you are the network administrator for a small company that implements nat to access the internet. however, you recently acquired five servers that must be accessible from outside your network. your isp has provided you with five additional registered ip addresses to support these new servers, but you don't want the public to access these servers directly. you want to place these servers behind your firewall on the inside network, yet still allow them to be accessible to the public from the outside. which method of nat translation should you implement for these servers? answer restricted dynamic static overloading
Answers
Static NAT should be used as the NAT translation technique for these servers.the servers would share an IP address and port, which can lead to conflicts and security problems.
A one-to-one mapping between a public IP address and a private IP address is produced via static NAT. In this scenario, a distinct public IP address would be given to each of the five servers and mapped to that address on the internal network. This enables the servers to remain firewall-protected while yet being reachable from outside.
Because it limits access from the outside to particular ports or IP addresses on the internal network, restricted NAT is inappropriate. Because dynamic NAT selects a public IP address from a pool of accessible addresses, which may vary each time a server makes a connection, it would not function. PAT, or port address translation, another name for NAT overloading,
Because it permits several devices to share a single public IP address and port number, it is ineffective. As a result, the servers would share an IP address and port, which can lead to conflicts and security problems.
learn more about IP address here:
https://brainly.com/question/31026862
#SPJ4
Related Questions
what syntax would a vim user choose if they wanted to perform a search-and-replace operation on an entire document?
Answers
A Vim user would choose the syntax ":1,$s/search/replace/g" to perform a search-and-replace operation on an entire document. In this syntax, the colon (:) denotes entering command-line mode, "1" is the starting line, and "$" represents the end of the document.
How the Vim user choose the syntax?As a Vim user, the syntax for performing a search-and-replace operation on an entire document is straightforward.
First, you need to open the document in Vim and ensure that you are in normal mode.
Then, you need to use the command:%s/old_text/new_text/g.
The percent symbol indicates that you want to perform the operation on the entire document, while the "s" stands for substitute.
The old_text represents the text you want to replace, and new_text represents the new text you want to insert.
The "g" at the end of the command stands for "global," which means that Vim will replace all occurrences of old_text with new_text in the document.
Once you enter the command and press enter, Vim will perform the search-and-replace operation on the entire document.
Learn more about Vim user at
https://brainly.com/question/29649677
#SPJ11
Help me please with this

Answers
Answer:
Explanation:
QUestion 2 is A
QUestion 1 is A i think
the font size sets the size of text
Answers
Answer:
Yup thats correct
Explanation:
A charity is keeping track of donations for one month. The director would like to create a report that groups data by week. Each group will contain donations collected on each day of the week. Which type of calculated figure should the director use to display a cumulative total beneath each group?
running sum
sum
grand total
percentage
Answers
The calculated figure that the director should use to display a cumulative total beneath each group is option A: "running sum".
Which type of calculated figure is this?A "running sum" is used by the director to display cumulative totals beneath each group. It accumulates the values of a field over time or across a grouping.
Director groups donations weekly and displays total for each day using running sum to calculate and add up amount as days progress. Director groups donations weekly by creating a running sum field that adds daily totals until end of the week. Cumulative totals for each day of the week displayed in report.
Learn more about sum from
https://brainly.com/question/25734188
#SPJ1
which abstraction concept is needed to distinguish among database objects and classes and to identify database objects
Answers
The abstraction concept needed to distinguish among database objects and classes, and to identify database objects is "Identification".
Identification refers to the unique identifier assigned to each database object, which enables it to be distinguished from other objects. In a database, objects can be classified and organized into classes or tables, but each object must have a unique identifier that distinguishes it from all other objects in the database. This identifier is typically a key field or a combination of key fields that are used to uniquely identify the object.
the concept of Identification is essential in databases to distinguish among objects and to identify them uniquely. By assigning a unique identifier to each object, we can ensure that we can manage and manipulate data effectively.
Learn more about the abstraction concept:https://brainly.com/question/24366147
#SPJ11
Your question is incomplete but probably the complete question is :
Which abstraction concept is needed to distinguish among database objects and classes, and to identify database objects?
Specialization
Identification
Aggregation
Classification
Sumproduct is a function that returns the sum of the products of elements in a set of arrays.
a. True
b. False
Answers
The statement "sumproduct is a function that returns the sum of the products of elements in a set of arrays" is a true statement. Sumproduct is a function in we can use in Excel.
What is Sumproduct in Excel?The SUMPRODUCT function is categorized under the Excel Math and Trigonometric functions. The function will multiply the corresponding elements of a given array and then return the sum of the products. It is used to calculate the weighted average.
For some jobs like financial analyst, SUMPRODUCT is a very handy function as it can process tables in different ways and helps to compare data in two or more ranges. It also helps to calculate data with multiple criteria.
Learn more about sumproduct brainly.com/question/29731774
#SPJ4
1. Sunday Times wants an analysis of the demographic characteristics of its readers. The
Marketing department has collected reader survey records containing the age, gender, marital
status, and annual income of readers. Design an application (Flowchart) that accepts reader
data and, when data entry is complete, produces a count of readers by age groups as follows:
under 20, 20–29, 30–39, 40–49, and 50 and older. Hint: Refer to the program discussed in
class Figure 6-15
2. Create the logic (Flowchart) for a program that calculates and displays the amount of money
you would have if you invested R10000 at 4 percent simple interest for one year. Create a
separate method to do the calculation and return the result to be displayed.
The main program (Flowchart) should prompt the user for the amount of money and passes it
to the interest-calculating method.
Answers
Answer:
GIRL
Explanation:
DALAGANG FILIPINA
14 YEARS OLD
NEED FRIENDS
Which statement assigns the value 98 to the variable myScore in Python?
myScore << 98
myScore = 98
x == 98
x! = 98
Answers
myScore = 98 is the correct choice.
Answer:
b
Explanation:
3 difference between single user operating system and multi user operating system
Answers
Answer:
Explanation:
A Single User Operating System is designed for use by only one person at a time. This type of OS is typically used on desktop or laptop computers and not typically used on servers. Single User Operating Systems are generally more user-friendly and easier to use than Multi User Operating Systems.
A Multi-User Operating system allows multiple users to access the same computer system at the same time. Multi User Operating Systems have many uses but are particularly popular in business and educational settings where multiple people need to access a single computer system.
______________________ increases security by verifying identity based on more than just a password or pin.
Answers
Answer:
two-factor authentication
Explanation:
two-factor authentication increases security by verifying identity-based on more than just a password or pin.
How do you translate binary code?
Answers
Computers can comprehend binary numerals, which are numbers. It is composed of both 0s and 1s. Computers and a few other electrical equipment can only understand binary.
hence they only accept input in binary format and output results in binary format.
We will learn how to convert a binary number to a decimal in this post.
Formula from Binary to Decimal
In order to convert a binary number to a decimal number, we must multiply each digit of the binary number starting at 0 by powers of 2 and then sum the results to obtain the decimal number.
Direct communication with individuals via binary code is uncommon. While computers store, sort, and transfer data using binary digits, they also convert all of these 0s and 1s into other, more comprehensible representations.
There are various potential justifications for using a binary translator.
Learn more about Binary here:
https://brainly.com/question/19802955
#SPJ4
What is the key sequence to copy the first 4 lines and paste it at the end of the file?
Answers
Press Ctrl+C after selecting the text you want to copy. Press Ctrl+V while holding down the cursor to paste the copied text.
What comes first in the copy and paste process for a slide?Select the slide you wish to copy from the thumbnail pane, then hit Ctrl+C on your keyboard. Move to the location in the thumbnail pane where you wish to paste the slide, then hit Ctrl+P on your keyboard.
What comes first in the copying process of a segment?The secret to copying a line segment is to open your compass to that segment's length, then mark off another segment of that length using that amount of opening.
To know more about copy visit:-
https://brainly.com/question/24297734
#SPJ4
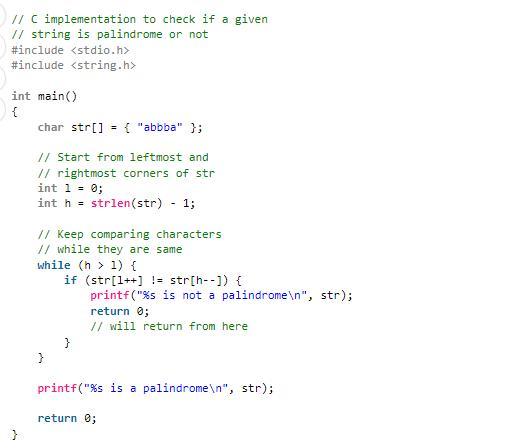
You have been given palindrome. 5 , a MIPS assembler program that reads a line of input and then prints 2 lines.
\$1521 spim -f palindrome, s
Enter a line of input: Hello
not palindrome
palindrone
Add code to palindrome. 5 to make it equivalent to this \(C\) program which reads a line and prints whether it is a palindrome
or not.
Answers
The isPalindrome() method can be used to determine whether a string is a palindrome. The method will return true if the input string is a palindrome and false if it is not. We send our input string as an argument.
What is palindrome function ?If a string's reverse is the same as the original, it is referred to as a palindrome string. For instance, level, radar, etc. A number that is the same number in reverse is referred to as a palindrome number. like as 3553, 12321, etc.A string's palindrome status may be checked using the isPalindrome() function. If the supplied string is a palindrome, the method will return true; if it is not, it will return false. Our input string is sent as an argument.The isPalindrome() method can be used to determine whether a string is a palindrome. The method will return true if the input string is a palindrome and false if it is not. We send our input string as an argument.Learn more about palindrome function refer to :
https://brainly.com/question/23161348
#SPJ1
when an increase in technology only improves one of the goods on the of, the ppf shifts out equally along both axes. True/False ?
Answers
True, When an increase in technology only improves one of the goods on the of, the ppf shifts out equally along both axes.
False. When an increase in technology improves the production of one good, the production possibility frontier (PPF) shifts outwards only along the axis of that good, becoming steeper for the other good. The slope of the PPF reflects the opportunity cost of producing one good in terms of the other, and if the production of one good becomes more efficient, the opportunity cost of producing it will decrease, leading to a steeper slope for the other good.
Therefore, the shape of the PPF changes and moves away from the origin in the direction of the good that has seen an improvement in technology. The new PPF represents a higher level of production efficiency, as more of both goods can be produced with the same resources. This means that the economy has increased its capacity to produce and has greater flexibility in choosing the combination of goods it wants to produce.
Learn more about PPF here:
https://brainly.com/question/17581360
#SPJ4
20. Which of the following is an example of plagiarism?
A. Citing information from a fake news site.
B. Illegally downloading a movie that you like from the Internet.
C. Copying your friend's work and claiming it as your own.
D. Sharing an author's words and giving them proper credit.
Answers
Answer: C. Copying your friend's work and claiming it as your own.
Explanation:
plagiarism is taking someone else's work or ideas and passing them off as one's own.
How does vpn software ensure that people accessing a network are authorized to do so? Multiple ChoiceVPN software establishes secure connections.VPN software uses encryption to protect the users' credentials.VPN software authenticates users.VPN software links blocks of transactions connected to the user.
Answers
VPN software authenticates users to ensure that people accessing a network are authorized to do so.
What is a VPN?Software called VPN (Virtual Private Network) is created to offer safe online remote access to a private network. The VPN connection process must include authentication to assist ensure that only authorised users can access the network.
The VPN programme confirms a user's identity when they connect to a VPN by employing authentication techniques including passwords, digital certificates, or biometric information. The user's identity and eligibility to enter the network are verified through the authentication process.
After user authentication, the VPN software uses encryption to create a secure connection between the user's device and the VPN server. The user's data and communications are protected against illegal access and interception thanks to this.
Learn more about encryption here:
brainly.com/question/17017885
#SPJ1
PLS HELP FOR ACSL What Does This Program Do - Arrays Problem. Pls give the correct answer!! ASAP!!!!!!
LOOK AT IMAGE PLS

Answers
After the following program is executed, 3 elements in the array are not zero.
What is array?An array is a data structure used for storing and organizing elements of the same data type. Arrays are typically used to store collections of numbers, strings, or objects. Arrays allow for fast access and manipulation of data, as elements can be retrieved and updated quickly. Arrays are also used in some programming languages for passing parameters to functions and for defining and accessing multidimensional data structures, such as matrices and tables. Arrays are usually created using the array constructor of the language, which specifies the data type of the array, the number of elements it can store, and the initial values of the elements. Arrays are dynamic in nature, meaning they can be resized and changed as needed. Arrays can also be used to store objects, allowing the programmer to create complex data structures.
To learn more about array
https://brainly.com/question/30510492
#SPJ1
if teh formula in cell 49 is copied to cells e49:f49, what sequence of values would be generated in cells d49:f49?
Answers
Excel moves or copies a cell with formulas and their results, cell formats, and comments. When moving or copying a cell.
If there are certain cells, rows, or columns that do not appear on a worksheet, you can copy all cells.
Otherwise, the visible cells. In adding to viewable cells, Excel copies cached or filtering cells per default.
C C C
The formulation in cell D49 is a stable formula that does not vary by cell type. Alt + F4 is the shortcut to fasten a form.
Therefore, the formula given in D49 would achieve the same output when copied to another cell.
To know more about cells visit:
https://brainly.com/question/30046049
#SPJ4
A cell with formulas, results, cell formats, and comments can be moved or copied by Excel whenever a cell gets changed or modified.
What will happen if there are specific cells, rows, or columns?You can copy all cells if a worksheet contains several cells, rows, or sections that are incomplete. if not, the cells that are visible. Excel by automatically copies cached or filtered information when expanding them to display cells.
What is the formulation in cell D49?Cell D49 contains a formula that is constant through all cell types. The shortcut for completing a form is Alt + F4. Therefore, transferring the formula from D49 into another cell would results in the same conclusion.
To know more about formulation visit :-
https://brainly.com/question/15374128
#SPJ4
A customer seeks to buy a new computer for a private use at home.The customer primarily needs the computer to use the Microsoft PowerPoint application for the purpose of practice presentation skills.As a sales person what size hard disc would you recommend and why?
Answers
Answer:
The most common size for desktop hard drives is 3.5 inches, they tend to be faster and more reliable, and have more capacity. But they also make more noise.
Explanation:
If you are continually deleting and installing programs or creating content, the disc must have good reliability.
Keep in mind that larger hard drives are also a little slower, so it is preferable to opt for two smaller ones. Large hard drives are partitioned so there is no problem gettin
chbdg good performance, but if you put everything on one big disk and it breaks, you will lose everything.
If you buy 2 small disks, check that the motherboard does not limit the speed of a second hard disk.
in designing loops, we need to consider both the loop control structure and the loop body. group of answer choices true false
Answers
The given statement "in designing loops, we need to consider both the loop control structure and the loop body. " is true because when creating loops, it is necessary to take into account both the loop control structure and the loop body.
The loop control structure determines how many times the loop will iterate and under what conditions it will terminate. This can include elements such as the initial value of the loop counter, the condition for continuing the loop, and the way the loop counter is updated at each iteration. The loop body, on the other hand, defines the actions that will be performed on each iteration of the loop. This can include calculations, data manipulation, input/output operations, and other tasks that need to be performed repeatedly.
Both the control structure and the body of the loop are important considerations in designing efficient and effective loops.
You can learn more about loops at
https://brainly.com/question/26098908
#SPJ11
In a voice over IP setup (VoIP), what kind of device converts signals from a campus's analog phone equipment into IP data that can travel over a phone company's analog telephone lines
Answers
Answer:
VoIP gateway
Explanation:
A VoIP stands for the voice over IP. The VoIP gateway is defined as a hardware device which is used to convert the telephony traffic into the packets of data that is used for transmission over the internet. It acts as the bridge and connects the VoIP with the worlds of the legacy telephony.
In a VoIP setup, the signals form the analog phone of the campus equipment are converted to the IP data which can travel over the analog telephone lines of the phone company.
Read each question below. Then, using the drop-down menus, decide if it represents the purpose, construction, or support aspect of choosing a website host.
Will the website be built by a programmer at a company?
What type of content will be on the website?
Will the website be used to share family pictures or as a professional site for posting news?
Will customers be making secure transactions on the website?
How extensive of a control panel, or location of login and website control, will be needed?
Answers
Answer:
ConstructionPurposePurposeSupportConstructionExplanation:
Will the website be built by a programmer at a company? construction
What type of content will be on the website? purpose
Will the website be used to share family pictures or as a professional site for posting news? purpose
Will customers be making secure transactions on the website? support
How extensive of a control panel, or location of login and website control, will be needed? Construction
__________________________________________________
Prove by induction that the height of a perfect binary tree is log(n+1)-1. Recall that a perfect binary tree is a binary tree in which all interior nodes have two children and all leaves have the same depth.
Answers
To prove that the height of a perfect binary tree is log(n+1)-1, we will use mathematical induction. First, we will show that this formula holds for a tree with only one node (n=1). In this case, the height of the tree is 0, and log(n+1)-1 equals 0, so the formula holds.
Next, we will assume that the formula holds for a perfect binary tree with k nodes, and show that it also holds for a tree with k+1 nodes. To do this, we will add one node to the tree, which must be added as a leaf node. This means that the height of the tree increases by 1. By the induction hypothesis, the height of the original tree was log(k+1)-1. Adding a leaf node does not affect the depth of any other nodes in the tree, so the height of the new tree is log(k+2)-1, which is equal to log((k+1)+1)-1. Therefore, the formula holds for a perfect binary tree with k+1 nodes.
By the principle of mathematical induction, we have shown that the formula holds for all perfect binary trees.
To prove by induction that the height of a perfect binary tree is log(n+1)-1, we need to establish two steps: base case and induction step.
Base case: For n = 1 (one node), height = log(1+1)-1 = log(2)-1 = 0, which is correct as the single node tree has height 0.
Induction step: Assume the height of a perfect binary tree with n nodes is log(n+1)-1. Now, consider a tree with 2n+1 nodes (one extra level). This new tree has double the nodes plus one additional root. The height increases by 1.
New height = log(2n+1+1)-1 = log(2(n+1))-1 = log(n+1)+log(2)-1 = (log(n+1)-1)+1.
This shows the height of a perfect binary tree with 2n+1 nodes is log(n+1)-1 +1, maintaining the relationship as we add a level, proving the statement by induction.
To know more about induction visit-
https://brainly.com/question/18575018
#SPJ11
What are the benefits of building redundancy into a network?
Answers
The advantages of incorporating redundancy into a network are that they can offer backups in the event of a problem or in the event that one communication line is blocked.
What are the advantages of including redundancy in a network and what are the possible drawbacks?It is a technique for expanding the network's communication channels and network devices. It may also reduce the likelihood of serious data failure. It is possible to think of network redundancy as a backup mechanism to assist stop possibly more significant issues.
The primary advantage of including redundancy in a network is?By offering several channels for traffic, network redundancy ensures that data may continue to flow even in the case of a failure. In other words, more redundancy equates to more reliability. Furthermore, it aids in distributed site management.
To know more about network visit:-
https://brainly.com/question/17880618
#SPJ4
(50 POINTS!) Select the correct answer.
A website sells illegal and counterfeited materials. According to which law can the US Attorney General seek a court order to request service providers to block access to that website?
A. Copyright Act
B. Digital Millennium Act
C. SOPA
D. PIPA
Answers
Answer:
Digital Millennium Act
Explanation:
not sure
Answer:
Copyright Act
Explanation:
I'm not completely sure, but the copyright act is the original creators of products and anyone they give authorization to are the only ones with the exclusive right to reproduce the work.
Select the correct navigational path to add a chart to an Excel worksheet.
Select the range of cells.
Click the __ Formula tab on the ribbon and look in the
group.
Click the dialog box launcher and then the __ tab.
The charts are then listed by category. Select the one you wish to use. Click OK.
Answers
To use a chart template that has been saved, choose the proper navigation route. Choose the cell range. Look in the group by selecting the ___ tab on the ribbon.
What is chart in excel ?In Excel Spreadsheets, a graph is a common name for a chart. Data from a spreadsheet that is represented visually can be more understood than data that is only seen as numbers. With the use of a chart, you may visualise data in a number of various chart types, including bar, column, pie, line, area, donut, scatter, surface, and radar charts. It is simple to make a chart with Excel. In Excel, a chart is useful you can use to visually convey data. Charts make it considerably simpler to display comparisons and patterns and let your audience understand the significance of the numbers. You will learn how to add charts and adjust them in this session so that they effectively convey information.
To know more about chart in excel visit:
https://brainly.com/question/29790710
#SPJ1
Answer: insert, charts, all charts
Explanation:
just did it
Pipeline Concept:
Break instruction execution ____ ____________.
Answers
Pipeline Concept:
Break instruction execution into stages.
The pipeline concept in computer architecture refers to a technique used to improve the performance of the processor by breaking down the instruction execution into several stages.
Each stage is designed to perform a specific task, and the output of one stage is passed as input to the next stage, forming a pipeline.
The stages may include fetching the instruction, decoding it, executing it, and storing the result.
However, there can be situations where the pipeline needs to be halted, such as when a branch instruction is encountered, and the next instruction to execute is not known yet.
In such cases, the pipeline is broken, and the execution of instructions is temporarily halted until the branch is resolved.
For more such questions on Pipeline Concept:
https://brainly.com/question/30089658
#SPJ11
What is the result when you run the following program?
print(2 + 7)
print("3 + 1")
Answers
#1
No quotes means program will add the numbers .\(\tt print (2+7)\)
\(\tt 9\)
#2
Here there is a double quoteProgram will print inside\(\tt print ("3+1")\)
\(\tt 3+1\)
How many things can a computer compare at one time?
Answers
Answer: billion of items at one time
Explanation: The computer is very capable of comparing items bulk at one time
Which of these lights is NOT part of the standard three-point lighting setup?
key light
backlight
fill light
background light
Answers
Answer:
i believe background lighting