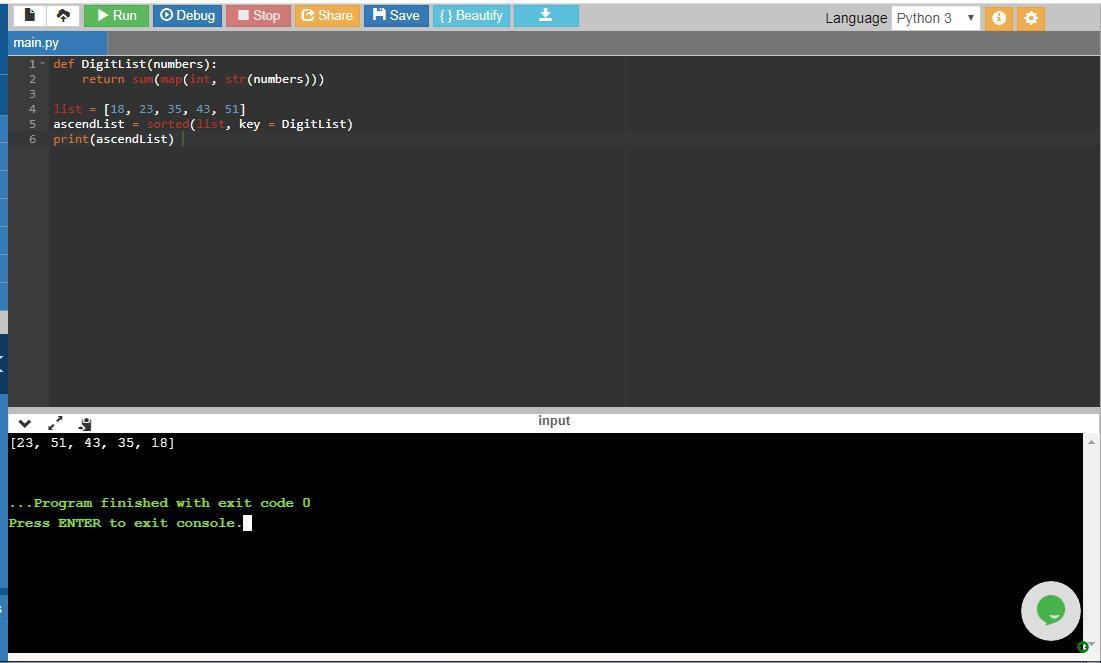
Write a program that displays the values in the list numbers in ascendingorder sorted by the sum of their digits.
Answers
Answer:
Here is the Python program.
def DigitList(number):
return sum(map(int, str(number)))
list = [18, 23, 35, 43, 51]
ascendList = sorted(list, key = DigitList)
print(ascendList)
Explanation:
The method DigitList() takes value of numbers of the list as parameter. So this parameter is basically the element of the list. return sum(map(int, str(number))) statement in the DigitList() method consists of three methods i.e. str(), map() and sum(). First the str() method converts each element of the list to string. Then the map() function is used which converts every element of list to another list. That list will now contain digits as its elements. In short each number is converted to the string by str() and then the digit characters of each string number is mapped to integers. Now these digits are passed to sum() function which returns the sum. For example we have two numbers 12 and 31 in the list so each digit is 1 2 and 3 1 are added to get the sum 3 and 4. So now the list would have 3 4 as elements.
Now list = [18, 23, 35, 43, 51] is a list of 5 numbers. ascendList = sorted(list, key = DigitList) statement has a sorted() method which takes two arguments i.e. the above list and a key which is equal to the DigitList which means that the list is sorted out using key=DigitList. DigitList simply converts each number of list to a another list with its digits as elements and then returns the sum of the digits. Now using DigitList method as key the element of the list = [18, 23, 35, 43, 51] are sorted using sorted() method. print(ascendList) statement prints the resultant list with values in the list in ascending order sorted by the sum of their digits.
So for the above list [18, 23, 35, 43, 51] the sum of each number is 9 ,5, 8, 7, 6 and then list is sorted according to the sum values in ascending order. So 5 is the smallest, then comes 6, 7, 8 and 9. So 5 is the sum of the number 23, 6 is the sum of 51, 7 is the sum of 43, 8 is the sum of 35 and 9 is the sum of 18. So now after sorting these numbers according to their sum the output list is:
[23, 51, 43, 35, 18]
Related Questions
You may review Chapter 2, pages 67-71 of the textbook or communication skills.
Now please answer the following questions:
• What communication systems do you believe are best to be used at a help desk?
• What may be a couple of reasons for the satisfaction disparity?
• How can you ensure that all employees are satisfied with the help desk's services regardless of how
Responses to Other Students: Respond to at least 2 of your fellow classmates with at least a 50-100-w
found to be compelling and enlightening. To help you with your discussion, please consider the following
• What differences or similarities do you see between your posting and other classmates' postings?
**
M
hp
Answers
Customer satisfaction is very important. A good insights as well as guidance in regards to the question are given below
What is the review?In terms of Communication systems that is made for a help desk: The right one to use in terms of communication systems for a help desk would is one that is based on the key needs as well as the need requirements of the firm and that of their customers.
Therefore, Reasons for satisfaction in terms of disparity are:
Inconsistent in terms of service qualityLack of available resourcesTraining as well as developmentLearn more about review from
https://brainly.com/question/25955478
#SPJ1
The implementation of mutex locks provided in Section 6.5 suffers from busy waiting. Describe what changes would be necessary so that a process waiting to acquire a mutex lock would be blocked and placed into a waiting queue until the lock became available.
Answers
The changes would be necessary so that a process waiting to acquire a mutex lock would be blocked and placed into a waiting queue is: Spinlocks.
What is spinlock?Spinlock can be defined as the process of enabling a thread to wait while looking for lock that are available.
Spinlock is important as it enable thread to partition processor based on their needs so as to make it possible for thread waiting for spinlock to make use of one processor while other threads can as well run on other processor without hindering or interrupting one another.
Inconclusion the changes would be necessary so that a process waiting to acquire a mutex lock is: Spinlocks.
Learn more about spinlock here:https://brainly.com/question/13766808
Write the necessary steps to compress the following IPv6 address and then put the Shortened version: (A)2001:0db8:0000:0000: 0000:0000:0000:0c50 (B) 2001:0db8:0000:0000: b450:0000:0000:00b4
Answers
The Ipv6 notation removes a field when there is just 0 (zero) available in it. When IPv6 address notation allows for continuous 0s (zeroes), all zeroes are changed to::.
What applications use IPv6?The Internet Research Task Force (IETF) developed IPv6, the most recent version of the internet protocol, which aids in localizing node systems on a network and directing web traffic while tackling the issue of IPv4 address exhaustion caused by widespread, prolonged internet use.
Which gadgets support IPv6?Cable internet providers (ISPs); IP-based home security systems; Blu-ray players, AV receivers, and television sets that can link to the Internet; Networked Home Electronics;
To know more about IPv6 visit:
https://brainly.com/question/15733937
#SPJ1
integrated circuits are made up of _____ and carry an electrical current
Answers
Answer:
integrated circuits are made up of Transistor and carry an electrical current
Falcon Waste Management purchased land and a warehouse for $740,000. In addition to the purchase price, Falcon made the following expenditures related to the acquisition: broker’s commission, $44,000; title insurance, $10,000; miscellaneous closing costs, $13,000. The warehouse was immediately demolished at a cost of $32,000 in anticipation of the building of a new warehouse. Determine the amounts Falcon should capitalize as the cost of the land and the building
Answers
8,07,000 is the total amount to be capitalized.
Explain about the capitalization?The term "capitalization" in finance refers to the entire debt and equity of a corporation, or its book value. The dollar value of a company's outstanding shares, or market capitalization, is determined by multiplying the current market price by the total number of existing shares.
Making the first letter of words' capital letters is the process of capitalization (an uppercase letter). The condition of being capitalized is another possible meaning. To uppercase the word polish, which is written with a lowercase p here, for instance, you would write Polish.
Capitalization is the combination of owner-owned and loaned funds. Therefore, it discloses the overall amount of money invested in a corporation. Share capital, loans, debentures, etc. Following are the standard categories for capitalization: standard capitalization
we must first total all of the expenses.
$7,40,000 for land and a warehouse
$44,000 in broker commission
$10,000 in title insurance
Added closing expenses $13000
=7,40,000 + 44,000 +10,000 +13000
=8,07,000
8,07,000 total cost to be capitalized
To learn more about capitalization refer to:
https://brainly.com/question/29099684
#SPJ1
How is blockchain different from traditional database models?
Blockchain can lead to increased transparency and trust in data, ultimately driving more innovation, improved productivity, and quality.
Blockchain prohibits transparency by redefining the fundamental nature of business ecosystems and business flows.
Blockchain provides multiple versions of the data that can be kept by individual entities.
Blockchain increases innovation; however, it decreases productivity and quality.
I don't know this yet.
Answers
The difference between blockchain and traditional database models is that: C. Blockchain provides multiple versions of the data that can be kept by individual entities.
What is a database?A database simply refers to an organized and structured collection of data that're stored on a computer system as a backup and they're usually accessed electronically.
What is a blockchain?A blockchain can be defined as a digital and dynamic financial system that is designed and developed to be used in recording and maintaining transactions that are associated with or made through the use of a bitcoin, usually as a database.
In this context, we can infer and logically deduce that unlike the traditional database models, blockchain is designed and developed to provide multiple versions of financial transactions (data), and they can also be kept by individual business entities.
Read more on blockchain here: brainly.com/question/25700270
#SPJ1
PLS HELP!! TAKINT TEST
A _____ is a network geographically confined to one building.
A) VPN
B) MAN
C) LAN
D) WAN
Answers
In a student scheduling program, a variable HasFreePeriod is set as True or False. This variable is an example of?
an abstract data type.
a user defined type.
an array.
a scalar
Answers
Answer: a user defined type
Explanation:
Answer:
Hi
Explanation:
The answer would be A User Defined Type
The one who answered before me is right as well
Select the correct text in the passage.
Which computer applications can Mr. Crowell use to make the classroom learning more stimulating and interesting?
Mr. Crowell has been teaching in a school for years with the help of traditional teaching methods. Recently, the school authorities have
recommended the use of computer programs and applications to facilitate a better learning experience for their students. Mr. Crowell wants to make
the classroom learning stimulating and interesting. He will have to use a few of the several computer applications available to him. These applications
include email, multimedia presentations, spreadsheets, word processing software] videos, and simulations,
rights reserved.
Reset
Next
Answers
The computer applications can Mr. Crowell use to make classroom learning more stimulating and interesting are:
b) Multimedia presentationsc) Spreadsheetsd) Word processing softwaref) SimulationsWhat are computer applications?Email, spreadsheets, and word processing software would not be good choices for him to utilize in his class as his pupils cannot interact with these tools. His major objective is to provide a better learning experience.
Mr. Crowell should think about adding multimedia presentations, movies, and simulations to augment his current teaching techniques since he wants to add more interesting computer applications to his classroom.
Therefore, the correct options are b, c, d, and f.
To learn more about computer applications, refer to the link:
https://brainly.com/question/8224724
#SPJ9
The question is incomplete. The missing options are given below:
Options:
-multimedia presentations
-spreadsheets
-word processing software
-videos
-simulation
Microwave transmits information between network nodes using
O satellite
O coaxial cables
towers
fiber optics
Answers
Answer:
Towers and satellite.
Explanation:
Electromagnetic waves is a propagating medium used in all communications device to transmit data (messages) from the device of the sender to the device of the receiver.
Generally, the most commonly used electromagnetic wave technology in telecommunications is radio waves.
Radio waves can be defined as an electromagnetic wave that has its frequency ranging from 30 GHz to 300 GHz and its wavelength between 1mm and 3000m. Therefore, radio waves are a series of repetitive valleys and peaks that are typically characterized of having the longest wavelength in the electromagnetic spectrum.
Basically, as a result of radio waves having long wavelengths, they are mainly used in long-distance communications such as the carriage and transmission of data.
The distance from one peak to the next peak is called wavelength. This distance is also equal to the distance from one trough of a wave to another.
Also, microwave is a form of radio waves which typically has short wavelengths and frequency ranging from 300 MHz and 300 GHz.
Hence, microwave transmits information between network nodes using towers and satellite.
Answer:
Towers and Satelite is the correct answer :D
To help insure that an HTML document renders well in many web browsers it is important to included which at top of file
Answers
Answer:
<!DOCTYPE html>
Explanation:
This tells the browseer that the code is HTML5 format
Which of the following is an example of an inline element? A. B. C. D.
Answers
What will be the different if the syringes and tube are filled with air instead of water?Explain your answer
Answers
Answer:
If the syringes and tubes are filled with air instead of water, the difference would be mainly due to the difference in the properties of air and water. Air is a compressible gas, while water is an incompressible liquid. This would result in a different behavior of the fluid when being pushed through the system.
When the syringe plunger is pushed to force air through the tube, the air molecules will begin to compress, decreasing the distance between them. This will cause an increase in pressure within the tube that can be measured using the pressure gauge. However, this pressure will not remain constant as the air continues to compress, making the measured pressure unreliable.
On the other hand, when the syringe plunger is pushed to force water through the tube, the water molecules will not compress. Therefore, the increase in pressure within the tube will be directly proportional to the force applied to the syringe plunger, resulting in an accurate measurement of pressure.
In summary, if the syringes and tube are filled with air instead of water, the difference would be that the measured pressure would not be reliable due to the compressibility of air.
consider a memory system with a memory access time of 150 ns and a cache access time of 20ns. If the effective access time is 20% greater than the cache access time, what is the hit ratio H g
Answers
Answer:
H = 0.7333333
Explanation:
Given that:
The memory access time (\(T_m\)) = 150 ns
The cache access time \((T_c)\) = 20 ns
Effective access time \((T_e)\) = 20% > \((T_c)\)
Then, it implies that:
= \((T_c)\) + 20% of
=\((T_c)\)(1+20%)
=\((T_c)\)(1+ 0.2)
= 20ns × 1.2
= 24ns
To determine the hit ratio H;
Using the formula:
\(T_e = T_c \times H+(1-H) \times (T_c + T_m) \\ \\ T_e = HT_c + T_c + T_m -HT_c -HT_m \\ \\ T_e = T_c +T_m - HT_m \\ \\ T_c -T_e = T_m (H-1) \\ \\ H-1 = \dfrac{T_c -T_e}{T_m} \\ \\ H = 1+ (\dfrac{T_c -T_e}{T_m})--- (1)\)
Replacing the values; we have:
\(T_c - T_e = 20ns - 24 ns \\ \\ T_c - T_e = -4 ns \\ \\ \dfrac{T_c - T_e }{T_m} = \dfrac{-4 ns}{150} \\ \\ \dfrac{T_c - T_e }{T_m} = -0.02666667\)
From (1)
\(H = 1+ (-0.2666667) \\ \\ H = 1 - 0.2666667 \\ \\ \mathbf{H = 0.7333333}\)
2. Which is not part of the Sans Institutes Audit process?
Help to translate the business needs into technical or operational needs.
O Deler a report.
O Define the audit scope and limitations.
O Feedback based on the
Answers
Answer:
Help to translate the business needs into technical or operational needs. This is not a part.
Explanation:
Capital budgeting simply refers to the process that is used by a business in order to determine the fixed asset purchases that is proposed which it should accept, or not. It's typically done in order to select the investment that's most profitable for a company.
Some of the capital budgeting processes include:
Identification and analysis of potential capital investments.
Application of capital rationing
Performing post-audits
It should be noted that developing short-term operating strategies is not part of the capital budgeting process.
Learn more about investments on:
https://brainly.com/question/15105766
#SPJ2
3.14.5 codehs write a program that asks a user for a radius value and then draws a blue circle inside a red square in the center of a canvas
Answers
The required program that asks a user for a radius value and then draws a blue circle inside a red square in the center of a canvas is given as follows:
import turtle
radius = float(input("Enter the radius value: "))
turtle.color("red")
turtle.begin_fill()
for _ in range(4):
turtle.forward(radius * 2)
turtle.right(90)
turtle.end_fill()
turtle.penup()
turtle.goto(0, -radius)
turtle.pendown()
turtle.color("blue")
turtle.begin_fill()
turtle.circle(radius)
turtle.end_fill()
turtle.hideturtle()
turtle.done()
The radius of a circle is always half the length of its diameter. If the diameter is 4 cm, then the radius is 4 cm 2 = 2 cm. The radius is r and the diameter is d in mathematical formulae.
The radius of a circle is the distance between its center and its perimeter (in other words, the radius is one-half of its diameter).
Learn mor eabout radius;
https://brainly.com/question/28162977
#SPJ1
The greater than sign(>) is an example of
Answers
Answer:
charactor
Explanation:
It's used in arythmetic calculation
Choosing ideas and developing them is done during which step of the writing process
Answers
Answer:
prewriting.
Explanation:
Decide on a topic to write about and Brainstorm ideas about the subject and how those ideas can be organized.
Brainly account. How to open?
Answers
Write a program that prompts a user to enter the number of elements to store in an array. Then prompt the user to enter all the numbers stored in the array.
The program should then cycle through the array to see if any numbers are divisible by 5. If any number is divisible by 5 print out which ones are and identify them in the output.
Answers
Answer:
Here's an example of a program that does what you've described:
# Get the number of elements in the array
n = int(input("Enter the number of elements to store in the array: "))
# Initialize the array
arr = []
# Get the elements of the array from the user
print("Enter the elements of the array:")
for i in range(n):
arr.append(int(input()))
# Print out which numbers are divisible by 5
print("The following numbers are divisible by 5:")
for i, x in enumerate(arr):
if x % 5 == 0:
print(f"{i}: {x}")
This program will first prompt the user to enter the number of elements in the array. It then initializes an empty array and prompts the user to enter each element of the array. Finally, it loops through the array and prints out the index and value of any element that is divisible by 5.
Explanation:
2 The following image shows the number of orders Company A received in 2015-2020. A financial analyst wants to calculate the year-over-year growth rate of the orders and has entered the formula for 2016 in cell C4. What steps should the analyst take to apply the same formula to all adjacent years using the Macabacus' Fast Fill Right shortcuts?
Answers
In the above case, the thing to do is to Press Ctrl + Shift + Right Arrow to select cells C4 to G4, then press Ctrl + R.
What are Computer shortcuts?A computer shortcuts are known to be a composition of one or a lot of keys that bring about a command in software or operating system.
Hence, In the above case, the thing to do is to Press Ctrl + Shift + Right Arrow to select cells C4 to G4, then press Ctrl + R.
See options below
Select cell C4, then press Ctrl + Shift + R
Press Ctrl + Shift + Right Arrow to select cells C4 to G4, then press Ctrl + R
Select cell C4, then press Ctrl + R
Press Shift + Right Arrow to select cells C4 to G4, then press Ctrl + R
Learn more about Computer shortcuts from
https://brainly.com/question/12531147
#SPJ1
Create a slideshow with six pictures and text. The slide is about of of the Tcp/Ip networking layers choose the transport internet or network access layer for your slides. Title slide: Give as a minimum, the name of the layer you are presenting and your own name. The main use of the layer: Give at least two examples of how the layer is used. Diagram: Include a diagram (using squares, inches and arrows, etc) showing the relationship between the 3nd points and intervening network at this layer. Protocols: Name and describe at least two Protocols used in this layer. Supporting Protocols: Name and describe at least two Protocols that support that Protocols in your layer. (if they are non explain why that is the case). Supported Protocols: Name and describe at least two Protocols supported by the Protocols in your layer. Help Asap
Answers
Layer: Transport Layer
Presenter: MyAI
Main use of the layer:
1. Provides end-to-end communication between applications on different hosts.
2. Segments and reassembles data into a data stream.
Diagram:
[Application Layer] - [Transport Layer] - [Internet Layer] - [Network Access Layer]
Protocols:
1. Transmission Control Protocol (TCP): A connection-oriented protocol that provides reliable, ordered, and error-checked delivery of data between applications.
2. User Datagram Protocol (UDP): A connectionless protocol that provides unreliable, unordered, and unchecked delivery of data between applications.
Supporting Protocols:
1. Internet Protocol (IP): Provides logical addressing and routing of data between hosts.
2. Address Resolution Protocol (ARP): Maps IP addresses to physical addresses.
Supported Protocols:
1. HTTP: Hypertext Transfer Protocol, used for transferring web pages.
2. FTP: File Transfer Protocol, used for transferring files between hosts.
Which character is used to create an absolute reference to a cell?
11
$
!
()
Answers
Answer:
$
Explanation:
your welcome
$ character is employed to create an absolute reference to a cell. Thus, option B ($) is correct.
What is a cell in excel?The grid-like elements in an Excel spreadsheet like this one are called cells. On a worksheet, each cell is identifiable by its citation, the column letter, and the set of rows that cross at the cell's position.
There are different position for different cells. and for referencing them There is a number as well as an alphabet that is present to characterize the cell.
When duplicating a formula from one cell to another in Excel, an absolute reference seems to be a cell reference where the column but also row coordinates remain constant. The coordinates are corrected by adding the dollar sign ($) before them. Therefore, option B is the correct option.
Learn more about cell in excel, here:
https://brainly.com/question/1380185
#SPJ6
Columns, margins and orientation can all be found on what tab
Answers
Answer:
The right answer is: Option C: Layout.
Explanation:
Columns are used to write text in a word document in more than one columns. Similarly, margins is the empty space that is left blank from all sides of the page. Orientation can be either landscape or portrait.
all these options are found in the Layout tab in MS word.
Hence,
The right answer is: Option C: Layout.
100 POINTS!!!
what kind of laptop is compatible with my pc lol i want to do a dual pc setup and my budget is $500.
PC specs:
AMD Ryzen 7 1700X Eight-Core Processor 3.40 GHz
16 GB DIMM 1400 MHz RAM
Radeon RX580 Series
Answers
Answer:
Hmm.. Try researching, I'm sure you'll find something there..
Your company has been assigned the 194.10.0.0/24 network for use at one of its sites. You need to calculate a subnet mask that will accommodate 60 hosts per subnet while maximizing the number of available subnets. What subnet mask will you use in CIDR notation?
Answers
To accommodate 60 hosts per subnet while maximizing the number of available subnets, we need to use a subnet mask that provides enough host bits and subnet bits.
How to calculateTo calculate the subnet mask, we determine the number of host bits required to accommodate 60 hosts: 2^6 = 64. Therefore, we need 6 host bits.
Subsequently, we determine the optimal quantity of subnet bits needed to increase the quantity of accessible subnets: the formula 2^n >= the amount of subnets is used. To account for multiple subnets, the value of n is set to 2, resulting in a total of 4 subnets.
Therefore, we need 2 subnet bits.
Combining the host bits (6) and subnet bits (2), we get a subnet mask of /28 in CIDR notation.
Read more about subnet mask here:
https://brainly.com/question/28390252
#SPJ1
Which term refers to a slide that is generated by PowerPoint and includes Zoom links to multiple sections within a presentation?
Answers
A "Section Expand" slide is a PowerPoint slide that has Magnification links to various presentation sections.
How are slide presentations created?Tap the Ribbon's Slide Show tab. Choose either From Slide or From Starting. The slide show button in the status bar or the F5 key on your keyboard can also be used to launch the presentation. Clicking the Options button will let you leave the presentation and go back to normal viewing.The presentation title and the complete name ought to be on the first slide. The audience can get ready for your speech by viewing it up until the start of the presentation.The opening establishes the overall tone of the presentation and provides information about what the audience should take away from it.To learn more about slide presentation, refer to:
https://brainly.com/question/23714390
Write a paragraph discussing privacy issues on the internet
and their impact on human lives.
Answers
Explanation:
internent had a impact on human lives because it is very popular and it brought in phones so about evrbody in the world has internent and it impacted work around the world and changed the world alot.
Additional rows and columns are inserted into a table using the
tab.
o Table Tools Design
o Insert Table
o Table Tools Layout
o Table Tools Insert
Answers
In JAVA with comments: Consider an array of integers. Write the pseudocode for either the selection sort, insertion sort, or bubble sort algorithm. Include loop invariants in your pseudocode.
Answers
Here's a Java pseudocode implementation of the selection sort algorithm with comments and loop invariants:
```java
// Selection Sort Algorithm
public void selectionSort(int[] arr) {
int n = arr.length;
for (int i = 0; i < n - 1; i++) {
int minIndex = i;
// Loop invariant: arr[minIndex] is the minimum element in arr[i..n-1]
for (int j = i + 1; j < n; j++) {
if (arr[j] < arr[minIndex]) {
minIndex = j;
}
}
// Swap the minimum element with the first element
int temp = arr[minIndex];
arr[minIndex] = arr[i];
arr[i] = temp;
}
}
```The selection sort algorithm repeatedly selects the minimum element from the unsorted part of the array and swaps it with the first element of the unsorted part.
The outer loop (line 6) iterates from the first element to the second-to-last element, while the inner loop (line 9) searches for the minimum element.
The loop invariant in line 10 states that `arr[minIndex]` is always the minimum element in the unsorted part of the array. After each iteration of the outer loop, the invariant is maintained.
The swap operation in lines 14-16 exchanges the minimum element with the first element of the unsorted part, effectively expanding the sorted portion of the array.
This process continues until the entire array is sorted.
Remember, this pseudocode can be directly translated into Java code, replacing the comments with the appropriate syntax.
For more such questions on pseudocode,click on
https://brainly.com/question/24953880
#SPJ8