You are calculating commissions for sales staff at work. Employees receive ten dollars for every item sold. Your boss also wants to know the grand total paid to all employees as commission. How would you set this up in an Excel workbook and would you use absolute references, relative references, or both?
Answers
Answer:
To find the grand total paid to all employees as commission, we note the following;
The amount received by employees as commission for each item sold, r = $10.00
The information the boss wants to know = The grand total paid to all employees as commission
Let 'n' represent the the total sales, we have;
The grand total commission = Total sales × Commission
1) On MS Excel, four columns are created, labelled, Serial number, Employee Name, Number of Items Sold, Commission
2) In the second row, in the cell under the Commission column heading, Input the formula '=(Cell reference of adjacent Number of Items Sold) × 10' in the cell
3) Copy the the above formula to all the cells in the Commission column by clicking on the cell containing the formula, moving the mouse to the bottom right corner of the cell, and when the mouse pointer changes to a cross sign, left click and hold and drag to all the cells in the column
4) Input the formula =SUM(Argument) in the blank cell below the created Commission list
Where;
Argument = The reference to the range of cells containing the values in the Commission column
5) The output of the =SUM formula is the grand total paid to employees as commission
Explanation:
Related Questions
Good HTML skills will be required in order to prevent what from happening in the design of a web page?
Answers
Answer:
to properly use the tags in the web page
Explanation:
The full form HTML is Hyper Text Mark up Language. HTML is used in designing a good web page in the computer. It is used to design the document that are displayed in the web browser.
Instead of using a programming language to do the functions of a web page, the markup language uses the tags to identify the different types of the contents and purposes that they serve in the web page. A good HTML skills are required to prevent the web page from any improper designing of the contents in the web page.
true or false: erosion takes very long to happen.
Answers
Answer:
True
Explanation:
By definition, erosion is the gradual destruction or diminution of something.
1) Erosion can take many forms
2) The 3 main types of erosion are water, wind, and ice
3) The process of erosion can take up to thousands of years
4) Erosion affects humans because it creates dust that pollutes the air and on average carries around 20 different diseases including anthrax and tuberculosis
this text command defines how text will appear
Answers
In programming, the text command is not a specific command, but rather a term used to refer to a wide range of commands and functions that manipulate or display text.
What is a text command?Text commands may include functions for formatting, searching, replacing, and displaying text within a program or on a screen. These commands may be used in a variety of programming languages, including C, as you mentioned.
In C, for example, there are many standard library functions that can be used to work with text. Some of the most commonly used functions for working with text in C include:
printf(): used to display formatted text on the screen or in a file
scanf(): used to read formatted text from the keyboard or a file
strcpy(): used to copy one string of text to another
strcmp(): used to compare two strings of text to determine if they are equal
strlen(): used to determine the length of a string of text
Overall, text commands are a crucial part of programming and are used extensively in applications that involve working with text data.
Learn more about text on:
https://brainly.com/question/20169296
#SPJ1
What two states do binary numbers represent?
A) Coder and processor
B) Input and output
C) On and off
D) Right and left
Answers
Answer:
C
Explanation:
Binary is a base-2 number system that uses two mutually exclusive states to represent information. A binary number is made up of elements called bits where each bit can be in one of the two possible states. Generally, we represent them with the numerals 1 and 0.
Answer:
C
Explanation:
On and off symbolize 0 and 1.
An administrator at ursa major solar is using sharing rules to grant record access to users. which two types of record access can the administrator grant?
Answers
Based on the above, The two types of record access can the administrator grant are:
C. Read/Write
D. Read Only
What is read write access?This is seen as a kind of device that can both act as a kind of input and output or moves and receive.
The read-only access in computing is known to be the permission that is given to a user to be able to access files or directories and it is one where the user is only given the right to read or view, and not to make any changes.
Note that it is also seen as digital file that can be updated and deleted and therefore, Based on the above, The two types of record access can the administrator grant are:
C. Read/Write
D. Read Only
Learn more about record access from
https://brainly.com/question/8798580
#SPJ1
(a) what is the probability of drawing a vowel (a,e,i,o,u) and a consonant in either order? (b) write a matlab / python program to verify your answer in part (a). that is, randomly draw two letters without replacement and check whether one is a vowel and the other is a consonant. compute the probability by repeating the experiment for 10000 times.
Answers
Probability of drawing a vowel and a consonant in either order is 0.3230
So
Probability(Vowel) = probability of getting a vowel = 5/26
Probability(Consonant) = probability of getting a Consonant = 21/26
So,
1) prob_true = 0.3230
2) Smallest estimated Value of 1000 for error < 5 percent is N = 1000
3)
MATLAB code:
% a = 1, e=5 ,i=9 ,o=15 ,u =21
%vowels = [1,5,9,15,21];
Nset = round(logspace(2,5,100));
tmp = 1;
for x = 1:size(Nset,2)
n = Nset(x);
outcomes = 0;
for i = 1:n
r1 = randi([1 26],1,1);
r2 = randi([1 25],1,1);
if(r2 >= r1)
r2 = r2 + 1;
end
if((r1 == 1) | (r1 == 5) | (r1 == 9) | (r1 == 15) | (r1 == 21))
if((r2 ~= 1) & (r2 ~= 5) & (r2 ~= 9) & (r2 ~= 15) & (r2 ~= 21))
outcomes = outcomes + 1;
end
else
if((r2 == 1) | (r2 == 5) | (r2 == 9) | (r2 == 15) | (r2 == 21))
outcomes = outcomes + 1;
end
end
end
prob_est(x) = outcomes/n;
prob_true(x) = 2*((5*21)/(26*25));
error = ( abs((outcomes/n) - 2*((5*21)/(26*25)) ) / (2*((5*21)/(26*25))) )*100;
if(error< 5.0 & tmp == 1)
fprintf('smallest Value of N for error < 5 percent is N = %i\n',n);
tmp = 0;
end
end
plo
t(Nset,prob_est);
xlabel('Number of experiments');
ylabel('Probability of Coming A consonant and a Vowel');
hold on
plot(Nset,prob_true);
hold on
plot(Nset,prob_true + std(prob_est)./sqrt(Nset))
hold on
plot(Nset,prob_true - std(prob_est)./sqrt(Nset))
legend('Experimental probability','True Probability','prob_true + std(prob_est)./sqrt(Nset)', 'prob_true - std(prob_est)./sqrt(Nset)');
Know more about MATLAB,
https://brainly.com/question/30763780
#SPJ4
What is the default file setting for quick export with transparency?.
Answers
Answer:
Go to Edit > Preferences > Export. Select File > Export > Export Preferences.
the configuration will be Edit > Preferences > Export. Select File > Export > Export Preferences in photoshop.
what is photoshop ?Photoshop is a graphic editor software developed by Adobe Incorporation popular software and used in any industries in editing digital art and raster graphics now a days.
several color compositions like CMYK, RGB, CIELAB, duotone can be supported by this software which involve in conversion and change of the color values of the graphics.
There are multiple number of application of Photoshop which show many benefits like the versatility to mix and mix picture content and textual content, create a content effect, shadows, textures, and embosses, manipulation of images in creative ways and re-create images
Photoshop can Correct color, Reduce red eye, Add borders, Change to grayscale, Work with layers
For more details regarding photoshop, visit
brainly.com/question/15385979
#SPJ2
which statement made by a teacher is most likely to activate stereotype threat?
Answers
A statement made by a teacher that highlights a stereotype or implies a negative stereotype about a particular group is most likely to activate stereotype threat.
Stereotype threat refers to the concern or anxiety an individual experiences when they believe they may confirm a negative stereotype about their own social group. This can negatively impact their performance and lead to underperformance compared to their actual abilities.
A statement made by a teacher that emphasizes a negative stereotype about a particular group, such as "Girls aren't as good at math as boys," is most likely to activate stereotype threat.
This can make students from that group feel anxious and perform worse on academic tasks due to the fear of confirming the negative stereotype.
These statements, directly or indirectly, reinforce stereotypes and create a psychological pressure for individuals to prove themselves in line with those stereotypes. Such statements can undermine confidence and hinder performance due to the fear of confirming the stereotype.
To learn more about Stereotype: https://brainly.com/question/361502
#SPJ11
Tormund wants to build a proxy firewall for his two computers, A and B. How can he build it?
A.
by connecting computer A with computer B and computer B to the proxy firewall
B.
by connecting a different firewall to each computer
C.
by connecting computer A to computer B through the proxy firewall
D.
by connecting only one of the computers to the firewall
Answers
Answer:
b
Explanation:
what statement is correct on the sequential search algorithm? group of answer choices best case: when the first element in the array happens to be the search k best case: search key k exists in the middle of the given array worst case: search key k exists in the middle of the given array worst case: search key k disappears from the given array
Answers
The optimal situation for sequential search is that it performs one comparison and immediately matches X. In the worst-case scenario, sequential search performs n evaluations and either fits the last object in the list or does not.
What is the optimal sequential search time difficulty case?Thus, we can calculate the running time of this method by tallying the number of comparisons it performs given an n-dimensional array. If the first member of the list is the goal, sequential search works best. In this instance, only one comparison is required to yield the successful search.
The linear search algorithm is also known as the consecutive search algorithm. It is the most basic search method. Linear search merely traverses the list and matches each part with the object whose location is to be located.
Learn more about array from here;
https://brainly.com/question/19570024
#SPJ4
Which excel feature makes it easy to copy and paste formulas in multiple cells?.
Answers
Answer:
Ctrl + R - Copy a formula from the cell to the left and adjusts the cell references. For example, if you have a formula in cell A2 and you want to copy it to cell B2, select B2 and press Ctrl + R. Tip. Both of the above shortcuts can be used to copy formulas to multiple cells too.
Explanation:
A video project needs to be encrypted as it is going from a source to a destination. What can be added to the video
Answers
Answer:
A video encoder
Explanation:
an encoder is used to make a video encrypted so nobody can take your copy it. For instance You Tube uses an encoder
Which HTML tag is formatted correctly?
NEED ANSWER ASAP PLZ HELP ME IDONT UNDERETAND IT
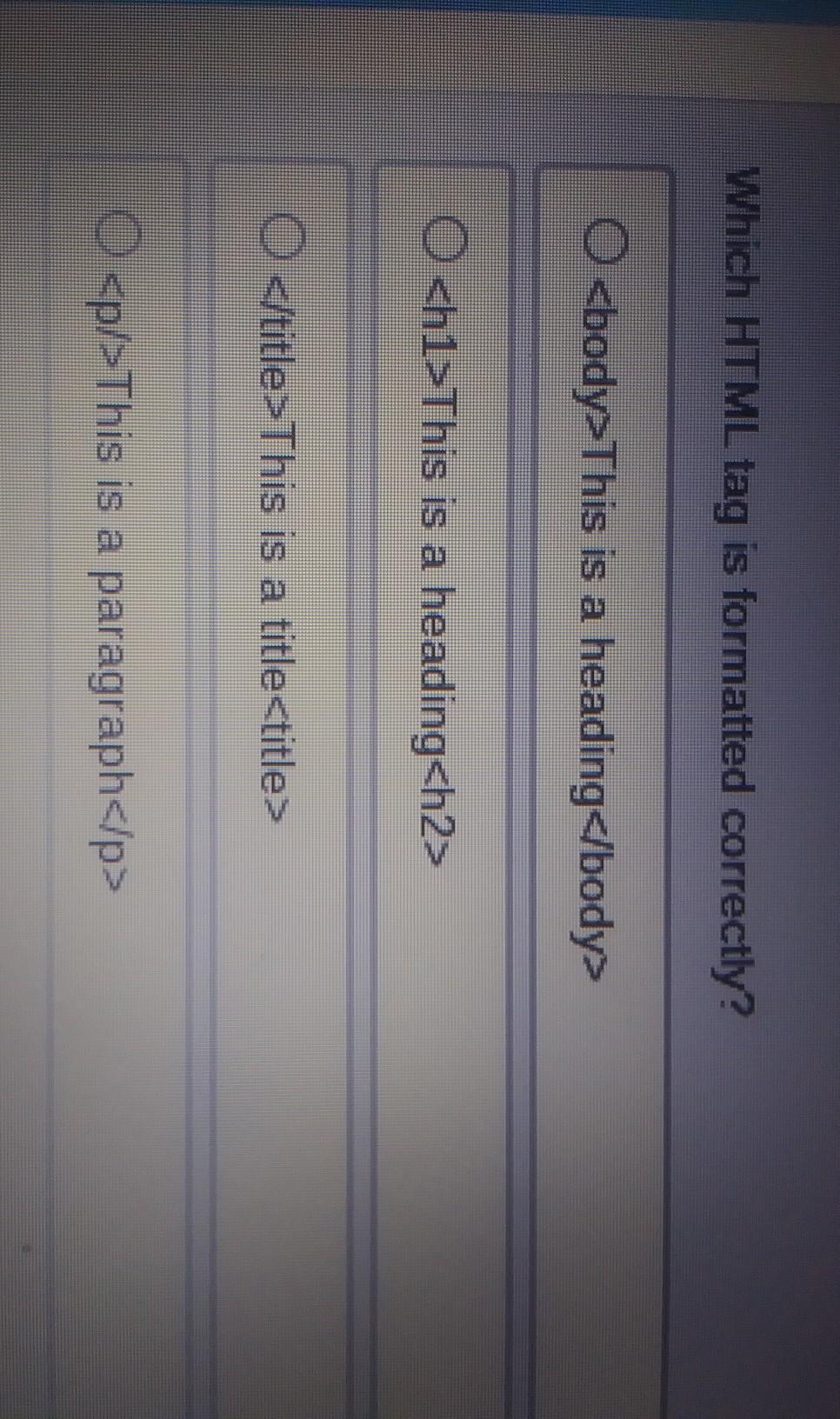
Answers
I think the last one is the correct one
Answer:
D
Explanation:
All others don't work
List three ideas for checking in with your progress and recognizing completion on your actions.
Answers
One idea for checking in with your progress and recognizing completion on your action is to set specific milestones or targets along the way and regularly evaluate your progress towards them.
How can you effectively track your progress and acknowledge completion of your action?To effectively track your progress and acknowledge completion of your action, it is important to establish clear milestones or targets that can serve as checkpoints. Break down your overall goal into smaller, measurable objectives that can be achieved incrementally.
Regularly assess your progress by comparing your actual achievements against these milestones. This will provide you with a tangible way to track your advancement and ensure that you stay on track. Once you reach a milestone or successfully complete a specific objective, take the time to acknowledge and celebrate your achievement.
Read more about action check
brainly.com/question/30698367
#SPJ1
Which of the following statements are true about cross-platform development? Select 3 options.
Hybrid apps are cross-platform and provide access to many hardware features.
Web apps are not cross-platform, unless they are being run on a smartphone.
Native apps are cross-platform applications, where one version of the app runs on all devices.
Application programming interfaces are often used to make cross-platform development easier.
Cross-platform development allows programmers to create one version of an app that runs on many
different platforms.
Answers
Answer:
- Application programming interfaces are often used to make cross-platform development easier.
-Hybrid apps are cross-platform and provide access to many hardware features.
-Cross-platform development allows programmers to create one version of an app that runs on many different platforms.
Explanation:
The statements that are correct about "cross-development platform" would be:
A). Hybrid apps are cross-platform and provide access to many hardware features.
D). Application programming interfaces are often used to make cross-platform development easier.
E). Cross-platform development allows programmers to create one version of an app that runs on many different platforms.
What is a cross-development platform?The Cross-Development platform is described as the process of development of application software that carries the ability to function on various operating systems.
The above statements correctly state that these applications offer access to multiple characteristics of the hardware and work on a number of platforms.
The applications are prepared to allow its access on distinct devices and it helps in making on the application that will work on all platforms.
Thus, options A, D, and E are the correct answers.
Learn more about "Development" here:
brainly.com/question/752980
What is Hypertext Transfer Protocol?
Answers
Answer:
an application layer protocol for distributed, collaborative, hypermedia information systems.
Explanation:
Click on the arrow in A. What will enable you to do?
Answers
Answer:
We need a picture
Explanation:
Express the following numbers in decimal: (a) * (10110. 0101) 2 (b) * (16. 5) 16 (c) * (26. 24) 8 (d) (dada. B) 16 (e) (1010. 1101) 2
Answers
Answer:
(a) To convert from binary to decimal, we can use the formula:
decimal = a_0 * 2^0 + a_1 * 2^1 + a_2 * 2^2 + ... + a_n * 2^n
where a_i is the i-th digit of the binary number.
Using this formula, we can convert (10110.0101)2 to decimal as follows:
(10110.0101)2 = 1 * 2^4 + 0 * 2^3 + 1 * 2^2 + 1 * 2^1 + 0 * 2^0 + 0 * 2^-1 + 1 * 2^-2 + 0 * 2^-3 + 1 * 2^-4
= 22.3125
Therefore, (10110.0101)2 = 22.3125 in decimal.
(b) To convert from hexadecimal to decimal, we can use the formula:
decimal = a_0 * 16^0 + a_1 * 16^1 + a_2 * 16^2 + ... + a_n * 16^n
where a_i is the i-th digit of the hexadecimal number.
Using this formula, we can convert (16.5)16 to decimal as follows:
(16.5)16 = 1 * 16^1 + 6 * 16^0 + 5 * 16^-1
= 22.5
Therefore, (16.5)16 = 22.5 in decimal.
(c) To convert from octal to decimal, we can use the formula:
decimal = a_0 * 8^0 + a_1 * 8^1 + a_2 * 8^2 + ... + a_n * 8^n
where a_i is the i-th digit of the octal number.
Using this formula, we can convert (26.24)8 to decimal as follows:
(26.24)8 = 2 * 8^1 + 6 * 8^0 + 2 * 8^-1 + 4 * 8^-2
= 22.375
Therefore, (26.24)8 = 22.375 in decimal.
(d) To convert from hexadecimal to decimal, we can use the formula:
decimal = a_0 * 16^0 + a_1 * 16
^1 + a_2 * 16^2 + ... + a_n * 16^n
where a_i is the i-th digit of the hexadecimal number.
Using this formula, we can convert (dada.B)16 to decimal as follows:
(dada.B)16 = 13 * 16^3 + 10 * 16^2 + 13 * 16^1 + 10 * 16^0 + 11 * 16^-1
= 56090.6875
Therefore, (dada.B)16 = 56090.6875 in decimal.
(e) To convert from binary to decimal, we can use the formula:
decimal = a_0 * 2^0 + a_1 * 2^1 + a_2 * 2^2 + ... + a_n * 2^n
where a_i is the i-th digit of the binary number.
Using this formula, we can convert (1010.1101)2 to decimal as follows:
(1010.1101)2 = 1 * 2^3 + 0 * 2^2 + 1 * 2^1 + 0 * 2^0 + 1 * 2^-1 + 1 * 2^-3
= 10.8125
Therefore, (1010.1101)2 = 10.8125 in decimal.
Why do companies collect information about consumers? A. Because they want to meet new friends on social networks B. Because they take consumers' best interests to heart C. Because they want to effectively advertise to consumers D. Because they are looking for good employees to hire
Answers
Answer:
C. Because they want to effectively advertise to consumers.
Explanation:
Companies collect info for more accurate advertisements, which are designed to make people interact with them more commonly.
"IBM should collect data on which computer parts are fixed most
frequently? What could it do with this data?
Answers
Collecting data on frequently repaired computer parts allows IBM to improve product design and quality, optimize inventory management, and enhance customer support and service.
1. Improve product design and quality: By identifying the parts that require frequent repairs, IBM can focus on enhancing the design, durability, and reliability of those components. This can lead to the development of more robust and long-lasting computer systems, reducing the need for repairs in the future.
2. Optimize inventory and supply chain management: By analyzing the frequency of repairs for different parts, IBM can make informed decisions about inventory management. They can ensure an adequate stock of frequently repaired parts to minimize downtime for customers and streamline their supply chain by prioritizing the procurement and distribution of these components.
3. Enhance customer support and service: IBM can leverage this data to improve their customer support and service offerings. They can allocate resources and train their support staff to handle common repairs efficiently. Additionally, they can proactively address issues by providing customers with troubleshooting guides, self-service options, or proactive replacement programs for parts prone to frequent failures.
Learn more about IBM here:
https://brainly.com/question/17156383
#SPJ11
what would be a reason for a computer user to use the task manager performance tab?
Answers
A computer user may want to use the task manager performance tab to monitor the overall health of their computer's hardware and software. The performance tab displays real-time data on CPU usage, memory usage, and disk activity, which can help users identify any processes or applications that are causing their system to slow down or become unresponsive. By using the performance tab, users can also determine if they need to upgrade their hardware or optimize their software settings to improve their computer's performance.
Monitoring system resource utilization: The Performance tab in Task Manager provides real-time information about the usage of system resources such as CPU, memory, disk, and network. Users can use it to monitor the performance of their computer and identify any potential resource bottlenecks or spikes in resource usage.
Troubleshooting performance issues: If a computer is running slowly or experiencing performance issues, the Performance tab can help users identify which resource (e.g., CPU, memory, disk) is being heavily utilized and causing the performance problem. This information can aid in troubleshooting and identifying the root cause of the performance issue.
Optimizing resource usage: The Performance tab can also help users identify processes or applications that are consuming excessive system resources, allowing them to take appropriate actions to optimize resource usage. For example, users can identify and close unnecessary applications or processes that are consuming excessive CPU or memory, which can help improve overall system performance.
Monitoring performance during resource-intensive tasks: When performing resource-intensive tasks such as video editing, gaming, or running virtual machines, users can use the Performance tab to monitor the system's resource utilization in real-time. This can help users ensure that their computer has enough resources available to handle the task efficiently and prevent performance degradation.
Overall, the Task Manager Performance tab is a valuable tool for monitoring and troubleshooting system performance, optimizing resource usage, and identifying performance issues on a Windows computer.
learn more about Task Manager here:
https://brainly.com/question/30398635
#SPJ11
1.Analyze some basic performance indicators of BIDVMETLIFE
2. Analyze bidvmetlife's swot
3. Some recommendations and asolutions to improve the current situation of bidvmetlife
Answers
1. Basic performance indicators: Premium growth, loss ratio, combined ratio, ROE, persistency ratio. 2. SWOT analysis: Strengths, weaknesses, opportunities, threats of BIDVMETLIFE. 3. Recommendations: Enhance digital capabilities, diversify products, improve customer retention, and talent development.
1. Analyzing basic performance indicators: Key performance indicators for BIDVMETLIFE would typically include premium growth rate, loss ratio, combined ratio, return on equity (ROE), and persistency ratio. These indicators provide insights into the company's growth, underwriting efficiency, profitability, and customer retention.
2. Analyzing BIDVMETLIFE's SWOT: Conducting a SWOT analysis for BIDVMETLIFE involves evaluating its strengths (such as brand reputation and distribution network), weaknesses (such as outdated technology or limited product offerings), opportunities (such as emerging markets or technological advancements), and threats (such as regulatory changes or intense competition).
3. Recommendations and solutions: To improve BIDVMETLIFE's current situation, potential recommendations could include enhancing digital capabilities to improve customer experience, diversifying the product portfolio to meet evolving customer needs, implementing customer retention strategies, and investing in talent development to attract and retain skilled professionals in the industry.
Learn more about SWOT analysis here:
https://brainly.com/question/32996259
#SPJ11
Give examples of hardware
Answers
Answer:
monitor
keyboard
mouse
CPU
UPS
printer
Scanner
and many more
Explanation:
hope it will help you
brainliest plz
Which set of keys is your right pointer finger responsible for typing (3 points)
a
3, E, D, and C
b
4, R, F, and V
c
5, T, G, and B
d
6, Y, H, and N

Answers
Answer:
D
Explanation:
Your right pointer finger is responsible for typing the Y, H, and N keys
Answer:
D
Explanation:
When typing, you rest your right pointer finger on the J key.
Most people are able to find this key without looking due to a small bump on the lower half of it.
Having your finger rest here allows for your hands to each take up roughly one half of the keyboard.
Your right pointer finger is responsible for typing the 6, Y, H, and N keys due to its positioning on the keyboard.
In what situations other than developing software might the process of analysis, design, development, test, deployment, and maintenance be a useful approach to problem solving?
Answers
In Systems development or traditional waterfall approach will the process of analysis, design, development, test, deployment, and maintenance be a useful approach.
What is software development?Software development is known to be a term that connote the composition of computer science works made for the process of developing , designing, and aiding software.
Note that In Systems development or traditional waterfall approach will the process of analysis, design, development, test, deployment, and maintenance be a useful approach. as it also uses the dteps listed above.
Learn more about software from
https://brainly.com/question/1538272
#SPJ1
What finger should be on the K key?
1. Pinky
2. Index
3. Middle
4. Ring
Answers
Answer:
The answer would be the middle
Explanation:
Hope this helps
Answer:
index has wonrg hahahahahh
Explanation:
Please answer quick:))))

Answers
Ok so.. I wanna know ur guys go-to coor and hat for Among Us (mines purple with the ninja band)
Answers
mine is lime and ninja band look at us we twins<3
How can you tell if a website is credible?
a. Anything on the web is automatically credible
b. You must review aspects of the site such as the author’s credibility
c. If it has a top-level domain of .com, it is credible
d. All of the above
Answers
Answer:
b
Explanation:
you must review everything, creditability , certificates, domains, etc
45 POINTS!!!!!!!!!!!PLZ HELP ME!!!!!!!!!!Select the correct answer. Which statement describes a characteristic of dynamic websites? A. They can be developed quickly. B. They are not functional. C. They are less flexible than static websites. D. They have content that is constantly updated. E. They are less expensive to host than static websites.
Answers
Answer:
D
Explanation:
Because anyone can update dynamic websites at any time, these are more functional and flexible. Therefore, content on dynamic websites keeps changing. Diverse content encourages users to return to these websites. The disadvantages of dynamic websites are that they are more expensive and take longer to develop than static websites. Hosting dynamic websites also costs more.
Answer:
D
Explanation: