You are the wireless network administrator for your organization. As the size of the organization has grown, you've decided to upgrade your wireless network to use 802.1x authentication instead of using preshared keys. To do this, you need to configure a RADIUS server and RADIUS clients. You want the server and the clients to mutually authenticate with each other. What should you do
Answers
To configure mutual authentication using 802.1x for a RADIUS server and clients, follow these steps:
Choose RADIUS server software supporting 802.1x, install it, and configure it to use an X.509 digital certificate for authentication. Configure the server to trust the certificate authorities (CAs) issuing client certificates. For each RADIUS client, obtain or generate an X.509 digital certificate, install the RADIUS client software, and configure it with the server's IP address, shared secret, and CA information.
Import the server's CA certificate onto each client device. Update network devices to enable 802.1x authentication, specify the RADIUS server, and shared secret. Define access policies on the server and test the authentication and connectivity. Monitor logs for issues and troubleshoot as needed.
To know more about Server related question visit:
https://brainly.com/question/30168195
#SPJ11
Related Questions
which is true? question 4 options: a program with multiple classes is contained in a single file a programmer must decide what a class contains and does class data are normally public a programmer should sketch a class while writing the code
Answers
This statement, "A programmer must decide what a class contains and does," is true.
Is it possible to have numerous classes in one Python file?The building blocks of Python libraries and other applications are either modules or collections of modules. There is no cap on the number of classes that can be contained in a file or module.
What number of classes make up a single program?A program can define any number of classes as long as they all have unique names. If a public class exists in Java, it must have the same name as the file.
To know more about class visit :-
https://brainly.com/question/29846696
#SPJ4
This statement, "A programmer must decide what a class contains and does," is true.
Is it possible to have numerous classes in one Python file?The building blocks of Python libraries and other applications are either modules or collections of modules. A file or module can have an unlimited number of classes in it.
Python code is organised into "modules" (groups of related files) and "packages" (collections of related modules).
One or more closely related classes may make up a module, which is a standalone unit. Prior to reading, using, maintaining, and, if necessary, extending modules, they must first be imported. A module is therefore a unit or reuse.
The rule is that the unit of reuse is a module. The building blocks of Python libraries and other applications are either modules or collections of modules.
In how many classes does a single programme consist?A program can define any number of classes as long as they all have unique names. If a public class exists in Java, it must have the same name as the file.
To know more about class visit :-
brainly.com/question/29846696
#SPJ4
The option to send a publication in an e-mail is available in the _____ tab.
File
Home
View
Review
Answers
Answer:
File
Explanation:
Ocean Levels
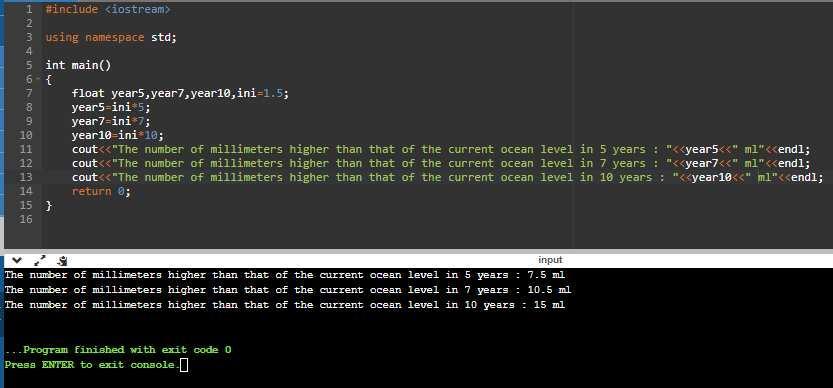
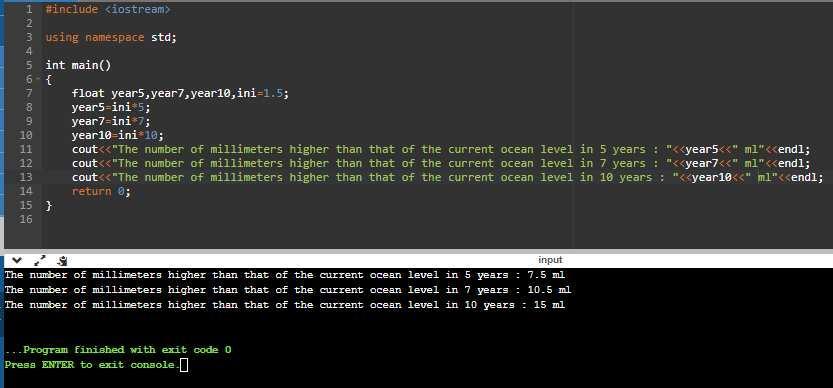
Assuming the ocean s level is currently rising at about 1.5 millimeters per year, write a program that displays:
* The number of millimeters higher than the current level that the ocean s level will be in 5 years.
* The number of millimeters higher than the current level that the ocean s level will be in 7 years..
* The number of millimeters higher than the current level that the ocean s level will be in 10 years.
Answers
The program is displayed in the images attached below:
#include <iostream>
using namespace std;
int main()
{
float year5,year7,year10,ini=1.5;
year5=ini*5;
year7=ini*7;
year10=ini*10;
cout<<"The number of millimeters higher than that of the current ocean level in 5 years: "<<year5<<" ml"<<endl;
cout<<"The number of millimeters higher than that of the current ocean level in 7 years: "<<year7<<" ml"<<endl;
cout<<"The number of millimeters higher than that of the current ocean level in 10 years: "<<year10<<" ml"<<endl;
return 0;
Learn more about programming here:
https://brainly.com/question/14368396
#SPJ4
Project manager Kevin has to create a project team organizational chart. Which activity should he perform before creating this chart?

Answers
Answer: C
Explanation: Allocating roles to project team members.
you need to develop and install a sideloaded app on the windows 10 professional systems within your organization. you plan to use a certificate purchased from symantec to digitally sign the app prior to sideloading it on your windows systems
Answers
The truth regarding this process is that You do not need to manually import the certificate used to digitally sign the app on each system.
What is the windows systemsTo create and install a sideloaded app on Windows 10 Professional systems in your organization, you can Create the app.
Use the tools and languages you like to make the app you want. Make sure the app follows the rules and standards for installing on Windows 10. It's crucial to ensure the security and authenticity of the certificate used for signing the app.
Read more about windows systems here:
https://brainly.com/question/27764853
#SPJ4
You need to develop and install a sideloaded app on the Windows 10 Professional systems within your organization. You plan to use a certificate purchased from Symantec to digitally sign the app prior to sideloading it on your Windows systems. what is true regarding this process?
A coenzyme is: An inactive enzyme. Any enzyme containing a B vitamin. A molecule that combines with and activates an enzyme. A molecule such as a B-vitamin that is released as a by-product of enzymatic reactions.
Answers
A coenzyme is C: A molecule that combines with and activates an enzyme.
Coenzymes are organic molecules that work in conjunction with enzymes to facilitate and enhance their catalytic activity. They bind to enzymes and play an essential role in the enzyme's function, often acting as carriers of specific chemical groups or electrons during enzymatic reactions. Coenzymes are not enzymes themselves but are necessary for the proper functioning of enzymes.
Therefore, the correct answer is (C) that a coenzyme is a molecule that combines with and activates an enzyme. It helps the enzyme carry out its specific biochemical reactions by providing necessary chemical components or aiding in the transfer of molecules or electrons.
You can learn more about coenzyme at
brainly.com/question/28901118
#SPJ11
List 8 things that online friends say and list 8 things that online fakes say.
Answers
Answer:
online friend
hi
hello
hahaha
how are you
how your day
i dont known
where are you
what are you doing
online fakes
are you serious
are you crazy
what do you want
firts of all
lets talk about later
~Online friends~
Lol
girl
heheh
wat
okk
You a Queen
u good man
jgjkggjglsgkhkbgls *Spamming you*
~Fake online friend~
Who asked?
Shut up
ok.
ok stop bragging.
I have to go my mom called me.
aw to bad
Hey can you send me money
Oh it's your birthday, I didn't know...- Oh you told me everyday this week, I forgot?
what do raichle's default mode network and corbetta's ventral attentional network have in common?
Answers
Answer: voluntary deployment of attention and the reorientation to unexpected events
Explanation:
Raichle's Default Mode Network and Corbetta's Ventral Attentional Network both have in common that they are large-scale brain networks involved in cognitive processing and attentional functions.
They are both activated in the human brain when people are at rest and not involved in any specific task. The default mode network is involved in self-reflection, introspection, and mind-wandering. On the other hand, the ventral attentional network is responsible for detecting and reacting to sensory stimuli that have significant emotional, social, or motivational implications.
Both these networks have been associated with cognitive flexibility and creativity. They work together to coordinate human behavior and maintain a balance between internal and external stimuli.
Learn more about brain networks: https://brainly.com/question/29669975
#SPJ11
question 2 fill in the blank: a data analytics team uses to indicate consistent naming conventions for a project. this is an example of using data about data.
Answers
Explanation:
A data analytics team using consistent naming conventions for a project is an example of using data about data, also known as metadata. Metadata is data that provides information about other data, such as its structure, format, and content. In this case, the consistent naming conventions for the project can be considered metadata because they provide information about the data being used in the project, helping to ensure that it is organized and understood properly.
Therefore, the correct answer is:
A data analytics team uses consistent naming conventions to indicate metadata for a project.
use the drop-down menus to complete the steps for using find and replace commands. 1. make sure you have not selected any particular cell. 2. under the (insert, home, review, formulas) tab, go to the (alignment, cells, editing, styles) command group. 3. choose the (go to, replace, comments, formulas) option 4. type in the information you want to find and what it should be replaced with. to make sure all instances are changed at once, select (replace, replace all, find all, find next)
Answers
Through line biomechanics concentration and observation magic if International Society of Biomechanics in sports.
What is "International Society of Biomechanics in sports"?The recently developed professional association in biomechanics is the "International Society of Biomechanics in sports".It is the professional association in bio-mechanics.
It is an international society which is dedicated to bio-mechanics to sports. The main purpose of the society is to understand and study the human movement and its relation to sport bio-mechanics. They provide information regarding bio-mechanics in sports.
Therefore, Through line biomechanics concentration and observation magic if International Society of Biomechanics in sports.
Learn more about biomechanics on:
https://brainly.com/question/13898117
#SPJ1
Answer:
The correct answers are Home, Editing, Replace, and Replace All
For what two reasons is it important to add comments to a program?
Answers
What does this mean?

Answers
Answer:
The network that the platform is running on is down. Wait about 30min, and then try again. You can also restart your device.
Explanation:
This used to happen to me all the time during school, but when I restarted my computer it always fixed it!
Select the correct answer.
What helps the project team to identify the latest software build?
A.
defect
B.
version number
C.
test plan
D.
test environment
E.
hardware
Answers
Answer:
B version number
Explanation:
You have two Windows Server 2016 computers with the Hyper-V role installed. Both computers have two hard drives, one for the system volume and the other for data. One server, HyperVTest, is going to be used mainly for testing and what-if scenarios, and its data drive is 250 GB. You estimate that you might have 8 or 10 VMs configured on HyperVTest with two or three running at the same time. Each test VM has disk requirements ranging from about 30 GB to 50 GB. The other server, HyperVApp, runs in the data center with production VMs installed. Its data drive is 500 GB. You expect two VMs to run on HyperVApp, each needing about 150 GB to 200 GB of disk space. Both are expected to run fairly disk-intensive applications. Given this environment, describe how you would configure the virtual disks for the VMs on both servers.
Answers
The virtual disk configuration for the VMs on both servers in this environment is shown below.
In the Hyper V Test,
Since there will be two or three virtual machines running at once, each of which needs between 30 and 50 GB of the total 250 GB of disk space available,
What is virtual disks?Setting up 5 virtual disks, each 50 GB in size.
2 VMs each have a 50 GB virtual drive assigned to them.
The above setup was chosen because running three VMs with various virtual disks assigned to them will not pose an issue when two or three VMs are running concurrently and sharing the same virtual disk. This is because the applications are disk-intensive.
To learn more about virtual disks refer to:
https://brainly.com/question/28851994
#SPJ1
Given this environment, the virtual disk configuration for the VMs on both servers is shown below. Because two or three VMs will be running at the same time, and each VM has disk requirements ranging from 30 to 50 GB of total disk space of 250 GB.
What is Hyper V Test?While there are several methods for testing new virtual machine updates, Hyper-V allows desktop administrators to add multiple virtual machines to a single desktop and run tests. The Hyper-V virtualization technology is included in many versions of Windows 10. Hyper-V allows virtualized computer systems to run on top of a physical host. These virtualized systems can be used and managed in the same way that physical computer systems can, despite the fact that they exist in a virtualized and isolated environment. To monitor the utilization of a processor, memory, interface, physical disk, and other hardware, use Performance Monitor (perfmon) on a Hyper-V host and the appropriate counters. On Windows systems, the perfmon utility is widely used for performance troubleshooting.Therefore,
Configuration:
Creating 5 Virtual disks of 50 GB each.
1 virtual disk of 50 GB is assigned to 2 VM.
The above configuration is because since two or three VM will be running at the same time and using the same virtual disk will cause a problem since the applications are disk intensive, running three VMs with different virtual disks assigned to them, will not cause a problem.
For Hyper V App,
Two VM will run at the same time, and the disk requirement is 150 - 200 GB of 500 GB total disk space.
Configuration:
Creating 2 virtual disks of 200 GB each with dynamic Extension and assigning each one to a single VM will do the trick.
Since only two VMs are run here, the disk space can be separated.
To learn more about Hyper V Test, refer to:
https://brainly.com/question/14005847
#SPJ1
why does low air pressure usually indicate bad weather?
Answers
Areas with high pressure typically have calm, fair weather. Areas with low pressure have comparatively thin atmospheres.
Why does poor weather typically signal low air pressure?Low pressure causes active weather. The atmosphere becomes unstable when the air rises since it is lighter than the surrounding air masses. When the air pressure increases, water vapor in the air condenses, creating clouds and rain, among other things. Both severe weather and active weather, such as wind and rain, are brought on by low pressure systems.
What type of weather lowers air pressure?Low-pressure areas are typically associated with bad weather, while high-pressure areas are associated with calmer winds and clear skies (such as cloudy, windy, with potential for rain or storms).
To know more about low air pressure visit:-
https://brainly.com/question/2194071
#SPJ4
you manage several windows workstations in your domain. you want to configure a gpo that will make them prompt for additional credentials whenever a sensitive action is taken. what should you do? answer configure user rights assignment settings. configure restricted groups settings. configure user account control (uac) settings. configure windows firewall with advanced security settings.
Answers
By configuring the UAC settings in the GPO, you will make the Windows workstations in your Domain prompt for additional credentials when sensitive actions are taken, ensuring a higher level of security.
To configure a Group Policy Object (GPO) that prompts for additional credentials whenever a sensitive action is taken on your Windows workstations in your domain, you should follow these steps:
1. Configure User Account Control (UAC) settings: UAC settings ensure that users are prompted for additional credentials when performing sensitive actions, like installing software or changing system settings. To configure UAC settings in the GPO, follow these steps:
a. Open the Group Policy Management Console (GPMC).
b. Right-click on the desired domain or organizational unit (OU), and select "Create a GPO in this domain, and link it here."
c. Name the new GPO, and click "OK."
d. Right-click on the newly created GPO, and select "Edit."
e. Navigate to "Computer Configuration" > "Policies" > "Windows Settings" > "Security Settings" > "Local Policies" > "Security Options."
f. Locate the UAC settings, such as "User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode." Configure the settings as desired to enforce the additional credential prompts.
2. The other options, such as User Rights Assignment settings, Restricted Groups settings, and Windows Firewall with Advanced Security settings, are not directly related to prompting for additional credentials during sensitive actions. These settings control different aspects of system security, like user permissions, group membership, and network protection, respectively.
By configuring the UAC settings in the GPO, you will make the Windows workstations in your domain prompt for additional credentials when sensitive actions are taken, ensuring a higher level of security.
To Learn More About Domain
https://brainly.com/question/19268299
SPJ11
ASAP
There are two competing scientific theories that try to explain the illusion of animation. Which of these answers is NOT one of the competing theories?
Persistence of Vision
Image-permanence
Phi Phenomenon
The first who answers correct will get brainlest and those that are incorrected will be marked with a red flag.
Answers
what does a technician need in order to make changes to software installed on the computer of a customer?
Answers
A technician needs the customer's permission before making any changes to a computer.
What kind of work does a level one technician at a call center typically do?A level one technician's main duty is to obtain information from the customer. All of the data must be accurately entered into the work order by the level one technician.
Which of the following software launches first when you turn on your laptop?computing device. When a computer is turned on, an operating system, a specific program, must be started. By handling the intricate logistics of hardware management, the operating system's job is to make other computer applications more functional.
To know more about technician visit:-
https://brainly.com/question/14290207
#SPJ1
por que se dice que las TIC´S son las integracion de las TI y las TC?
Answers
La respuesta correcta para esta pregunta abierta es la siguiente.
A pesar de que no se anexan opciones o incisos para responder, podemos comentar lo siguiente.
Se dice que las TIC´S son las integración de las TI y las TC porque ambas actividades se han integrado o fusionado en una solo concepto al momento de juntar las herramientas tecnológicas para almacenar, procesar y mandar información a través de los recursos tecnológicos utilizando los canales o recursos de los medios masivas de comunicación como lo son las redes satelitales o las comunicaciones vía microondas.
Al fusionarse las TI (Tecnologías de la Información) con las TC (Tecnologías de Comunicación), se maximiza la capacidad de enviar una mayor cantidad de información al momento a diferentes lugares del planeta.
Nora has shared a document with others, and she needs to be able to easily identify when others are modifying the
documents and where those modifications have been made.
Which feature should Nora use?
Password Protection
OneDrive storage
Track Changes
Protected View
Answers
Answer:
C, Track Changes
Explanation:
Answer:
C. Track Changes
Explanation:
hope this helps :)
A device that allows you to talk to someone else in another location, is called?
Answers
A device that allows you to talk to someone else in another location is called a telephone.
Telephones are electronic devices that use a network of wires, cables, and other infrastructure to transmit the human voice over long distances. These devices have been in use for over a century and have undergone significant changes in terms of design and functionality. Modern telephones can be classified into several types, such as landlines, mobile phones, and VoIP (Voice over Internet Protocol) phones.
Landlines are connected to the telephone network via a wired connection, mobile phones use wireless networks, and VoIP phones use an internet connection for communication. Telephones are widely used for personal and professional communication and have become an essential part of our daily lives.
Learn more about mobile phones here: brainly.com/question/23433108
#SPJ4
When companies charge different prices for the same product, they're using
A. behavioral shopping.
B. dynamic pricing.
C. targeted advertising.
D. fair pricing.
Answers
Answer: When companies charge different
prices for the same product, they're using
B.) Dynamic Pricing
Is the most accurate
Explanation: If a firm can find a way to charge every customer the price he/she values a good at, the firm can capture more profits than it could with a single price, in a given market.
what is a type of system software that allows a user to perform maintenance type tasks
Answers
Answer:
Computer
Explanation:
The type of system software that allows a user to perform maintenance-type tasks is a computer.
A computer has many programs and operating systems.
what is the reason that an isp commonly assigns a dhcp address to a wireless router in a soho environment?
Answers
A business manages the IP address distribution for employee workstations using DHCP. Small businesses that are frequently operated out of homes or even tiny offices are referred to as SOHOs.
Why does a wireless router frequently receive a DHCP address from an ISP in a SOHO context for convenience in managing IP addresses?The ISP commonly uses DHCP to assign the IP address between the wireless router and ISP site. In this system, IP addresses are dynamically assigned to clients, making it simple to assign the assigned IP address to another client in the event that a dropped client.
What function does the WAN DHCP IP address serve?It directs the internet to send data to places like a mailing address on a package.
To know more about IP address visit:-
brainly.com/question/16011753
#SPJ1
Create a protocol that will solve the problems you saw with Protocol 1 by doing some error-checking. The sender should be able to construct a single multi-packet message that is sent at once. Afterwards they can keep communicating to fix any errors in the transmission. Things to consider:
Answers
To construct and send, open a network environment a single multi-packet message, simply click "Add Packet" and then click "Send at Once".
How will the receiver know the order of the packets or if any are missing?If the text or message sent does not make any reading sense, or if certain words are jumbled and out of place, then it is clear that something is wrong.
If the messages arrive in a coherent fashion, then the packet was fully received.
How will the receiver request missed packets and what will the sender do in response?
Where the users are familiar with the Transmission Control Protocol, lost packets can be detected when there is a timeout. Lost packets are referred to as Dropped packets.
Please note that the Problem to be solved from Protocol 1 is not provided hence the general answers.
Learn more about protocol at:
https://brainly.com/question/27581708
#SPJ4
Full question:
Protocol 2 - Check for Errors
Create a protocol that will solve the problems you saw with Protocol 1 by doing some error-checking. The sender
should be able to construct a single multi-packet message that is sent at once. Afterwards they can keep
communicating to fix any errors in the transmission. Things to consider:
How will the receiver know the order of the packets or if any are missing?
How will the receiver request missing packets and what will the sender do in response?
How will both sender and receiver know the full message arrived successfully?
how data driven software can improve the reliability and effectiveness of software
Answers
Data-driven design makes linked product data streams simpler, assisting manufacturers in making sense of massive data.
By using this knowledge, they may improve product quality and reliability by making well-informed design decisions. It is feasible to discern patterns and spot concerns well before they affect the end user thanks to an AI-powered, data-driven strategy. Instead of spending time putting out fires, developers may fix problems and resume producing creative code with the help of these proactive tools. A method of software engineering known as "data-driven development" uses data to direct the development process. It entails choosing and keeping track of metrics or key performance indicators (KPIs) that might help you better understand your product and make it better moving forward.
Learn more about data here-
https://brainly.com/question/17355880
#SPJ4
What’s y’all’s favourite movie??? Mines Us

Answers
Answer:
Depends halloween movie, chrismas, scary
which of the following types of storage would you recommend if someone needed a hard drive with fast data access and a small outline?a. Magnetic hard driveb. Solid-state hard drivec. Flash drived. Optical drive
Answers
If someone needs a hard drive with fast data access and a small outline, the type of storage that should be recommended is a Solid-state hard drive (SSD). The correct answer is B.
An SSD, also known as a solid-state drive, is a storage device that employs flash memory to store data. It is smaller in size and faster than a standard hard disk drive (HDD). It has a faster read/write speed than an HDD and consumes less energy than an HDD because it does not have any moving parts.
A magnetic hard drive has moving parts and is slower than an SSD. Optical drives, on the other hand, are used to read data from CDs, DVDs, and Blu-ray discs, and are not suitable for storage purposes. Flash drives are often used for data transfer and storage, but they have a lower storage capacity than an SSD.
Therefore, if someone needed a hard drive with fast data access and a small outline, the type of storage that would be recommended is a Solid-state hard drive (SSD).
You can learn more about Solid-state hard drive (SSD) at
https://brainly.com/question/28476555
#SPJ11
ipv6 supports types of auto-configuration: stateful auto-configuration and stateless auto-configuration. which of the following is a true statement? stateful auto-configuration is more secure than stateless auto-configuration. stateless auto-configuration is more secure than stateful auto-configuration. stateless auto-configuration is more efficient than stateful auto-configuration. stateless auto-configuration requires needs dynamic host configuration protocol for ipv6.
Answers
The correct statement is: Stateless auto-configuration is more efficient than stateful auto-configuration.
Stateless auto-configuration in IPv6 allows hosts to configure their network settings without the need for a central server. Hosts use information from router advertisements to derive their IPv6 addresses and other network parameters. This process is efficient as it eliminates the need for a central server to assign addresses to each host.
In terms of security, neither stateful nor stateless auto-configuration is inherently more secure than the other. Security measures can be implemented in both types of auto-configuration to ensure the integrity and authenticity of the configuration information.
Stateless auto-configuration does not require the Dynamic Host Configuration Protocol for IPv6 (DHCPv6) to function. However, DHCPv6 can be used in conjunction with stateless auto-configuration to provide additional configuration options.
Learn more about IPv6 auto-configuration here:
https://brainly.com/question/28334036
#SPJ11
Click this link to view O*NET’s Tasks section for Computer Programmers. Note that common tasks are listed toward the top, and less common tasks are listed toward the bottom. According to O*NET, what common tasks are performed by Computer Programmers? Check all that apply.
Negotiating costs and payments with customers
Conducting trial runs of programs and software applications
Writing, updating, and maintaining programs or software packages
interviewing and hiring programming workers
Marketing and selling software packages
Correcting errors by making changes and rechecking a program
Answers
The options that applies are:
Conducting trial runs of programs and software applicationsWriting, updating, and maintaining programs or software packagesCorrecting errors by making changes and rechecking a programWhat is ONET?O*NET is known to be an OnLine app or web that gives a good descriptions of how the world work and it is often used by job seekers, workforce development and others.
Therefore, based on the above statement about ONET, The options that applies are:
Conducting trial runs of programs and software applicationsWriting, updating, and maintaining programs or software packagesCorrecting errors by making changes and rechecking a programLearn more about ONET from
https://brainly.com/question/5605847
#SPJ1
Answer:
conducting trial runs of programs and software applications
writing, updating, and maintaining programs or software packages
correcting errors by making changes and rechecking a program
good luck.