You work as the IT administrator for a small business and are responsible for the corporate network. You have two servers and a DNS server that use static IP addresses on the 192.168.0.0/24 subnet. You plan to install three more servers soon, so you need to create DNS records for these servers on the CorpDC server.
Answers
As the IT administrator for the small business, it is important to ensure that the corporate network is running smoothly. With the addition of three more servers, it is necessary to create DNS records for these servers on the CorpDC server.
This can be done by accessing the DNS management console on the CorpDC server and adding the new servers as host records. Make sure to assign them static IP addresses on the 192.168.0.0/24 subnet and configure the necessary DNS records to ensure proper communication and connectivity within the network. This will ensure that all servers are properly identified and accessible on the network.
Hi! As an IT administrator for a small business, you will need to create DNS records for the three new servers on the CorpDC server. To do this, follow these steps:1. Log in to the CorpDC server as an administrator.
2. Open the DNS management console.
3. Navigate to the appropriate DNS zone for your network (e.g., yourdomain.com).
4. Right-click on the zone and select "New Host (A or AAAA)".
5. Enter the hostname and static IP address for each new server, ensuring they are within the 192.168.0.0/24 subnet.
6. Click "Add Host" to create the DNS record for each server.
7. Once all records are created, verify the changes by using tools such as "nslookup" or "ping" with the hostnames of the new servers.By following these steps, you will successfully create DNS records for the new servers on the CorpDC server, ensuring their proper integration into your corporate network.
To learn more about administrator click on the link below:
brainly.com/question/29994801
#SPJ11
Related Questions
In which of the following cases is the application of a nested loop not justified? When comparing two lists of integers When formatting a long text to make it more readable
When locating the smallest number in a list of integers When processing data in nested data structures
Answers
The nested loop can be used When processing data in nested data structures. The correct option is D.
What is nested loop?A nested loop is a loop statement that is contained within another loop statement. That is why nested loops are also called "loop inside loops". Any number of loops can be defined within another loop.
Nested loops are useful when you need to repeat some action on the data in the outer loop for each pass through it. For example, you could read a file line by line and count how many times the word "the" appears on each line.
A nested loop is a loop within a loop, such as an inner loop within the body of an outer loop.
When processing data in nested data structures, the nested loop can be used.
Thus, the correct option is D.
For more details regarding nested loop, visit:
https://brainly.com/question/29532999
#SPJ2
what is the most important person and why
Answers
Answer:
me myself and i. i am the most important person because i am 100 times better than u
Explanation:
give me brainliest please
` grave or tilda key (just to the left of the #1)
Answers
The grave or tilde key, located just to the left of the #1 key on a standard keyboard, is a versatile key that has multiple uses in computing. When pressed on its own, the key typically creates a grave accent (`), which is a diacritical mark used in some languages to indicate pronunciation or stress.
In programming languages, the grave key is often used to indicate string literals or special characters. For example, in Python, the backtick (a variant of the grave key) is used to indicate a raw string literal.
The tilde (~) is another character that can be created by pressing the same key with the shift key held down. In computing, the tilde is often used to indicate a user's home directory in Unix-based operating systems, and can also be used as a shorthand for negation or approximation.
Overall, the grave or tilde key may not be used as frequently as other keys on the keyboard, but it still has important uses in various contexts, particularly in programming and linguistics.
You can learn more about programming languages at: brainly.com/question/23959041
#SPJ11
pls help quick... will mark brainliest...

Answers
Answer:
the answer is c
Explanation:
So my computer has be clicking random things and opening things. It’s been happening for a few days and I want to know if it’s a hacker or something wronging with the computer (I don’t have a mouse) so it’s not auto clicking
Answers
Viruses and malware are common and can have drastically negative results on your computer and life.
You can often tell that your computer is infected because it acts weird or slow.
Active antivirus software is a good way to prevent these problems.
What is the prefix for the host address 2001:db8:bc15:a:12ab::1/64? the network portion, or prefix, of an ipv6 address is identified through the prefix length. a /64 prefix length indicates that the first 64 bits of the ipv6 address is the network portion. hence the prefix is 2001:db8:bc15:a.
Answers
An IPv6 address's prefix length serves as a means of identifying the network portion, or prefix. The network portion of an IPv6 address is the first 64 bits, as indicated by a prefix length of /64. The prefix is 2001:DB8:BC15:A as a result.
The IPv6 address 2001 db8 is associated with what prefix?A unique IPv6 prefix that is used only for documentation examples is 2001:db8::/32. Additionally, you can specify a subnet prefix, which tells a router how the network is organized internally. The subnet prefix for the example IPv6 address is as follows. The subnet prefix is always 64 bits long.
Describe the IPv6 prefix.The idea of IPv6 prefixes is comparable to IPv4 subnetting. When an IPv6 address has a prefix, it is written as an IPv6 address followed by a decimal number that indicates how many bits in the address make up the prefix.
To know more about network visit:-
brainly.com/question/29350844
#SPJ4
What technology that was developed in the early 1880s was used for both mining reclaiming land in the california delta?.
Answers
The technology that was developed in the early 1880s ,that was used for both mining reclaiming land in the california delta is hydraulic mining.
A type of mining known as hydraulic mining involves moving silt or displacing rock material with the help of high-pressure water jets. The resulting water-sediment slurry from placer mining for gold or tin is sent through sluice boxes to extract the gold. Kaolin and coal mining both use it.
Ancient Roman practices that employed water to remove soft subsurface minerals gave rise to hydraulic mining. Its contemporary form, which makes use of pressured water jets generated by a nozzle known as a "monitor," was developed in the 1850s in the United States during the California Gold Rush. Despite being effective in extracting gold-rich minerals, the process caused significant environmental harm due to increased flooding and erosion as well as sediment blocking water ways and covering farmland.
To know more about hydraulic mining click here:
https://brainly.com/question/13970465
#SPJ4
what feature is used on memory slots and modules to prevent modules from being inserted incorrectly?
Answers
Polarizing feature is used on memory slots and modules to prevent modules from being inserted incorrectly.
How does polarized function work?
They mostly clean up power supply as their main job (storage). Additionally, when they're connected together, they're used to stop DC in amplifier stages.
An option is a film or ceramic capacitor, although they are physically larger and do not have high capacitance values.
What is the name of the slot where memory modules are stored?
On your motherboard, RAM is installed in DIMM (dual in-line memory module) slots.
As a result, DIMM slots may sometimes be referred to as "RAM slots." Your motherboard's capacity for installing RAM increases with the number of DIMM slots it has.
Learn more about Polarizing feature
brainly.com/question/29753970
#SPJ4
~50 points~
how do you merge shapes in powerpoint
Answers
Answer:
Select the shapes to merge. Press and hold Shift to select multiple shapes. The Shape Format tab appears. ...
On the Shape Format tab, click Merge Shapes, and then pick the option you want. The order in which you select the shapes to merge may affect the options shown to you.Explanation:
Which science fiction author was born in the 1800s?
Frank Herbert, Robert Heinlein, Edgar Rice Burroughs, Isaac Asimov
Answers
Answer:
Edgar Rice Burroughs, known for his work in Science Fiction and Fantasy, was born in the 1800s.
Explanation:
Other Choices:
Frank Herbert was also a known Science Fiction writer, but he wasn't born until 1920.
Robert Heinlein was born in 1907 and also a well-published Science Fiction author and military officer.
Isaac Asimov, much like Frank Herbert, wasn't born until 1920 and contributed to the same field of literature.
d
5.
in the blanks. Compare your answers with your classmates' an
mnemonic codes
COBOL
1.
2. Assembly language is based on
3.
4.
Stat
SQL
is a language processor.
Compiler
is a high-level language.
number system consists of 10 digits.
is a fifth generation language.
Decimal
Answers
Answer:
1. COBOL: Common Business-Oriented Language
2. Assembly language is based on machine code.
3. Stat: Statistical Analysis System
4. SQL: Structured Query Language
5. Decimal: Decimal number system consists of 10 digits.
Mnemonic codes: Mnemonic codes are used to represent instructions or data in a more human-readable format, making it easier for programmers to remember and understand. Examples of mnemonic codes include ADD (addition), SUB (subtraction), and MOV (move). They are commonly used in assembly language programming.
Compiler: A compiler is a language processor that translates high-level programming code into machine code, which can be directly executed by a computer. It performs various tasks such as syntax analysis, optimization, and code generation.
High-level language: A high-level language is a programming language that is designed to be easier for humans to read, write, and understand. It provides a higher level of abstraction and is closer to natural language compared to low-level languages like assembly or machine code.
Fifth-generation language: A fifth-generation language (5GL) is a programming language that focuses on artificial intelligence and problem-solving using a high-level, declarative approach. It allows programmers to specify what needs to be done rather than how to do it. Examples of 5GLs include Prolog and OPS5.
What type of software has been developed to enable users to make use of the vast amount of data being collected and organized today?.
Answers
Answer:
The type of software that has been developed to enable users to make use of the vast amount of data being collected and organized today is Analytics software.
What is Software?
A set of instructions, data, or programs used to run computers and carry out specified activities is referred to as software. It is the inverse of hardware, which describes a computer's physical components. Software is a catch-all phrase for apps, scripts, and programs that execute on a device.
Analytics software is a sort of software that has been developed to allow users to make use of the large quantity of data that is being gathered and structured nowadays.
It is used to compute the performance of digital content and to convert business information into reports. Therefore
Explanation:
what are trends in GPS ?
Answers
Answer:
New Trends in GPS & Telematics in 2021 and Beyond - Rewire Security. Real-time location tracking systems for cars, vans, motorcycles, lorries, wired or plug & play options—battery-powered GPS tracking systems with magnets attached to flat metal surfaces such as containers.
Explanation:
provide an example of (a) a time period and (b) reporting periods that might be part of a service level agreement for your it department's wifi service.
Answers
A) Time period: The amount of time for which the Wi-Fi service should be available per day, week, or month is an example of a time period that may be included in an SLA. This is referred to as uptime. B) Reporting period: The IT department should have a reporting period for Wi-Fi service, which specifies how often they will report on the service's performance. For example, they may provide a report on a monthly or weekly basis.
A Service Level Agreement (SLA) for an IT department's Wi-Fi service would have specific time periods and reporting periods. Time period and reporting periods are important terms related to service level agreements.
An SLA is a document that outlines the level of service a customer should expect from a service provider. In this case, the IT department is the service provider for Wi-Fi service. For example, the IT department may guarantee that the Wi-Fi service will be available 99% of the time in a given month. The remaining 1% is allowed for maintenance and upgrades.
This report should include uptime, bandwidth usage, user access, and any other relevant data. This will ensure that the IT department is accountable for the level of service they provide.
You can learn more about Wi-Fi service at: brainly.com/question/14149909
#SPJ11
list 20 specific purpose of application software
Answers
Answer:
1. Word processing
2. Spreadsheet creation and analysis
3. Database management
4. Presentation creation and delivery
5. Graphic design and editing
6. Video editing
7. Music production
8. Web browsing
9. Email management
10. Project management
11. Time tracking and monitoring
12. Accounting and financial management
13. Inventory and supply chain management
14. Human resources management
15. Customer relationship management
16. Sales management
17. Marketing management
18. Education and training
19. Healthcare management
20. Scientific research and analysis
the maximum acceptable down time after a computer system failure is determined by a company's
Answers
The maximum acceptable downtime after a computer system failure is determined by a company's specific needs, industry standards, customer expectations, and potential financial and operational consequences.
The maximum acceptable downtime after a computer system failure is a critical factor that varies from company to company. It depends on various factors, such as the nature of the business, industry standards, customer expectations, and the potential financial and operational consequences of the downtime. For some businesses, even a few minutes of downtime can result in significant financial losses or reputational damage. In contrast, others may be able to tolerate longer periods of downtime without severe consequences. Therefore, each company must evaluate its specific needs and consider the impact of potential downtime on its operations and stakeholders to determine an acceptable threshold.
Learn more about company here:
https://brainly.com/question/19659292
#SPJ11
Why do companies collect information about consumers? A. Because they want to meet new friends on social networks B. Because they take consumers' best interests to heart C. Because they want to effectively advertise to consumers D. Because they are looking for good employees to hire
Answers
Answer:
C. Because they want to effectively advertise to consumers.
Explanation:
Companies collect info for more accurate advertisements, which are designed to make people interact with them more commonly.
Play a role of an IT employee and explain how you will solve
business problems and provide decision support for a school by
establishing a database.
Write it clearly. thank you!
Answers
As an IT employee, I would solve business problems and provide decision support for the school by establishing a database. A database would help in organizing and managing various school-related data effectively, enabling informed decision-making and streamlining processes.
To establish a database for the school, I would follow the following steps:
Requirement Gathering: I would meet with key stakeholders, such as school administrators, teachers, and staff, to understand their data management needs and identify the specific problems they are facing. This could include areas such as student records, attendance, academic performance, curriculum management, financial data, and more.Database Design: Based on the requirements gathered, I would design the database schema, which includes defining the tables, fields, and relationships between them. This step involves careful consideration of data normalization techniques to ensure efficient data storage and retrieval.Database Implementation: Using appropriate database management software, such as MySQL, Oracle, or Microsoft SQL Server, I would create the database and tables as per the design. I would also establish necessary security measures, such as user access controls and data encryption, to protect sensitive information.Data Migration and Integration: If the school already has existing data in different formats (e.g., spreadsheets, paper-based records), I would develop a strategy to migrate and integrate that data into the new database. This process may involve data cleansing, transformation, and validation to ensure accuracy and consistency.Application Development: Depending on the school's requirements, I may develop customized software applications or use existing solutions to interact with the database. These applications could include student information systems, attendance trackers, gradebook systems, or financial management tools. Integration with other existing systems, such as learning management systems or communication platforms, may also be considered.Training and Support: I would provide training sessions and documentation to school staff, ensuring they understand how to use the database effectively and efficiently. Ongoing support and maintenance would be provided to address any issues or evolving needs that may arise.By establishing a database for the school, we can centralize and organize various data sets, enabling efficient data management and decision-making processes. The database would improve data accuracy, accessibility, and integrity, leading to better insights and informed decision support for school administrators, teachers, and staff. It would streamline administrative tasks, enhance collaboration among different departments, and ultimately contribute to an improved overall school management system.
Learn more about database visit:
https://brainly.com/question/29412324
#SPJ11
You are writing an algorithm and want to tell the computer what to do if the
user does not perform an action. Which type of statement should you include
in your algorithm?
A. Return
B. When-if
C. If-else
D. And-or
Answers
Answer:
you are writing an algorithm and went to tell computer what to do If the return
The type of statement, i.e., if-else should be include in your algorithm. The correct option is C.
What is if-else statement?An "if-else" statement is a conditional statement that determines whether a particular condition is true or false and then executes different code based on the outcome of that evaluation.
An "if-else" statement could be used in the context of a user action to check whether the user has performed a specific action and then execute different code depending on whether the user has performed that action or not.
To exit a function and return a value to the calling code, use a "return" statement. A "when-if" statement and a "and-or" statement are not standard programming constructs and are rarely used in code.
Thus, the correct option is C.
For more details regarding algorithm, visit:
https://brainly.com/question/22984934
#SPJ7
Which of the following rules is most likely to be used in an AUP
Answers
An Acceptable Use Policy (AUP) typically includes a set of rules and guidelines that outline the proper and acceptable use of an organization's computer network, internet connection, and other technology resources.
What is an AUP?An Acceptable Use Policy (AUP) typically includes a set of rules and guidelines that outline the proper and acceptable use of an organization's computer network, internet connection, and other technology resources. The specific rules included in an AUP can vary depending on the organization, but some common rules that are likely to be included in an AUP are:
Prohibiting the use of the organization's technology resources for illegal activities, such as hacking or spreading malware.
Prohibiting the use of the organization's technology resources to harass or bully others.
Prohibiting the unauthorized access, use, or modification of the organization's technology resources or data.
Prohibiting the use of the organization's technology resources for personal or non-work-related activities.
Requiring users to keep their passwords secure and to change them regularly.
Requiring users to report any security incidents or suspicious activity to the organization's IT department.
Out of these rules, the most likely to be used in an AUP is the first rule, which prohibits the use of the organization's technology resources for illegal activities. This is because it is a fundamental rule that applies to all organizations and is essential for maintaining the security and integrity of the organization's technology resources. However, all of these rules are important and are likely to be included in an AUP to some extent.
To know more about AUP,visit:
https://brainly.com/question/24951641
#SPJ1
If a city is experiencing very high temperatures, what action would allow the city to become cooler?
Answers
Answer:
Explanation:
1. Shut off the air conditioners.
2. Have a picnic at the nearest park in the shade.
3. Go swimming
4. Sleep outside.
In an interview, you are asked to explain how gamification contributes to enterprise security. How should you reply? a. Recreational gaming helps secure an enterprise network by keeping the attacker engaged in harmless activities. b. Instructional gaming in an enterprise keeps suspicious employees entertained, preventing them from attacking. c. Instructional gaming can train employees on the details of different security risks while keeping them engaged. d. Recreational gaming can train employees on how to contain a physical threat at an enterprise.
Answers
Gamification contributes to enterprise security because C. Instructional games can train employees in the details of different security risks while keeping them engaged.
Why Gamification can Improve the Security Awareness?Gamification has been used by organizations to improve customer loyalty. For example, different levels of play can be reached by using the application to earn points, purchase certain products, or participate in the company's gamified programs. But elements of gamification can still be found in today's workplace. Gamification is used to improve HR functions (employee recruitment, onboarding, etc.) and to motivate customer service representatives or call center or similar department employees to increase productivity and engagement I can do it. Gamification not only increases employee motivation and engagement, but it also optimizes workflows and processes, attracts new talent, and can be used for educational purposes.
Learn more about gamification for security awareness https://brainly.com/question/29655904
#SPJ4
Parte de una ventana que contiene los comandos agrupados en pestañas....
Answers
Answer:
/
Explanation:
ITIL defines availability as the ability of an IT service or other configuration item to perform its agreed function when required. Any unplanned interruption to a service during its agreed service hours (also called the agreed service time, which is specified in the SLA) is defined as downtime. The availability measure is calculated by taking the downtime from the agreed service time as a percentage of the total agreed time.
Answers
According to ITIL, availability refers to the ability of an IT service or configuration item to perform its intended function when required. This means that the service or item is available and functioning as expected during the agreed service hours or service time specified in the SLA (Service Level Agreement).
However, any unplanned interruption to the service or item during the agreed service hours is considered downtime. Downtime is defined as the period of time during which the service or item is unavailable or not functioning as expected. To calculate the availability measure, ITIL takes the downtime from the agreed service time and calculates it as a percentage of the total agreed time. This percentage represents the level of availability that the service or item is able to achieve during the specified service hours or service time.
Overall, understanding availability and downtime is crucial for maintaining high-quality IT services and ensuring that they meet the expectations of stakeholders and users. By using ITIL's definitions and calculations, organizations can track and measure the availability of their IT services and configuration items, identify areas for improvement, and ultimately provide a better user experience.
You can learn more about Downtime at: brainly.com/question/28334501
#SPJ11
Since you have to be cautious about deleting a slide, PowerPoint only allows you to delete one slide at a time. True or False
Answers
Answer:
true
Explanation:
The statement "Since you have to be cautious about deleting a slide, PowerPoint only allows you to delete one slide at a time" is true.
What is a PowerPoint presentation?G slides can be used to create a PowerPoint presentation. By clicking the large sign at the top left of your screen, you can log in and create a presentation if you have an account. I use slides to create my presentations because it is so simple to use.
You ought to investigate it for yourself. Since it is entertaining, students should enjoy both watching and participating in such presentations. With the right approach, it can assist schools in meeting the needs of all students.
When using PowerPoint, you can project color, images, and video for the visual mode to present information in a variety of ways (a multimodal approach).
Therefore, the statement is true.
To learn more about PowerPoint presentations, refer to the below link:
https://brainly.com/question/16779032
#SPJ2
Which of the following steps does a data scientist take before determining usable results?
Answers
Before determining usable results, a data scientist takes several steps to ensure the accuracy and validity of their findings. First, they define the problem and clearly articulate the hypothesis they are investigating. Next, they gather and clean the relevant data, ensuring that it is accurate and complete. This may involve removing duplicates, correcting errors, and filling in missing values.
Once the data is cleaned, the data scientist will then explore it using statistical analysis and visualization techniques. This allows them to identify patterns, trends, and relationships in the data and determine which variables are most relevant to the research question. They may also use machine learning algorithms to identify patterns that are not immediately apparent.
After analyzing the data, the data scientist will then develop and test models to determine which best predicts the outcome of interest. This involves selecting the appropriate model, tuning its parameters, and evaluating its performance using cross-validation or other techniques.
To know more about data scientist visit:-
https://brainly.com/question/24269857
#SPJ11
1. What are the biggest risks when using the public Internet as a Wide Area Network (WAN) or transport for remote access to your organization’s IT infrastructure?
Answers
Answer:
The problems or risk when using a WiFi is that, hackers often have the ability to position themselves between the user and the end point connection. and once these hackers gains access to your information and privacy, u might lose important documents or contents.
It is of utmost importance that when an end user is using a public WiFi as a WAN, he/she must ensure to browse with VPN turned on, and the sharing options turned off.
Explanation:
Solution
One of the biggest risk with public WiFi is the ability or capacity for hackers to position themselves between you (user) and the point of connection. so instead of communicating directly with the hotpot, at several times you end up sending your information to the hacker.
The hacker also have access or privileges to every information you send out such as credit card information, emails and so on. once the hacker gains access to that information, you run into trouble.
As an end user when making use of public WiFi to ensure to browse with VPN (Virtual private Network) on and turned off sharing options
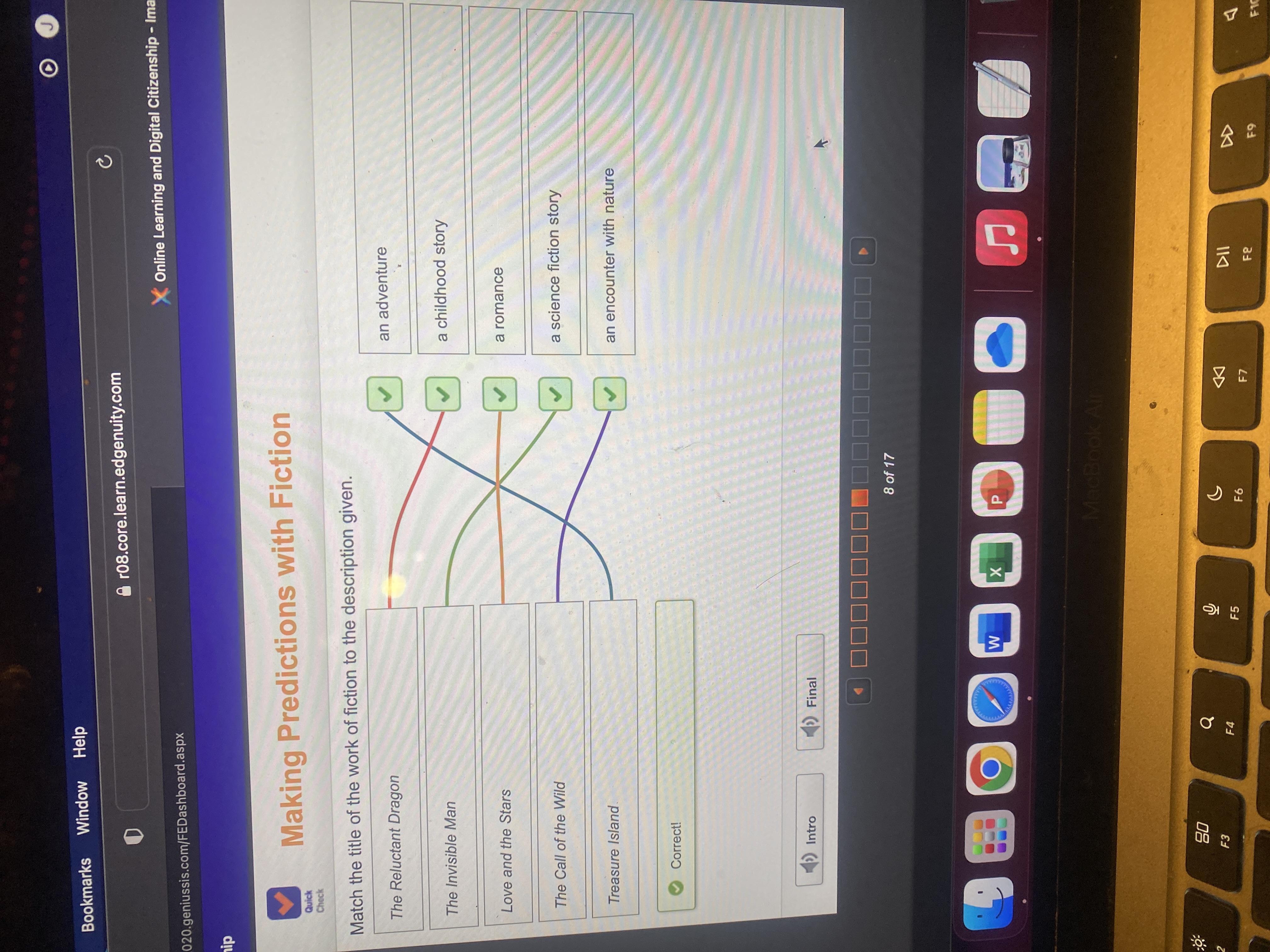
Match the title of the work of fiction to the description given.

Answers
Answer:
Explanation:
Let's get the ones that there is no dispute.
Love and the Stars Romance
The Invisible Man Science Fiction
Treasure Island An Adventure
Call of the Wild An encounter with Nature
Reluctant Dragon Childhood story.
Here's the problem.
Most ten year olds are children. They likely would like both Call of the Wild and the Reluctant Dragon as well as Treasure Island.
The Reluctant Dragon could be called science fiction.
Answer:
your welcomeee
Explanation:
Please.. I want to answer quickly.. in computer or in
clear handwriting.. and thank you very much
2. The data below is actually the length of Item 01 of a Kitchen Organizer for its plate rack. Considering the data given in \( \mathrm{cm} \) and with a standard is \( 55+/-5 \mathrm{~cm} \). Do the
Answers
Without the actual data provided, it is not possible to determine whether the given data is within the standard range or not. The conclusion depends on comparing the actual data with the specified standard range of
55±5 cm.
The given data is within the standard range for the length of Item 01 of the Kitchen Organizer plate rack.
Explanation:
To determine if the given data is within the standard range, we need to compare it to the specified standard of
55
±
5
c
m
55±5cm.
If the given data falls within the range of
55
±
5
c
m
55±5cm, then it is considered within the standard.
To know more about data visit :
https://brainly.com/question/21927058
#SPJ11
So I recently bought a T480 Lenovo ThinkPad and didn't really understand at the time what I was buying. I tried to play some fps games and quickly realized that it runs kind of bad. I did a ton of research on how to upgrade this laptop (it came with a 512gb ssd and 16gb ram upgrade) and what I found was that the fan turns on when the cpu hits 70c which brings me to my question, in theory could I buy a cooling pad and vacuum for it and it increase the fps? Makes sense in my head but before i drop $150 I thought I would drop 45 brainly points. Please give me an explanation on why it would or wouldn't work, and if it wouldn't work what can I do to improve performance.
Answers
In a bid to enhance the performance of the T480 Lenovo ThinkPad, some users have opted to purchase cooling pads and vacuums with the expectation of an improvement in FPS.
What is the explanation for the above response?Note that such efforts may not yield significant outcomes, despite their ability to prevent thermal throttling and promote system stability.
Essentially, FPS performance is largely tied to CPU and GPU clock speeds, which cannot be readily upgraded on most laptops including the T480. An alternative method to augment the game's FPS is by altering its graphics configuration or opting for a less demanding resolution setting.
Through this tactic, less graphic-processing power is needed and better frame rates may result. Also, terminating any unneeded background programs can improve general system capacity usage.
Learn more about computer performance at:
https://brainly.com/question/13161274
#SPJ1