Write a simplified machine language program that has register $s0 loop through the numbers 0, 100, 200, ..., 500. See Lab 11 for details on submitting the simplified machine language programs.
Answers
Answer:
Explanation:
li $s4 , 100 // Initialize register $s4 with 500 for checking the condition when $s0 is equal to 500
Loop : li $s0 , 0 // Initialize register $s0 with0
abc : addi $s0 , 100 // Add 100 to register $s0
bne $s0, $s4 , abc // Branch to label abc if not equal to 500
beq $s0, $s4 , Loop // Branch to label Loop if equal to 500
Related Questions
Where are the kidneys located?
a) Attached to the bladder
b) Lower back
c) Upper back
d) Middle back
e) Chest cavity
f the following is acian of health
Answers
Answer:
B
Explanation:
Your kidneys are fist-sized organs shaped like beans that are located at the back of the middle of your trunk, in the area called your flank. They are under the lower part of your ribcage on the right and left sides of your backbone.
what is computer virus
Answers
Answer:
A type of malicious code or program written to alter the way a computer operates and is designed to spread from one computer to another.
Once a virus has successfully attached to a program, file, or document, the virus will lie dormant until circumstances cause the computer or device to execute its code. In order for a virus to infect your computer, you have to run the infected program, which in turn causes the virus code to be executed.
Answer:
Computer virus :
In more technical terms, a computer virus is a type of malicious code or program written to alter the way a computer operates and is designed to spread from one computer to another. A virus operates by inserting or attaching itself to a legitimate program or document that supports macros in order to execute its code.
Help pls.
Write python 10 calculations using a variety of operations. Have a real-life purpose for each calculation.
First, use Pseudocode and then implement it in Python.
For example, one calculation could be determining the number of gallons of gas needed for a trip based on the miles per gallon consumed by a car.
Sample code in a program:
print("A field 30 feet wide and 40 feet long. Area (square feet): ", area)
Sample output:
A field 30 feet wide and 40 feet long. Area (square feet): 120
Answers
If we are to make a python program that would perform the calculation to determine the number of gallons of gas needed for a trip, this is given below:
The Programdef printWelcome():
print ('Welcome to the Miles per Gallon program')
def getMiles():
miles = float(input('Enter the miles you have drove: '))
return miles
def getGallons():
gallons = float(input('Enter the gallons of gas you used: '))
return gallons
def printMpg(milespergallon):
print ('Your MPG is: ', str(milespergallon))
def calcMpg(miles, gallons):
mpg = miles / gallons
return mpg
def rateMpg(mpg):
if mpg < 12:
print ("Poor mpg")
elif mpg < 19:
print ("Fair mpg")
elif mpg < 26:
print ("Good mpg")
else:
print ("Excellent mpg")
if __name__ == '__main__':
printWelcome()
print('\n')
miles = getMiles()
if miles <= 0:
print('The number of miles cannot be negative or zero. Enter a positive number')
miles = getMiles()
gallons = getGallons()
if gallons <= 0:
print('The gallons of gas used has to be positive')
gallons = getGallons()
print('\n')
mpg = calcMpg(miles, gallons)
printMpg(mpg)
print('\n')
rateMpg(mpg)
Read more about python programming here:
https://brainly.com/question/26497128
#SPJ1
what is this car first to awnser is the brianliest

Answers
Answer: Lamborghini
Explanation: Is it yours
Which of the following is the correct representation of -780,030,000 in exponential notation?
Answers
2.2 code practice question 1
Answers
Answer:
a = float(input("Enter an integer: "))
print(a + 1)
print (a + 2)
print (a + 3)
Explanation:
The epa requires spray guns used in the automotive refinishing process to have transfer efficiency of at least
Answers
The epa requires spray guns used in the automotive refinishing process to have transfer efficiency of at least 65 percent transfer efficiency.
What is the transfer efficiency
EPA lacks transfer efficiency requirement for auto refinishing spray guns. The EPA regulates auto refinishing emissions and impact with rules. NESHAP regulates paint stripping and coating operations for air pollutants.
This rule limits VOCs and HAPs emissions in automotive refinishing. When it comes to reducing overspray and minimizing wasted paint or coating material, transfer efficiency is crucial. "More efficiency, less waste with higher transfer rate."
Learn more about transfer efficiency from
https://brainly.com/question/29355652
#SPJ1
C++ Add each element in origList with the corresponding value in offsetAmount. Print each sum followed by a semicolon (no spaces).
Ex: If origList = {4, 5, 10, 12} and offsetAmount = {2, 4, 7, 3}, print:
6;9;17;15;
#include
#include
using namespace std;
int main() {
const int NUM_VALS = 4;
int origList[NUM_VALS];
int offsetAmount[NUM_VALS];
int i;
cin >> origList[0];
cin >> origList[1];
cin >> origList[2];
cin >> origList[3];
cin >> offsetAmount[0];
cin >> offsetAmount[1];
cin >> offsetAmount[2];
cin >> offsetAmount[3];
/* Your code goes here */
cout << endl;
return 0;
}
Answers
Answer:
here you go, if it helps ,do consider giving brainliest
Explanation:
#include<stdio.h>
int main(void)
{
const int NUM_VALS = 4;
int origList[4];
int offsetAmount[4];
int i = 0;
origList[0] = 40;
origList[1] = 50;
origList[2] = 60;
origList[3] = 70;
offsetAmount[0] = 5;
offsetAmount[1] = 7;
offsetAmount[2] = 3;
offsetAmount[3] = 0;
// Prints the Sum of each element in the origList
// with the corresponding value in the
// offsetAmount.
for (i = 0;i<NUM_VALS;i++)
{
origList[i] += offsetAmount[i];
printf("%d ", origList[i]);
}
printf("\n");
return 0;
}
In JAVA with comments: Consider an array of integers. Write the pseudocode for either the selection sort, insertion sort, or bubble sort algorithm. Include loop invariants in your pseudocode.
Answers
Here's a Java pseudocode implementation of the selection sort algorithm with comments and loop invariants:
```java
// Selection Sort Algorithm
public void selectionSort(int[] arr) {
int n = arr.length;
for (int i = 0; i < n - 1; i++) {
int minIndex = i;
// Loop invariant: arr[minIndex] is the minimum element in arr[i..n-1]
for (int j = i + 1; j < n; j++) {
if (arr[j] < arr[minIndex]) {
minIndex = j;
}
}
// Swap the minimum element with the first element
int temp = arr[minIndex];
arr[minIndex] = arr[i];
arr[i] = temp;
}
}
```The selection sort algorithm repeatedly selects the minimum element from the unsorted part of the array and swaps it with the first element of the unsorted part.
The outer loop (line 6) iterates from the first element to the second-to-last element, while the inner loop (line 9) searches for the minimum element.
The loop invariant in line 10 states that `arr[minIndex]` is always the minimum element in the unsorted part of the array. After each iteration of the outer loop, the invariant is maintained.
The swap operation in lines 14-16 exchanges the minimum element with the first element of the unsorted part, effectively expanding the sorted portion of the array.
This process continues until the entire array is sorted.
Remember, this pseudocode can be directly translated into Java code, replacing the comments with the appropriate syntax.
For more such questions on pseudocode,click on
https://brainly.com/question/24953880
#SPJ8
Code to be written in R language:
The Fibonacci numbers is a sequence of numbers {Fn} defined by the following recursive relationship:
Fn= Fn−1 + Fn−2, n > 3
with F1 = F2 = 1.
Write the code to determine the smallest n such
that Fn is larger than 5,000,000 (five million). Report the value of that Fn.
Answers
Here is the R code to determine the smallest n such that the Fibonacci number is larger than 5,000,000:
fib <- function(n) {
if (n <= 2) {
return(1)
} else {
return(fib(n - 1) + fib(n - 2))
}
}
n <- 3
while (fib(n) <= 5000000) {
n <- n + 1
}
fib_n <- fib(n)
cat("The smallest n such that Fibonacci number is larger than 5,000,000 is", n, "and the value of that Fibonacci number is", fib_n, "\n")
The output of this code will be:
The smallest n such that Fibonacci number is larger than 5,000,000 is 35 and the value of that Fibonacci number is 9227465.
Learn more about R language here: https://brainly.com/question/14522662
#SPJ1
In the Stop-and-Wait flow-control protocol, what best describes the sender’s (S) and receiver’s (R) respective window sizes?
Answers
Answer:
The answer is "For the stop and wait the value of S and R is equal to 1".
Explanation:
As we know that, the SR protocol is also known as the automatic repeat request (ARQ), this process allows the sender to sends a series of frames with window size, without waiting for the particular ACK of the recipient including with Go-Back-N ARQ. This process is mainly used in the data link layer, which uses the sliding window method for the reliable provisioning of data frames, that's why for the SR protocol the value of S =R and S> 1.5 reasons why application programs are temporarily stored in main memory
Answers
The reasons why application programs are temporarily stored in main memory are:
So that they CPU can have access to it easily. Because the main memory is one that is byte-addressable and it is one that CPU can use.Why does operating system application software kept in the memory of the computer?RAM (Random Access Memory) and other application programs are said to be kept there because:
So that one can easily have access to it.So it can quickly transmit or to reached by the device's processor. RAM is said to be main memory in a computer.Therefore, The reasons why application programs are temporarily stored in main memory are:
So that they CPU can have access to it easily. Because the main memory is one that is byte-addressable and it is one that CPU can use.Learn more about application programs from
https://brainly.com/question/1538272
#SPJ1
20 POINTS!!!!!!!!!! will give brainliest
A requirements document is created during the _____ phase of software development.
Coding
Planning
Release
Design
Answers
Answer:
Release
Explanation:
Founders Education
Suzanne is following a fad diet. She has started to experience low energy during her workouts, and on a recent trip to the doctor, she found out she has high cholesterol. Which fad diet is Suzanne most likely following?
Answers
Answer:
Hi mate....
Explanation:
This is ur answer....
--> Suzanne just facing low carbohydrates....
hope it helps you,
mark me as the brainliest pls....
Follow me!
Answer:
A.
low-carbohydrate
Explanation:
I have absolutely no idea what this is if anyone can help who’s into computer science pleasee
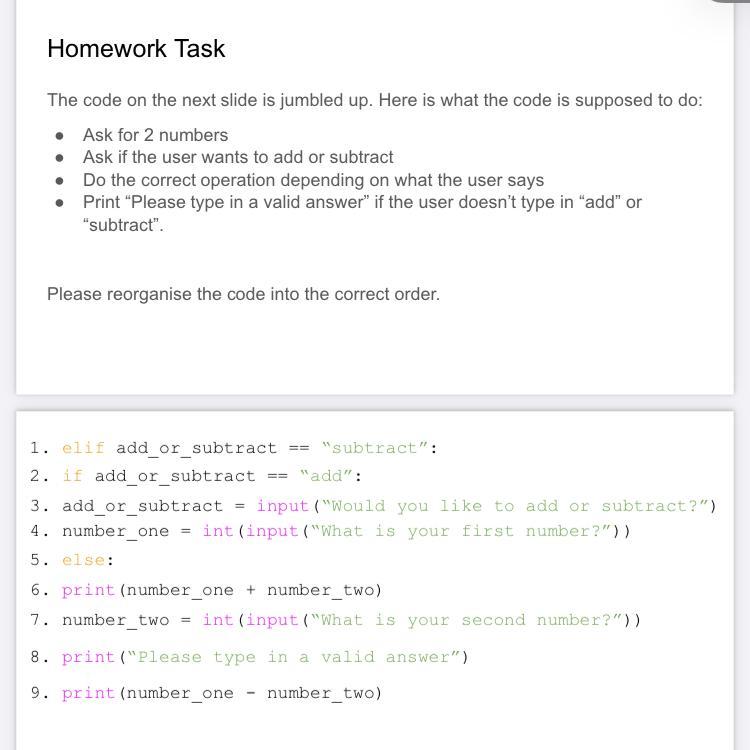
Answers
Answer:
Explanation:
It's code you have to put in the correct order so that the code can run correctly.
Move the code where its suppost to go to make it run
Which tool adds different amazing effects to a picture.
(a) Paint
(b) Lines tool
(c) Magic tool
Answers
Answer:
magic tool
Explanation:
The broadest search modifier is:
O NOT.
OOR.
ELSE.
AND.
What is the broadest search modifier?
Answers
Answer:
Image result for The broadest search modifier is: O NOT. OR. ELSE. AND. What is the broadest search modifier? Modified broad match: With modified broad match keywords, you choose specific keywords that are required for your ad to show, through the use of a plus sign. In other words, your ads will only show for queries that contain all of the words you precede with a plus sign in your keyword or phrase.
Which invention made it possible to have an entire computer for a single circuit board
Answers
Answer:
ok lang
Explanation:
User Interface Design ensures that the interface has elements that are easy to ________________. (Choose all that apply)
Question 1 options:
a) use to facilitate actions
b) change location
c) understand
d) remove
e) access
Answers
Answer:
A, C, D
Explanation:
User Interface (UI) Design focuses on anticipating what users might need to do and ensuring that the interface has elements that are easy to access, understand, and use to facilitate those actions.
Issues in plagiarism and copyright when blogging can be prevented. True or false
Answers
Answer:
It’s false
Explanation:
I can’t explain it’s too confusing
discuss seven multimedia keys
Answers
Answer:
Any seven multimedia keys are :-
□Special keys
□Alphabet keys
□Number keys
□Control keys
□Navigation keys
□Punctuation keys
□Symbol keys
An attack in which the attacker attempts to impersonate the user by using his or her session token is known as:
Answers
Answer:
Session hijacking
Explanation:
Session hijacking : Session hijacking is an attack where a user session is taken over by an attacker. A session starts when you log into a service, for example your banking application, and ends when you log out.
How do I make Karel slide
Answers
Answer:
1.3.4 Slide Karel
putBall();
move();
turnRight();
move();
putBall();
turnLeft();
move();
turnRight();
move();
putBall();
turnLeft();
function turnRight() {
turnLeft();
turnLeft();
turnLeft();
}
Explanation:
how to Write a simple Java socket programming that a client sends a text and server receives and print.
Answers
Answer:
Java Socket programming is used for communication between the applications running on different JRE.
Java Socket programming can be connection-oriented or connection-less.
Socket and ServerSocket classes are used for connection-oriented socket programming and DatagramSocket and DatagramPacket classes are used for connection-less socket programming.
The client in socket programming must know two information:
IP Address of Server, and
Port number.
Here, we are going to make one-way client and server communication. In this application, client sends a message to the server, server reads the message and prints it. Here, two classes are being used: Socket and ServerSocket. The Socket class is used to communicate client and server. Through this class, we can read and write message. The ServerSocket class is used at server-side. The accept() method of ServerSocket class blocks the console until the client is connected. After the successful connection of client, it returns the instance of Socket at server-side.
Explanation:
Creating Client:
import java.io.*;
import java.net.*;
public class MyServer {
public static void main(String[] args){
try{
ServerSocket ss=new ServerSocket(6666);
Socket s=ss.accept();//establishes connection.
DataInputStream dis=new DataInputStream(s.getInputStream());
Digital exclusion also known as the digital divide separates
Answers
The digital exclusion is being conceptualized as a state in which an individual is deprived of the use of information technologies, either due to insufficient means of access, lack of knowledge or lack of interest.
What are the main causes of the digital divide?Long-felt inequalities between the rich and entering the digital age tend to expand with the same and new technologies. Pierre Lévy, French philosopher, thinker of technology and society, stated that: “every new technology creates its excluded”.
The digital divide is a term that refers to the gap between demographics and regions that have access to modern information and communications technology (ICT), and those that don't or have restricted access. This technology can include the telephone, television, personal computers and internet connectivity.
See more about digital exclusion at brainly.com/question/14485114
#SPJ1
How many ads should be implemented per ad group?
A One or two
B Only one
C Three to five
D Two to three
Answers
Answer:
only one
Explanation:
because who likes ad
What feature allows a person to key on the new lines without tapping the return or enter key
Answers
The feature that allows a person to key on new lines without tapping the return or enter key is called word wrap
How to determine the featureWhen the current line is full with text, word wrap automatically shifts the pointer to a new line, removing the need to manually press the return or enter key.
In apps like word processors, text editors, and messaging services, it makes sure that text flows naturally within the available space.
This function allows for continued typing without the interruption of line breaks, which is very helpful when writing large paragraphs or dealing with a little amount of screen space.
Learn more about word wrap at: https://brainly.com/question/26721412
#SPJ1
wap to find to sum the digits of a positive integer which is 5 digits long.
Answers
Answer:
Explanation:
#include
int main()
{
int n, sum = 0;
printf("Enter a five digit number: ");
scanf("%d", &n);
while (n != 0) {
sum = sum + n % 10;
// removing last digit from number
n /= 10;
}
printf("Sum of digits: %d",sum);
return 0;
}
Which of these ports listed is the fastest? IEEE 1394 USB2.0 FIREWIRE ESATA
Answers
The port which is the fastest is ESATA.
What is ESATA?eSATA can be described as the SATA connector which can be access from outside the computer and it help to give the necessary signal connection that is needed for external storage devices.
The eSATA serves as a version of the eSATA port which is been regarded as the External SATA port, therefore, The port which is the fastest is ESATA.
Read more on the port here:
https://brainly.com/question/16397886
#SPJ1
20 POINTS!!!!!!! Which is considered a collection of code that can be run?
Answers
a computer program is a collection of instructions that can be executed by a computer to perform a specific task. A computer program is usually written by a computer programmer in a programming language.
Answer:
PROGRAM
Explanation:
I went and looked it up in my lesson, and I got it correct!!
Hope This Helped! :)