You are tasked with designing the following 3bit counter using D flip flops. If the current state is represented as A B C, what are the simplified equations for each of the next state representations shown as AP BP CP?
The number sequence is : 0 - 1 - 2 - 4 - 3 - 5 - 7 - 6 - 0
Answers
In the given 3-bit counter, the next state of A, B, and C (represented as A', B', and C') depends on the current state ABC.
The sequence is 0-1-2-4-3-5-7-6 (in binary: 000, 001, 010, 100, 011, 101, 111, 110).
The simplified next state equations for D flip-flops are:
A' = A ⊕ B ⊕ C
B' = A · B ⊕ A · C ⊕ B · C
C' = A · B · C
This counter follows the mentioned sequence and recycles back to 0 after reaching the state 6 (110). These equations can be implemented using XOR and AND gates connected to D flip-flops.
Read more about XOR and AND gates here:
https://brainly.com/question/30890234
#SPJ1
Related Questions
what does it mean if you get the brainlyest ?and why does everyone want it so bad? and how do i give it to someone?
Answers
people mark the people who answered their question probably because they were asked to or their answer was what they were looking for and it helped them. and i don't know why people want it so bad, but personally for me i like getting brainliest because i guess it makes me look cool lol. also it's easy, to give brainliest, when you see a crown that's where you mark brainliest. but sometimes brainly doesn't show the crown i don't understand why, but it happens for some people including me.
If a hacker targets a vulnerable website by running commands that delete the website's data in its database, what type of attack did the hacker perform
Answers
Answer:
SQL injection.
Explanation:
SQL injection is a way to exploit vulnerabilities in the handling of input data in some computer programs that work against a database. The injection takes place by a user submitting parameters to a database query, without the parameters being correctly transformed with respect to special characters, such as escape sequences. With custom parameters, a user can bypass login systems and manipulate data.
3D graphics are based on vectors stored as a set of instructions describing the coordinates for lines and shapes in a three-dimensional space. What do these vectors form?
a. A bitmap graphic
b. A zipped file
c. A wireframe
d. All of the above
Answers
The vectors stored as a set of instructions describing the coordinates for lines and shapes in a three-dimensional space form option C: a wireframe.
What are the 3D graphics?A wireframe may be a visual representation of a 3D question composed of lines and bends that interface a arrangement of focuses in a 3D space. It does not incorporate color or surface data and is frequently utilized as a essential system for making more complex 3D models.
Subsequently, the right reply is choice (c) - a wireframe. option (a) - a bitmap realistic and alternative (b) - a zipped record are not tools as they are not related to the concept of 3D wireframes.
Learn more about 3D graphics from
https://brainly.com/question/27512139
#SPJ1
What's the output of the following code?
var x = 10;
x = x + 4;
Console.log (“The value of x is "+x+"!");
O 14!
O The value of x is x!
O The value of x is 14
O The value of x is 14!
Answers
The answer should be "The value of x is 14!"
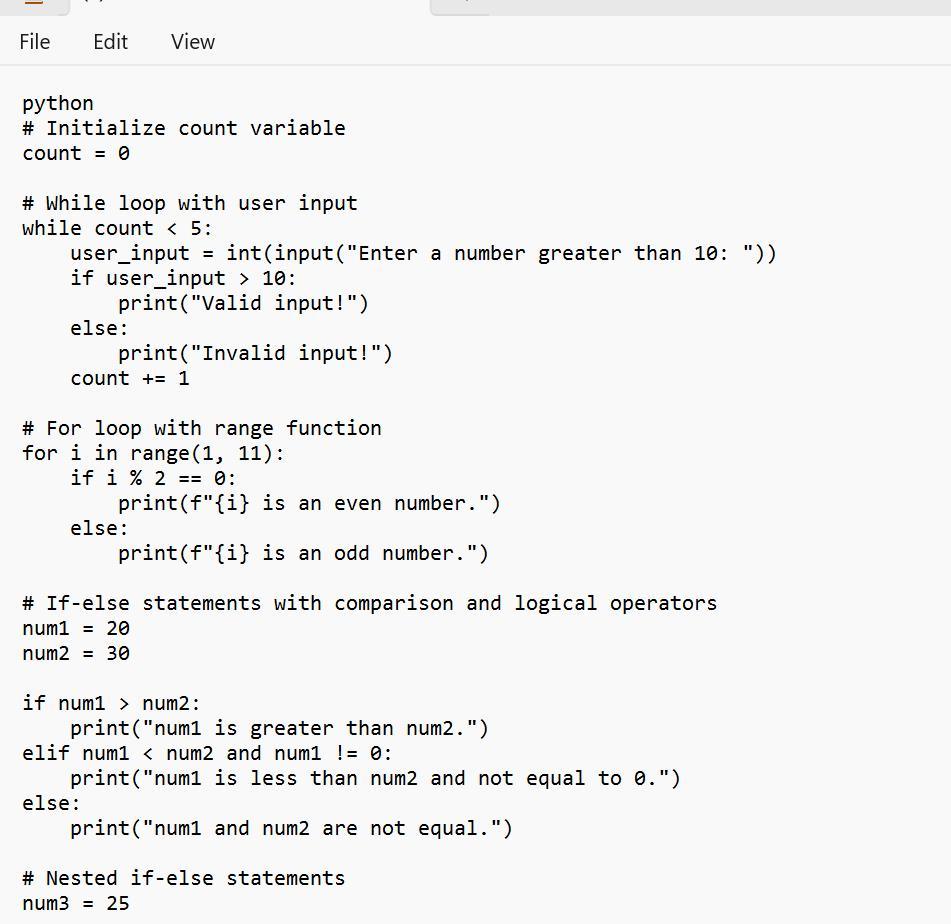
A detailed description is shown in the photo below. I wish you success!

if-else AND if-elif-else
need at minimum two sets of if, one must contain elif
comparison operators
>, <, >=, <=, !=, ==
used at least three times
logical operator
and, or, not
used at least once
while loop AND for loop
both a while loop and a for loop must be used
while loop
based on user input
be sure to include / update your loop control variable
must include a count variable that counts how many times the while loop runs
for loop must include one version of the range function
range(x), range(x,y), or range(x,y,z)
comments
# this line describes the following code
comments are essential, make sure they are useful and informative (I do read them)
at least 40 lines of code
this includes appropriate whitespace and comments
python
Answers
Based on the image, one can see an example of Python code that is said to be able to meets the requirements that are given in the question:
What is the python?The code given is seen as a form of a Python script that tells more on the use of if-else as well as if-elif-else statements, also the use of comparison operators, logical operators, and others
Therefore, one need to know that the code is just a form of an example and it can or cannot not have a special functional purpose. It is one that is meant to tell more on the use of if-else, if-elif-else statements, etc.
Learn more about python from
https://brainly.com/question/26497128
#SPJ1

QUESTION 5 OF 30
Burnout can happen quickly when
working with multiple sysadmins
working overtime
working as the sole sysadmin
Answers
Answer:
Burnout can happen quickly when working with multiple sysadmins, working overtime, or working as the sole sysadmin.
Explanation:
Create a Java program that asks the user for three test
scores. The program should display the average of the
test scores, and the letter grade (A, B, C, D or F) that
corresponds to the numerical average. (use dialog boxes
for input/output)
Answers
Answer:
there aren't many points so it's not really worth it but here
kotlin
Copy code
import javax.swing.JOptionPane;
public class TestScoreGrader {
public static void main(String[] args) {
double score1, score2, score3, average;
String input, output;
input = JOptionPane.showInputDialog("Enter score 1: ");
score1 = Double.parseDouble(input);
input = JOptionPane.showInputDialog("Enter score 2: ");
score2 = Double.parseDouble(input);
input = JOptionPane.showInputDialog("Enter score 3: ");
score3 = Double.parseDouble(input);
average = (score1 + score2 + score3) / 3;
output = "The average is " + average + "\n";
output += "The letter grade is " + getLetterGrade(average);
JOptionPane.showMessageDialog(null, output);
}
public static char getLetterGrade(double average) {
if (average >= 90) {
return 'A';
} else if (average >= 80) {
return 'B';
} else if (average >= 70) {
return 'C';
} else if (average >= 60) {
return 'D';
} else {
return 'F';
}
}
}
Explanation:
You are a systems analyst. Many a time have you heard friends and colleagues complaining that their jobs and businesses are being negatively impacted by e-commerce. As a systems analyst, you decide to research whether this is true or not. Examine the impact of e-commerce on trade and employment/unemployment, and present your findings as a research essay.
Answers
E-commerce, the online buying and selling of goods and services, has significantly impacted trade, employment, and unemployment. This research essay provides a comprehensive analysis of its effects.
What happens with e-commerceContrary to popular belief, e-commerce has led to the growth and expansion of trade by breaking down geographical barriers and providing access to global markets for businesses, particularly SMEs. It has also created job opportunities in areas such as operations, logistics, customer service, web development, and digital marketing.
While certain sectors have experienced disruption, traditional businesses can adapt and benefit from e-commerce by adopting omni-channel strategies. The retail industry, in particular, has undergone significant transformation. E-commerce has empowered small businesses, allowing them to compete with larger enterprises and fostered entrepreneurial growth and innovation. However, there have been job displacements in some areas, necessitating individuals to transition and acquire new skills.
Read mroe on e-commerce here https://brainly.com/question/29115983
#SPJ1
Why would you not restore a Domain Controller that was last backed up twelve months ago
Answers
Answer:
All the data and information that was updated or added since then will be lost so it is useless to restore a Domain Controller that was backedup twelve months ago.
Explanation:
A domain conttoller back-up must be prepared on regular basis else if DC breaks, restoration of most recent database will be impossible.
What is one way a lender can collect on a debt when the borrower defaults?
Answers
Answer:
When a borrower defaults on a debt, the lender may have several options for collecting on the debt. One way a lender can collect on a debt when the borrower defaults is by suing the borrower in court. If the lender is successful in court, they may be able to obtain a judgment against the borrower, which allows them to garnish the borrower's wages or seize their assets in order to pay off the debt.
Another way a lender can collect on a debt when the borrower defaults is by using a debt collection agency. Debt collection agencies are companies that specialize in recovering unpaid debts on behalf of lenders or creditors. Debt collection agencies may use a variety of tactics to try to collect on a debt, including contacting the borrower by phone, mail, or email, or even suing the borrower in court.
Finally, a lender may also be able to collect on a debt when the borrower defaults by repossessing any collateral that was pledged as security for the debt. For example, if the borrower defaulted on a car loan, the lender may be able to repossess the car and sell it in order to recover the unpaid balance on the loan.
Explanation:
Consider the definition of the Person class below. The class uses the instance variable adult to indicate whether a person is an adult or not.
public class Person
{
private String name;
private int age;
private boolean adult;
public Person (String n, int a)
{
name = n;
age = a;
if (age >= 18)
{
adult = true;
}
else
{
adult = false;
}
}
}
Which of the following statements will create a Person object that represents an adult person?
a. Person p = new Person ("Homer", "adult");
b. Person p = new Person ("Homer", 23);
c. Person p = new Person ("Homer", "23");
d. Person p = new Person ("Homer", true);
e. Person p = new Person ("Homer", 17);
Answers
Answer:
b. Person p = new Person ("Homer", 23);
Explanation:
The statement that will create an object that represents an adult person would be the following
Person p = new Person ("Homer", 23);
This statement creates a Person object by called the Person class and saving it into a variable called p. The Person method is called in this object and passed a string that represents the adult's name and the age of the adult. Since the age is greater than 18, the method will return that adult = true.
The other options are either not passing the correct second argument (needs to be an int) or is passing an int that is lower than 18 meaning that the method will state that the individual is not an adult.
Cindy wants to install a new application on her computer. This application requires the operating system to have 1 gigabyte in working memory to function properly. Which of the following system requirements does Cindy need to check for compatibility?
Answers
Answer: She needs to check her systems storage. (The working memory)
Explanation: In order to know if she can get the application she needs to check those things it requires.
Hope this helps-
Even though the terms operating memory and short-term memory are frequently used interchangeably, some theorists contend that the two memory types are distinct from one another because working memory permits the manipulation of information.
What system storage working memory to function properly?In contrast to long-term memory, which stores a large amount of knowledge over a lifetime, working memory is the little amount of information that may be kept in mind and used to carry out cognitive tasks. One of the most often used concepts in psychology is working memory.
Working memory is the short-term storage of information, in contrast to long-term memory, which accumulates a huge quantity of information throughout a lifetime. That has been stored, while short-term memory only refers to the temporary storing of information.
Therefore,She needs to check the storage on her computer. She needs to check the things the application needs in order to determine whether she can obtain it.
Learn more about system storage here:
https://brainly.com/question/28585157
#SPJ2
What is
relation degree.
Answers
Answer:
Explanation:
The degree of relationship can be defined as the number of occurrences in one entity that is associated with the number of occurrences in another entity. There is the three degree of relationship: One-to-one (1:1) One-to-many (1:M)
Create Task for AP computer science principles python
Answers
The AP program offers two computer science courses: AP Computer Science A and AP Computer Science Principles.
Thus, The more comprehensive of the two courses, AP Computer Science Principles teaches students the fundamentals of computer science while emphasizing teamwork.
Although computer science is a useful subject to study, is the exam challenging to pass.
For aspirant AP Computer Science Principles students, it's a good thing that the subject isn't ranked in the top 10 most challenging AP courses. But that doesn't make it any less difficult. Visit our AP Computer Science Principles resource page.
Thus, The AP program offers two computer science courses: AP Computer Science A and AP Computer Science Principles.
Learn more about AP program, refer to the link:
https://brainly.com/question/3121467
#SPJ1
Which heading function is the biggest?
1. h1
2. h2
3. h3
Answers
Answer:
h3
Explanation:
sub to Thicc Panda on YT
PLEASE HELP ME ANSWER THIS QUESTION. I REALLY REALLY NEED IT.
. According to IEEE, what is software engineering? (A) The study of
approaches (B) The development of software product using scientific
principles, methods, and procedures (C) The application of engineering
to software (D) All of the above
Answers
IEEE (Institute of Electrical and Electronics Engineers) describes software engineering as:
(D) All of the above.
Software engineering encompasses the study of approaches, and the development of software products using scientific principles, methods, and procedures. It also encompasses the application of engineering principles to software. It is a multidisciplinary field that combines technical knowledge, problem-solving skills, and systematic processes to design, develop, and maintain software systems efficiently and effectively.
list at least 5 disadvantages caused by computer viruses?
Answers
The 5 disadvantages caused by computer viruses:
A lot of pop-ups.Slow performance.Consistent crashes.Storage space shortage.The issues of Missing files.what are Computer virus?
A computer virus is known to be a kind a type of computer program that is, if it is executed, tends to double itself by changing other computer programs as well as inserting its own kind of code.
Note that if the replication process is said to succeeds, the affected areas are then known to be called "infected" with a computer virus.
Other disadvantages of computer virus are:
Unknown login items.Increased network traffic.Browser homepage is altered.Therefore, The 5 disadvantages caused by computer viruses:
A lot of pop-ups.Slow performance.Consistent crashes.Storage space shortage.The issues of Missing files.Learn more about computer viruses from
https://brainly.com/question/8401461
#SPJ1
Explain these five exffects of moisture on smart and modern materials. The materials: 2. Photochromic pigment 1.Thermochromic pigment 3. Shape memory polymer 4. Shape memory Alloy 5.Hydrogels
Answers
Smart materials are referred to as "reactive materials." Exposure to stimuli like as electric and magnetic fields, stress, moisture, and temperature can alter their characteristics.
Explain these five effects of moisture on smart and modern materials?Photochromic pigment—When exposed to light, photochromic pigments change color. Thermochromic pigment-When the temperature of thermochromic pigments shifts, the color changes. Shape memory polymer- Shape-memory Polymers are clever synthetic polymers that may return to their original shape after being deformed.Shape memory Alloy - Shape-memory alloys are metals that, even when distorted below a certain temperature, retain their shape.Hydrogels- A hydrogel is a three-dimensional system of hydrophilic polymers that can swell and absorb a lot of water.Thus, Smart materials are referred to as "reactive materials
For more information about Smart materials, click here:
https://brainly.com/question/2987553
#SPJ1
A script meaning sound effects
Answers
a) Importance of Software Engineering I
Answers
Answer:
os, operating system is very important
Should the federal government have bug bounty programs? Why or why not?
Answers
I think this question is supposed to be an opinion question but Im not sure
Bug bounty programs are initiatives in which organizations offer rewards to ethical hackers for identifying and reporting security vulnerabilities in their software, systems, or networks.
What is federal government?The federal government refers to the central government of a country, such as the United States government.
The primary reason is that the government has a vast amount of sensitive information, and data breaches can have serious consequences.
The government is responsible for protecting citizens' personal information, as well as national security secrets, and any data breaches could potentially cause harm to individuals and national security.
Another reason why the federal government should have bug bounty programs is that it can help the government identify skilled and ethical hackers who can be recruited to work for the government.
Thus, the federal government should have bug bounty programs.
For more details regarding federal government, visit:
https://brainly.com/question/371257
#SPJ2
What happens after the POST?
Answers
After the POST, the computer is ready for user interaction. Users can launch applications, access files, browse the internet, and perform various tasks depending on the capabilities of the operating system and the installed software.
After the POST (Power-On Self-Test) is completed during a computer's startup process, several important events take place to initialize the system and prepare it for operation. Here are some key steps that occur after the POST:
1. Bootloader Execution: The computer's BIOS (Basic Input/Output System) hands over control to the bootloader. The bootloader's primary task is to locate the operating system's kernel and initiate its loading.
2. Operating System Initialization: Once the bootloader locates the kernel, it loads it into memory. The kernel is the core component of the operating system and is responsible for managing hardware resources and providing essential services.
The kernel initializes drivers, sets up memory management, and starts essential system processes.
3. Device Detection and Configuration: The operating system identifies connected hardware devices, such as hard drives, graphics cards, and peripherals.
It loads the necessary device drivers to enable communication and proper functioning of these devices.
4. User Login: If the system is set up for user authentication, the operating system prompts the user to log in. This step ensures that only authorized individuals can access the system.
5. Graphical User Interface (GUI) Initialization: The operating system launches the GUI environment if one is available. This includes loading the necessary components for desktop icons, taskbars, and other graphical elements.
6. Background Processes and Services: The operating system starts various background processes and services that are essential for system stability and functionality.
These processes handle tasks such as network connectivity, system updates, and security.
For more such questions on POST,click on
https://brainly.com/question/30505572
#SPJ8
1. AVI files are known for displaying great video quality while maintaining an ____ file size
a. ever-changing
b. medium
c. large
d.small
2.What do we call a lossless image format that is most often used in web design
1. Audio Video Interleaved (AVI)
2. Portable Network Graphics (PNG)
3. Bit mapped paint (BMP)
4. GPU
Answers
ANSWER: C. large
Explanation:
Answer:
1. Small
Explanation:
For 3-D modeling unit 4 wrapping up the unit quiz.
Need help for making menu printing function and template menu loop
This is for a project I have in class, but we didn’t go over files yet so I’m confused.
make menu printing function
template menu loop
assuming user does not make mistakes
(text file):
add/remove items
create file if not present
menu program so it will need a menu
Answers
The Loop pulls the data for each post from the WordPress database and replaces each template tag with the relevant data. Each post in The Loop will process any HTML or PHP code.
What role of menu function and template menu loop?Users of Business+ can manage the individuals, files, and task lists that are automatically added when loops are first formed by using loop templates. You can specify in these loop templates what details or documents an agent must provide before submitting them for evaluation.
Therefore, The menu plays a significant role in the operation's identity and is the main factor in determining the operation's budget.
Learn more about loop here:
https://brainly.com/question/29479833
#SPJ1
Citi bike is an example of which arena of technology
Answers
Citi bike is an example of the arena of technology called Lyft.
What is Citi Bike?Citi Bike is a privately owned public bicycle-sharing system that operates in the Bronx, Brooklyn, Manhattan, and Queens boroughs of New York City, as well as Jersey City and Hoboken, New Jersey.
It was managed by Motivate (previously Alta Bicycle Share), with former Metropolitan Transportation Authority CEO Jay Walder as CEO, until September 30, 2018, when the firm was bought by Lyft. Lyft technology is used in the system's bikes and stations.
The system surpassed 50 million rides in October 2017 and will reach 100 million rides in July 2020.
Learn more about Lyft:
https://brainly.com/question/28547867
#SPJ1
Create a Word document with text, links, pictures, and content related to Artificial
elligence. (min 150 words).
Answers
To create a word document with text, links, images and content related to Artificial Intelligence, you can carry out more in-depth research on the topic and perform formatting in the software according to your needs.
For better contextualization, let's better understand the impact of artificial intelligence in the globalized world in which we live.
Artificial intelligenceIt is a complex field of study that uses theories, technologies and methods to enable machine learning through experiences, generating automatic adjustments to data inputs and performing according to natural language.
Able to process large volumes of data and recognize patterns, computers begin to perform tasks and generate learning just like the human brain.
To create your essay on artificial intelligence, you can also delve into different approaches to the topic, such as Big Data and its benefits for today's society, such as:
InnovationSpeedEfficiencySafetyAutomationTherefore, artificial intelligence is an expanding field that provides many advantages for society and organizations, making processes faster, optimized and is being used in various fields of science and knowledge.
Find out more information about Artificial Intelligence here:
https://brainly.com/question/25282575
Billie downloads an email attachment from a co-worker. The attachment contains a virus. Within minutes of downloading the file, Billie's computer shuts down and will not turn back on. The company uses an intranet network. How did a virus most likely get into the original file sent to Billie? Explain your answer.
Answers
Answers:
You suspect that you have accidentally downloaded a virus.Turn off his computer and reboot from a clean system disk.She has no reason to expect a file from this person.Lisa has received a file attachment from a co-worker, James.The attachment contains a virus.The virus most likely get into the original file sent to Billie through a corrupt file that was sent and it automatically pitch itself to the file.
How do viruses get into files?A lot of Computer Viruses are known to often spread to other disk drives or computers mostly wen an infected files are gotten through downloads that are gotten from websites, email attachments, etc.
Note that the issue is that virus most likely get into the original file sent to Billie through a corrupt file that was sent and it automatically pitch itself to the file.
Learn more about email attachment from
https://brainly.com/question/17506968
#SPJ2
different types of computer and state the major difference between them
Answers
Answer:
computers system may be classified according to their size.
four types of computers are;
microcomputers / personal computers- micro computers are also called personal computers which is PC this computer came in different shapes size and colors. a personal computers are designed to be used by one person at a time.some examples of the computer are;
laptopdesktopa palmtopa work station2. mini computers- mini computers are sometimes called mid-range computers which are more powerful than microcomputers and can support a number of users performing different tasks, they were originally developed to perform specific tasks such as engineering calculations.
3. Mainframe computers- Mainframe computers are larger systems that can handle numberous users, store large amounts of data and process transaction at a high rate. these computers are expensive and powerful.
4. super computers- super computers are the most largest, fastest and most powerful computer. this systems are able to process hundreds of million of instructions per second they are used for job requiring and long complex calculation.
which of the following desktops was derived from gnome 3, follows traditional desktop metaphor conventions, and is the primary desktop environment for the mint distribution?
Answers
The cinnamon desktop was derived from gnome 3 and follows traditional desktop metaphor conventions, and is the primary desktop environment for the mint distribution.
For Linux and Unix-like operating systems, Cinnamon is a free and open-source desktop environment that is based on GNOME 3 but adheres to conventional desktop metaphor principles. In response to the April 2011 release of GNOME 3, which abandoned the traditional desktop paradigm of GNOME 2 in favor of GNOME Shell, the Linux Mint team began developing Cinnamon. After numerous unsuccessful attempts to alter GNOME 3 to fit their design goals, the Linux Mint team decided to create an independent desktop environment by cloning a number of GNOME 3 components. Launched in October 2013, Cinnamon 2.0 effectively completed the split from GNOME. Applets and desklets are no longer supported by GNOME 3.The press has largely praised Cinnamon as the defining feature of Linux Mint, highlighting its user-friendliness and low barrier to entry. Cinnamon is comparable to the Xfce, MATE, and GNOME 2 (and GNOME Flashback) desktop environments in terms of its conservative design philosophy.
Know more about Cinnamon:
https://brainly.com/question/28411133
#SPJ4
Write the difference between left-sentential form and
right-sentential form
Answers
Answer:
answer is below
Explanation:
A left-sentential form is a sentential form that occurs in the leftmost derivation of some sentence. A right-sentential form is a sentential form that occurs in the rightmost derivation of some sentence.