You are the administrator of a server, and you have root privileges. The it manager has asked you to install the cups package to enable printing on the server. In this lab, your task is to complete the following: use dnf to install the cups package. After the installation is complete, print the sales document in /home/wadams
Answers
To install the cups package, type dnf install cups and press Enter at the prompt.
In order to confirm the installation, press Y and then Enter.
To print the sales document, enter lpr /home/wadams/sales and press Enter.
What is a cups package?
CUPS was created in 1997 by Michael R Sweet at Easy Software Products, with the first beta release on May 14, 1999. Soon after, Till Kamppeter began packaging CUPS for Mandrake Linux and developing the Foomatic CUPS drivers, which aided in the adoption of CUPS for printing on Linux. In 2002, Apple licensed CUPS for macOS, and in February 2007, Apple bought CUPS and hired Michael to continue its development as an open source project.
Michael left Apple in December 2019 to launch Lakeside Robotics. In September 2020, he collaborated with OpenPrinting developers to fork Apple CUPS in order to continue its development. Today, Apple CUPS is the CUPS version included with macOS® and iOS®, whereas OpenPrinting CUPS is the CUPS version being developed by OpenPrinting for all operating systems.
To know more about OpenPrinting, visit: https://brainly.com/question/27962260
#SPJ4
Related Questions
A summer camp offers a morning session and an afternoon session. The list morningList contains the names of all children attending the morning session, and the list afternoonList contains the names of all children attending the afternoon session.
Only children who attend both sessions eat lunch at the camp. The camp director wants to create lunchList, which will contain the names of children attending both sessions.
The following code segment is intended to create lunchList, which is initially empty.
It uses the procedure IsFound (list, name), which returns true if name is found in list and returns false otherwise.
FOR EACH child IN morningList
{
}
Which of the following could replace so that the code segment works as intended?
(A)
IF (IsFound (afternoonList, child))
{
APPEND (lunchList, child)
}
(B)
IF (IsFound (lunchList, child))
{
APPEND (afternoonList, child)
}
(C)
IF (IsFound (morningList, child))
{
APPEND (lunchList, child)
}
(D)
IF ((IsFound (morningList, child)) OR
(IsFound (afternoonList, child)))
{
APPEND (lunchList, child)
}
Answers
Answer:
The answer is "Option A".
Explanation:
In this question, the choice "A" is correct because in this a conditional if block statement is used that that use "IsFound" method that takes two parameters "afternoonList and Child" in its parameter and use the append method that takes "lunchList and child" in parameter and add values, that's why other choices are wrong.
If your laptop shows in the label that there are two different amps, does that mean that as long as your charger with one of the correct amps and the correct voltage will work? PICTURES PROVIDED
1. Of laptop label
2. Of charger label


Answers
Answer:
It is important to match the voltage and amperage of the charger to the specifications on the laptop label to ensure compatibility and avoid damaging your device. Looking at the pictures you provided, it appears that the laptop label shows two different amperage ratings for the AC adapter, which means that you can use a charger with either 2.25A or 3.42A output as long as it has the correct voltage (19.5V) and a compatible connector. However, it is recommended to use the adapter with the higher amperage rating to ensure that it can provide sufficient power for the laptop to operate optimally, especially during heavy usage. The charger label you provided shows an output of 19.5V and 3.33A, which meets the voltage and amperage requirements for your laptop, so it should work fine. Just make sure that the
Cheryl is responsible for cybersecurity at a mid-sized insurance company. She has decided to use a different vendor for a network antimalware than she uses for host antimalware. Is this a recommended action, why or why not
Answers
yes, this a recommended action and this is known to be best described as vendor diversity.
What is Vendor diversity?This is known to be one that gives two security benefits in regards to the fact that it does not have a single point of failure if one vendor cease operations and also each vendor has their own methodology and algorithms used for known or seeing malware.
Hence in the above case, yes, this a recommended action and this is known to be best described as vendor diversity.
learn more about cybersecurity from
https://brainly.com/question/12010892
#SPJ1
What is an example of information power?.
Answers
People are in a strong position if they have control over information that others need or want. Informational power can be demonstrated by having access to private financial records.
What is information power?A person's ability to persuade others based on their understanding of information that is pertinent to the situation.
Expert power is the capacity for a worker, regardless of level of seniority, to demonstrate knowledge in a field or circumstance. One employee might have the expert power in a situation if, for instance, no one else in the department has any experience using a particular piece of software but that employee does.
Thus, People are in a strong position if they have control over.
For more information about Informational power, click here:
https://brainly.com/question/26217832
#SPJ1
Find H.C.F of 4,5,10 by all the three methods.
Answers
Answer:
1. Factorization Method
2. Prime Factorization Method
3. Division Method
Which design principle is the subject of a photo or image?

Answers
The focal point is where the eye is drawn to in a photo or image.
The content of a photo or image serves as the framing design principle, and the further discussion can be defined as follows:
This placement of the principal topic of a design about other components on the page is referred to as framing. It is most commonly used in cinematography or photography to define how the primary point of an image is located inside the overall image.Therefore, the final answer is "Framing".
Learn more:
brainly.com/question/20307377
When opening and closing a security container, complete the _____.
a. SF 701
b. SF 700
c. SF 702
d. SF 703
Answers
Option c is correct. SF 702 is the answer to this question. SF 702 is used to open and close security containers. Track security containers.
The security container can be opened and closed at any time. However, if possible, security containers should only be opened for privacy and security reasons. Security containers should use all possible safeguards such as guard protection, password protection, fingerprint protection, etc. Standard Form (SF 702) – Security Container Inspection Sheet. A standard form (SF 702 Security Container Sheet) tracks who opens, closes, and inspects security containers containing sensitive information.
SF 702 or "Security Container Check Sheet" is used to record the opening and closing of the data carrier. An area check is carried out in the SF 701 after the daily check is finished. The
SF 702 must be stored and disposed of according to a component records management program. SF 702 will be stored in the NDC until the next conformance inspection by a higher level control center.
Know more about information here:
https://brainly.com/question/29244533
#SPJ4
A _____ is a block of code containing standard SQL statements and procedural extensions that is stored and executed at the DBMS server.
Answers
Answer:
Persistent Stored Module (PSM).
Explanation:
On the following page, write a static method print Short Words that accepts two parameters:_____.
a. a String str containing a list of words (separated by spaces), and an integer maxLength .
b. This method should print out the words in str whose lengths are at most maxLength.
c. You can assume there will always be a space after the last word in the string.
Answers
Methods in Java are collections of program statements that are named, and executed when called/invoked
The printShortWords method in Java where comments are used to explain each line is as follows:
//This defines the static method
public static void printShortWords(String str, int maxLength){
//This iterates through each word in the string
for(String word: str.split(" ")){
//The compares the length of each word to maxLength
if(word.length()<=maxLength){
//If the length of the current word is atleast maxLength, the word is printed
System.out.print(word+" ");
}
}
}
Read more about static methods at:
https://brainly.com/question/19360941
1. Are you aware about ICT technologies, online platforms and functions?
2. If you are to create a microblogging page, what will be your theme or content about?
1. Pick five (5) rules from the core rules of netiquette and cite a scenario which this rule is
violated and explain how will you address or correct this bad practice?
2. List down at least five (5) things you should do or not do to avoid internet threats such as
malwares and spams?
Answers
I am aware about ICT technologies, online platforms and functions.
2. If i create a microblogging page, the theme or content will be about Health and wholeness of the mind.
What is the five (5) rules from the core rules of netiquette?The Core Rules of Netiquette are:
Always Remember that you are Human. Do stand and keep the same standards of behavior online and in real life. Do Know where you are in regards to cyberspace. .Do Respect other people's time as well as their bandwidth. Do make yourself to appear good online. .Do and always Share expert knowledge.Therefore, I am aware about ICT technologies, online platforms and functions. If i create a microblogging page, the theme or content will be about Health and wholeness of the mind.
Learn more about ICT technologies from
https://brainly.com/question/20717870
#SPJ1
One benefit of taking notes in class is that the student
a.watches the teacher.
b.is actively engaged.
c.impresses the teacher.
d.writes instead of talking.
Answers
B),.......
Explanation:
is actively engaged
what are the answers for theses question?




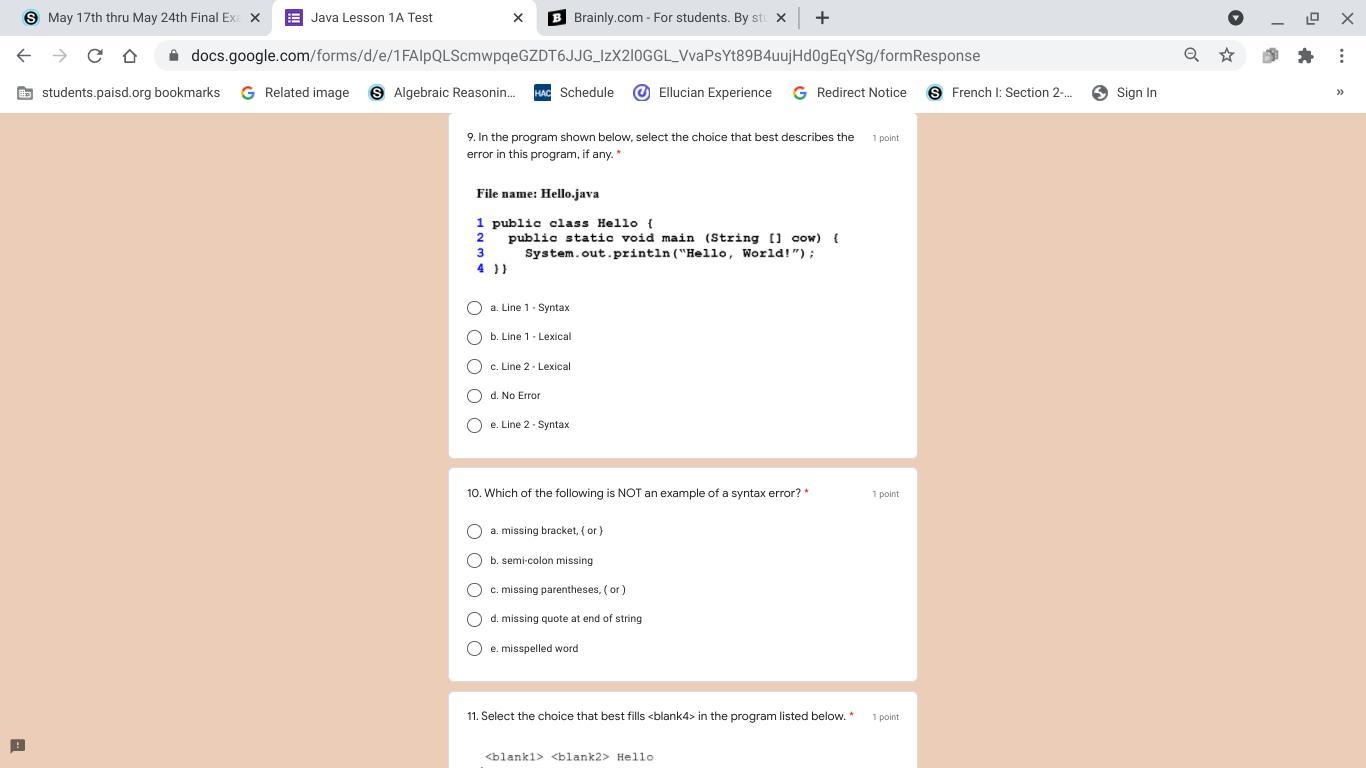
Answers
Answer: me no comprende coding
Explanation:
sorry
• Comments are blank which can be blank entered into documents
. Can be blank by clicking on Previous and blank icons in the blank group
electronically
notes
Comments
Next
navigated
Answers
Answer:
"can be blank by clicking on previous and blank icons in the blank group...
navigated
Explanation:
Been a while since i learned this this is a edu guess.
Given three floating-point numbers x, y, and z, output x to the power of z, x to the power of (y to the power of z), the absolute value of (x minus y), and the square root of (x to the power of z). Output each floating-point value with two digits after the decimal point, which can be achieved as follows: print('{:. 2f} {:. 2f} {:. 2f} {:. 2f}'. Format(your_value1, your_value2, your_value3, your_value4))Ex: If the input is: 5. 0 1. 5 3. 2 Then the output is: 172. 47 361. 66 3. 50 13. 13
Answers
math import, x = floating (input()), y = float (input ()), z = float(input()), value1 = pow(x, z), value2 = pow(x, pow(y, z)), value3 = abs(x - y), value4 = math. sqrt(pow(x, z))
*The code is in Python.
Calculate any formula using math functions. pow - compute powers, abs - compute absolute values, sqrt - compute square roots.
Output the value in the format you want
Note that the specified output is incorrect. It must be:
172.47 361.66 3.50 13.13
push('{:
.2f} {:
.2f} {:
.2f} {:
.2f}'.format(value1, value2, value3, value4))
Know more about Python here:
https://brainly.com/question/18502436
#SPJ4
Computer engineering is a career that......
Answers
Answer:
Computer engineering is a career that works on the development and research of new technology-related things.
Explanation:
Key end users should be assigned to a developmental team, known as the united application development team. True or False
Answers
The given statement "Key end users should be assigned to a developmental team, known as the united application development team" is TRUE
.A united application development team is a group of individuals who come together to develop an application that meets certain requirements. This group will include developers, testers, and project managers, among other roles.
However, the team's success is dependent on the involvement of the end-users who provide feedback on the application during the development process. It is important for key end-users to be assigned to the team because they can provide valuable insight into the application's functionality and user-friendliness. Key end-users are those who will be the primary users of the application.
Learn more about developmental team at
https://brainly.com/question/31164482
#SPJ11
Here is an array with exactly 15 elements: 1 3 4 10 14 19 21 27 31 38 40 48 55 88 101 Suppose that we are doing a binary search for the element 55.
1. Write out the state of the array for each iteration until element 55 is
2. Under what conditions is the binary search algorithm practical?
3. What is the best and worst case complexity?
Answers
Binary search is a practical algorithm for finding an element in a sorted array. Its best case complexity is O(1), while the worst case complexity is O(log n), where n is the number of elements in the array.
Binary search is a divide-and-conquer algorithm that efficiently searches for a target element in a sorted array. It works by repeatedly dividing the search space in half until the target element is found or it is determined that the element does not exist in the array.
In the given scenario, we have an array with 15 elements and we are searching for the element 55. The binary search algorithm proceeds as follows:
1. At the first iteration, the midpoint of the array is calculated as (0 + 14) / 2 = 7. Since the element at index 7 is 27 and 55 is greater than 27, we narrow down the search space to the right half of the array.
2. In the second iteration, the new midpoint is calculated as (8 + 14) / 2 = 11. The element at index 11 is 48, which is still less than 55. Therefore, we continue searching in the right half of the remaining array.
3. The third iteration calculates the midpoint as (12 + 14) / 2 = 13. The element at index 13 is 88, which is greater than 55. Hence, we adjust the search space to the left half of the remaining array.
4. Finally, in the fourth iteration, the new midpoint is calculated as (12 + 12) / 2 = 12. The element at index 12 is 55, which matches our target element.
The binary search algorithm is practical when the array is sorted and the search space can be halved in each iteration. This makes it highly efficient for large arrays as the search time increases logarithmically with the number of elements. However, it is not suitable for unsorted arrays or when frequent insertions or deletions occur, as maintaining the sorted order would be costly.
Learn more about Binary search
brainly.com/question/13143459
#SPJ11
Why is ROM used for in modern computers?
Answers
Answer:
Because ROM saves even after the computer is turned off
Explanation:
RAM doesnt function when the computer is off, ROM does.
Which statement is not true for a good algorithm?
A. It is clear and cannot be interpreted in more than one way by
different people or machines.
B. It successfully solves the desired problem or performs the desired
task.
C. It can perform a task or solve a problem even if various inputs are
involved.
O D. It uses more resources and more time than it needs to.
Answers
Answer:
D. It uses more resources and more time than it needs to.
Explanation:
A, B, and C each show the workload of an algorithm in positive light. However, D shows it using more resources and time than it needs to; something a "good" algorithm would not do.
The software team of a company is working on a project. the project involves many computing systems working together on disjointed tasks towards a single goal. what form of computing would the project be using?
Answers
The software team of a company is working on a project. the project involves many computing systems working together on disjointed tasks towards a single goal. The form of computing that the project will be using is grid computing.
In the field of computers, when multiple computing systems are used so that a single task can be achieved, then such a system is referred to as grid computing.
The main purpose of grip computing is to work on a joint task where each computer system is specialized in one way or the other in order to help in the joint or single goal. Hence, the correct option is grid computing.
Other options, such as mobile computing, are not correct as mobile computing is a wireless communication for the transmission of data.
Although a part of your question is missing, you might be referring to this question:
The software team of a company is working on a project. the project involves many computing systems working together on disjointed tasks towards a single goal. what form of computing would the project be using?
A. mobile computing
B. grid computing
C. cloud computing
D. green computing
To learn more about grid computing, click here:
https://brainly.com/question/14511163
#SPJ4
Give three code examples of how to increment the integer j by 1.
Answers
Answer:
(This is for Javascript)
j++;
j + = 1;
j = j + 1;
Complete the sentence
The protocol governing how a browser should handle web content is
HTML
HTTP
Answers
Answer:i think html
Explanation:
hope it’s right
Answer:
HTTP
Explanation:
A tester is attempting to capture and analyze the traffic on a given network has several switches.what could be used to successfully sniff the traffic on this switched networks ?
Answers
A tester can use a network tapping device or a network analyzer tool. These tools allow the tester to capture and analyze network traffic without disrupting the flow of data on the network.
Here's a step-by-step explanation of how to use these tools:
1. Network Tapping Device: A network tapping device is a hardware device that is inserted between the switch and the network. It passively copies all the network traffic passing through it and sends it to the tester's computer or monitoring device for analysis. The tester can then use a network analyzer tool to analyze the captured traffic.
2. Network Analyzer Tool: A network analyzer tool, also known as a packet sniffer or network protocol analyzer, is a software program that captures and analyzes network traffic. The tester can install this tool on their computer and configure it to capture the traffic from the network interface card (NIC).
To know more about network tapping visit:
https://brainly.com/question/32396020
#SPJ11
a data analyst team is reviewing an old project and needs to understand how the files naming conventions are structured. where should the team locate this information?0 / 1 pointin sqlin the metadatain the folder hierarchiesin the aggregated data
Answers
One should be concise and not provide extraneous amounts of detail. One should not ignore any typos or irrelevant parts of the question.Metadata is data that provides information about other data.
Metadata is a set of data that describes and provides information about other data. Data and metadata work together to create a complete picture of a given subject.Metadata is frequently utilized in library and database systems to manage the storage, discovery, and sharing of data. The way files naming conventions are structured is given in metadata. The metadata is where the team should search for the files naming conventions.Metadata is a good place to look for information about the data. A data analyst team is analyzing an old project and needs to know how the files naming conventions are structured. The team should look in the metadata for this information.Most data management systems enable users to store metadata about their data. This metadata can be as basic as a document's name or as complicated as a complete record of its history, usage, and lineage.For such more question on Metadata
https://brainly.com/question/14960489
#SPJ11
the ______tool is used to save the changes made in a document ( save./save as)
Answers
Answer:
save
Explanation:
save to save the changes
save as to save the form of file and find the the location of file
what is a data collector set, and what are the three basic types of data collection tools and formats?
Answers
Answer:
A set of strategies for gathering performance and diagnostic data and presenting it in a report or log style. The fundamental data collection approaches can include one or more of the following: performance counters, event traces, and system configuration data.
Performance counters and performance counter reports, traces and trace reports, and system configuration data are the three basic types.
Which of the following functions will truncate a numeric value to a specific position? A. TRUNCATE B. TRUNC C. TRUND D. none of the above.
Answers
The correct function to truncate a numeric value to a specific position is B. TRUNC.
The TRUNC function in SQL is used to truncate a numeric value to a specific number of decimal places. This function rounds down the value to the specified number of decimal places. The syntax for the TRUNC function is TRUNC(number, decimal places). The number parameter specifies the number to be truncated, and decimal places parameter specifies the number of decimal places to which the number should be truncated.
The TRUNCATE function is not a valid function in SQL. TRUND is also not a valid function in SQL. Therefore, the correct answer is B. TRUNC. This function is commonly used in financial applications where it is important to display a specific number of decimal places. For example, if you want to display the amount of a transaction in dollars and cents, you would use the TRUNC function to truncate the value to two decimal places. In summary, the TRUNC function in SQL is used to truncate a numeric value to a specific number of decimal places. It rounds down the value to the specified number of decimal places and is commonly used in financial applications. The correct function to truncate a numeric value to a specific position is B. TRUNC.
To know more about TRUNC visit:
https://brainly.com/question/27351576
#SPJ11
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
Suppose a client calls and is upset because he trashed something on his blog. He tells you that he knows software does not allow you to recover what has been deleted and asks for your help. What can you tell him?
WordPress includes a recovery from the trash, but it is complicated.
WordPress includes an undo from the trash.
WordPress does not allow recovery from the trash.
WordPress only allows recovery of images from the trash.
Answers
Answer:
WordPress only allows recovery of images from the trash.
What is a method that deletes an item from a list using the item’s value?
Remove
Delete
Erase
PopWhat is a method that deletes an item from a list using the item’s value?
Remove
Delete
Erase
Pop
Answers
Answer:
Remove
Explanation:
A method that deletes an item from a list using the item’s value is "Remove"
The "remove () function in python language indicates the specific element or character to be that needs to be removed.
For example
myList = ["Jane",16,34,52,"Lamar",13,27,20]
myList.remove(34)
myList
OUTPUT : ["Jane",16,52,"Lamar", 13,27,20]
Therefore, by printing the list using the print(), we can observe that the element 34 has been removed from myList.
Hence, the correct answer, in this case, is " Remove."