) and ¬p∧¬q are logically equivalent.
b) To determine whether (p∧q)→(p∨q) is a tautology, we can construct a truth table:
p | q | (p∧q) | (p∨q) | (p∧q)→(p∨q)
-----------------------------------
T | T | T | T | T
T | F | F | T | T
F | T | F | T | T
F | F | F | F | T
Since the last column of the truth table always evaluates to true, (p∧q)→(p∨q) is a tautology.
c) Truth table for the expression (¬p→q)∧(¬q∨r):
p | q | r | ¬p | ¬p→q | ¬q | ¬q∨r | (¬p→q)∧(¬q∨r)
--------------------------------------------------
T | T | T | F | T | F | T | T
T | T | F | F | T | F | F | F
T | F | T | F | F | T | T | F
T | F | F | F | F | T | T | F
F | T | T | T | T | F | T | T
F | T | F | T | T | F | F | F
F | F | T | T | T | T | T | T
F | F | F | T | T | T | T | T
Converting the truth table into Disjunction Normal Form (DNF):
(¬p∧¬q∧r)∨(¬p∧q∧¬r)∨(p∧¬q∧r)∨(p∧¬q∧¬r)∨(p∧q∧r)
Therefore, the expression (¬p→q)∧(¬q∨r) in Disjunction Normal Form (DNF) is (¬p∧¬q∧r)∨(¬p∧q∧¬r)∨(p∧¬q∧r)∨(p∧¬q∧¬r)∨(p∧q∧r).
To know more about DNF, visit
https://brainly.com/question/31326308
#SPJ11
Which ONE of the following fields can be edited by a user?
A ObjectID
B Shape Length
C Name
D FID
Answers
The field that can be edited by a user is option C: Name.
The Name field is typically used to store a descriptive label or identifier for an object. In many applications or systems, users have the ability to edit or update the Name field to provide a more meaningful or relevant name for an object. This allows users to customize the labels or identifiers associated with specific objects to better suit their needs or preferences.
Editing the Name field can be particularly useful when managing and organizing data. It enables users to assign names that are intuitive, and recognizable and helps facilitate efficient searching, sorting, or categorization of objects within a system.
Learn more about data management here:
https://brainly.com/question/30296990
#SPJ11
What is the difference between apple store and play store
Answers
You are configuring a new server for a client. The client has purchased five 1 TB hard drives and would like the server's storage system to provide redundancy and double fault tolerance. Which of the following configurations would BEST meet the client's requirements?
A. RAID 1
B. RAID 5
C. RAID 0
D. RAID 10
Answers
RAID 10 is the most suitable choice for the client's requirement of redundancy and double fault tolerance with five 1 TB hard drives.
The configuration that would BEST meet the client's requirements for redundancy and double fault tolerance with five 1 TB hard drives is RAID 10. RAID 10, also known as RAID 1+0, combines elements of both RAID 1 and RAID 0. It offers both redundancy and performance improvements. In RAID 10, the drives are mirrored in pairs, creating a RAID 1 (mirroring) configuration, and then these mirrored pairs are striped together in a RAID 0 (striping) configuration.With RAID 10, the client's data is mirrored across multiple drives, providing redundancy. If one drive fails, the mirrored drive ensures that the data is still accessible. Additionally, RAID 10 offers improved read and write performance due to the striping. On the other hand, let's consider the other options: RAID 1 only mirrors the drives, providing redundancy, but it does not offer striping or improved performance.
RAID 5 offers both striping and parity, providing redundancy and improved performance, but it can tolerate only a single drive failure, not a double fault. RAID 0 offers striping for improved performance, but it does not provide any redundancy or fault tolerance.
Learn more about tolerance here:
https://brainly.com/question/31855626
#SPJ11
Which data type can store decimal or fractional numbers?
A. boolean
B. Integer
C. Chat
D. Floating point
Answers
Answer:
♡ madeline here ♡
its a! have a great day
stay safe & be yourself
✧・゚: *✧・゚:・゚✧*:・゚✧・゚
Explanation:
Write method reverseString, which takes a string str and returns a new string with the characters in str in reverse order. For example, reverseString("ABCDE") should return "EDCBA".
Complete the reverseString method below by assigning the reversed string to result.
/** Takes a string str and returns a new string
* with the characters reversed.
*/
public static String reverseString(String str)
{
String result = "";
return result;
}
Answers
Answer:
The method written in Java is as follows:
public static String reverseString(String str){
String result = "";
int lentt = str.length();
char[] strArray = str.toCharArray();
for (int i = lentt - 1; i >= 0; i--)
result+=strArray[i];
return result;
}
Explanation:
This defines the method
public static String reverseString(String str){
This initializes the result of the reversed string to an empty string
String result = "";
This calculates the length of the string
int lentt = str.length();
This converts the string to a char array
char[] strArray = str.toCharArray();
This iterates through the char array
for (int i = lentt - 1; i >= 0; i--)
This gets the reversed string
result+=strArray[i];
This returns the reversed string
return result;
}
See attachment for full program that includes the main method
def reverseString(str):
y = str[::-1]
return y
print(reverseString("ABCDE"))
The code is written in python. A function name reverseString is declared. The function takes an argument str.
Then a variable named y is used to store the reverse of our argument string.
The keyword return is used to output the reversed string.
Finally, the function is called with a print statement.
The bolded portion of the code are keywords in python.
read more: https://brainly.com/question/15071835?referrer=searchResults

Bundlr is an example of gatekeeper technology.
Group startsTrue or False
Answers
Answer:
False
Explanation:
An online supermarket wants to update its item rates during the sales season. They want to show the earlier rates too but with a strikethrough effect so that the customer knows that the new rates are cheaper.
The ____ element gives a strikethrough appearance to the text.
Answers
Answer:
the <strike> element should do it
Explanation: