You work part time at a computer repair store. You are building a computer using spare parts. Your task in this lab is to select the correct memory module for the computer. Examine the motherboard memory slots and the memory modules available on the shelf in order to find the correct memory. If necessary, zoom in on the motherboard to get a better look at the memory slots. Install a single memory module in the motherboard. Do not try to install the wrong memory. Only remove the modules from the shelf that are necessary to complete the configuration
Answers
Memory is an important part of a computer. It is essential for a computer to work properly. Memory is the part of the computer that stores data, information, and programs that the computer uses to run. The motherboard of the computer is the central circuit board that connects all the other components of the computer together.
The memory slots are located on the motherboard, and this is where we need to install the memory module. In order to select the correct memory module for the computer, we need to make sure that it is compatible with the motherboard. There are different types of memory modules available on the shelf, and we need to select the one that is compatible with the motherboard.
We need to make sure that the memory module is the right size and the right speed. Once we have selected the correct memory module, we can install it in the motherboard. We need to make sure that we do not try to install the wrong memory module because this can damage the motherboard and the memory module. We also need to make sure that we only remove the modules from the shelf that are necessary to complete the configuration.
For more such questions on computer, click on:
https://brainly.com/question/24540334
#SPJ8
Related Questions
You are a solutions architect who works at a large retail company that is migrating its existing infrastructure to AWS. You recommend that they use a custom VPC. When you create a VPC, you assign it to an IPv4 Classless Inter-Domain Routing (CIDR) block of 10.0.1.0/24 (which has 256 total IP addresses). How many IP addresses are available
Answers
In this case, there are 251 IP addresses available. They are unique addresses for the Internet Protocol.
What is an IP address?An Internet Protocol (IP) address is a unique address on Internet, which is used to indicate a local network.
The term 'Internet Protocol' indicates the principles associated with the format of the data used by the local network.
An Internet Protocol address is always denoted by a set of numerical tags that indicate the local network.
Learn more about IP address here:
https://brainly.com/question/24930846
ITEMS
Evan spent 25% of his money on rent and g on food, together his
expenses totaled to $75.00. Calculate the total amount of money Evan had
Answers
Answer:
Total money he had = $136 (Approx.)
Explanation:
Given:
Spend on rent = 25%
Spend on food = 30%
Total of expenses = $75
Find:
Total money he had
Computation:
Total money he had = [Total of expenses][100/ (Spend on rent + Spend on food)]
Total money he had = [75][100/ (25 + 30)]
Total money he had = [75][100/ (55)]
Total money he had = 136.36
Total money he had = $136 (Approx.)
YOOO CAN ANYONE SOLVE THIS IN JAVA??
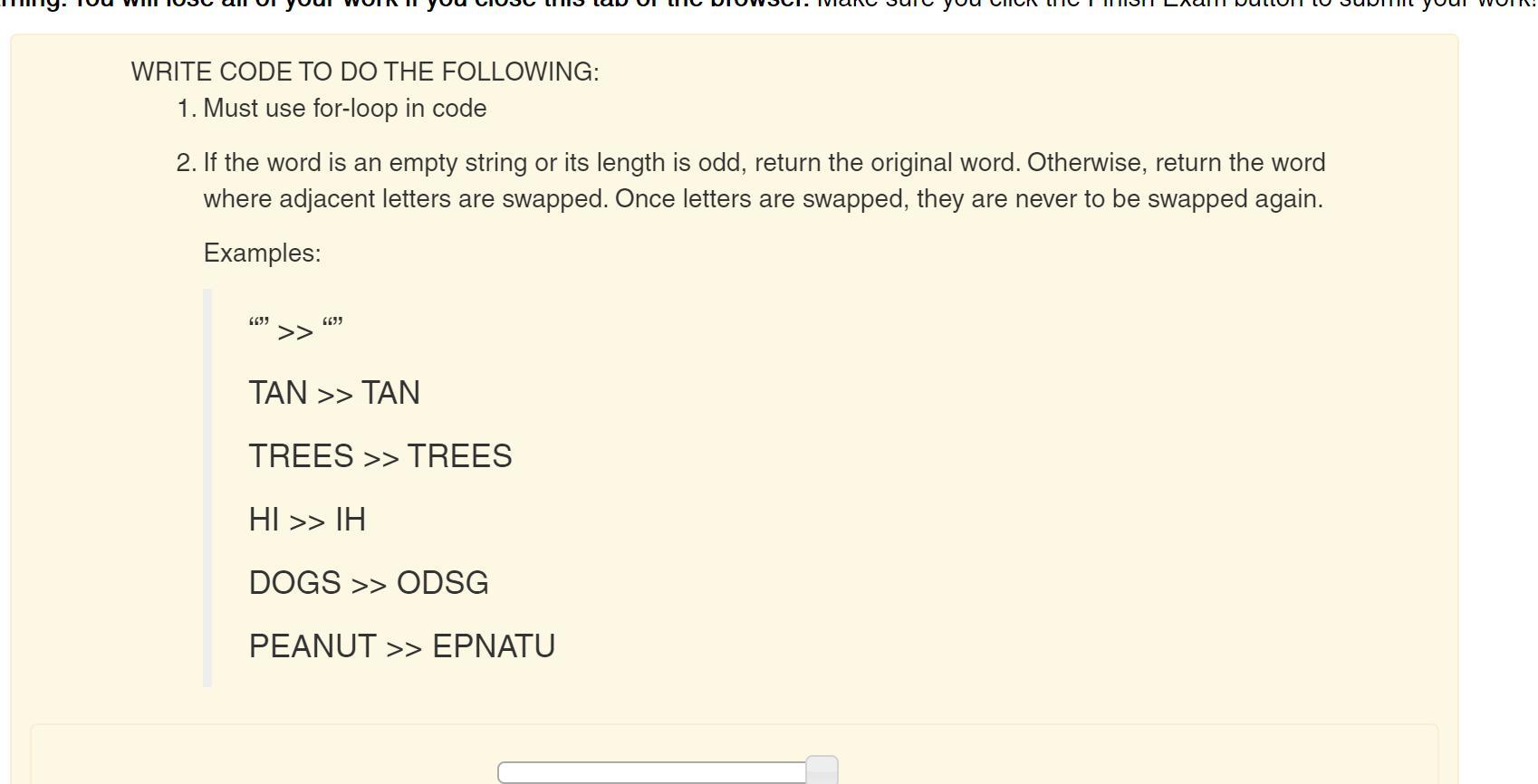
Answers
public class JavaApplication80 {
public static String swapLetters(String word){
char prevC = '_';
String newWord = "";
int count = 0;
if (word.length() % 2 == 1 || word.isBlank()){
return word;
}
else{
for (int i = 0; i<word.length(); i++){
char c = word.charAt(i);
if(count % 2 == 1){
newWord += (c +""+ prevC);
}
prevC = c;
count+=1;
}
}
return newWord;
}
public static void main(String[] args) {
System.out.println(swapLetters("peanut"));
}
}
This works for me. Best of luck.
Answer:
I do not know
Explanation:
he Get_Winnings(m, s) function should take two parameters — a string for the number of gold medals and an integer for the sponsored dollar amount. It will return either an integer for the money won or a string Invalid, if the amount is invalid. Olympians can win more than one medal per day.
Answers
The function "Get_Winnings(m, s)" takes a string for the number of gold medals and an integer for the sponsored dollar amount, returning the money won as an integer or "Invalid" if the amount is invalid.
The function "Get_Winnings(m, s)" takes two parameters: a string "m" representing the number of gold medals and an integer "s" representing the sponsored dollar amount. Here's a step-by-step explanation of the function.
Check if the input values are valid. If the "m" parameter is not a string or the "s" parameter is not an integer, return the string "Invalid".Convert the string "m" to an integer to calculate the total winnings based on the number of gold medals won.Calculate the money won by multiplying the number of gold medals with the sponsored dollar amount.Return the calculated winnings as an integer.If the input values are not valid or cannot be converted, the function will return the string "Invalid" to indicate an invalid amount. Otherwise, it will return the calculated money won as an integer.
For more such question on Integer
https://brainly.com/question/30030325
#SPJ8
explain how do compare and contrast graphic organizers help you to synthesize information?
Answers
Answer:
Answer: Given two or more sets of features of items, people, events, etc; compare and contrast graphic organizers help you to see what the sets have in common and what difference one set from the others, that is, what characteristics are unique from each set.
Explanation:
Given two or more sets of features of items, people, events, etc; compare and contrast graphic organizers help you to see what the sets have in common and what difference one set from the others, that is, what characteristics are unique from each set
Computer Architecture Question.
Note: Please do not copy from another question
answer.
a. Write down the steps of CISC approach for multiplying two numbers in memory of location 2:3 and 5:2. (marks 4)
Answers
Steps involved:1. Load first number from memory location 2:3 into a register. 2. Load second number from memory location 5:2 into another register. 3. Multiply two numbers stored in registers. 4. Store result.
The CISC (Complex Instruction Set Computer) approach for multiplying two numbers typically involves multiple steps to perform the multiplication operation. Here are the steps involved in the CISC approach for multiplying two numbers in memory:
1. Load the first number from memory location 2:3 into a register.
2. Load the second number from memory location 5:2 into another register.
3. Multiply the two numbers stored in the registers.
4. Store the result of the multiplication back into memory location 2:3.
In the first step, the CISC approach involves loading the first number from memory into a register. This allows for faster access and manipulation of the data. Similarly, in the second step, the second number is loaded from memory into another register. Once both numbers are loaded into registers, the actual multiplication operation takes place in the third step. The CPU performs the multiplication operation on the two numbers stored in the registers using the designated multiply instruction. This step utilizes the hardware's multiplication capabilities to perform the computation.
Finally, in the fourth step, the result of the multiplication is stored back into memory. The product is stored in memory location 2:3, replacing the original value. The CISC approach for multiplication involves breaking down the operation into multiple steps to allow for more complex instructions and operations to be performed. This approach allows for more flexibility and functionality in executing complex operations, but it may also result in longer instruction execution times compared to simpler architectures like RISC (Reduced Instruction Set Computer). CISC architectures often include a wide range of instructions to support various operations, including complex arithmetic and memory manipulation.
To learn more about RISC (Reduced Instruction Set Computer) click here:
brainly.com/question/29453640
#SPJ11
For questions 1-4, consider the following code:
num = int(input("Enter a number: "))
num = num % 4
if (num == 1):
print ("A")
elif (num == 2):
print ("B")
elif (num == 3):
print ("C")
elif (num == 4):
print ("D")
else:
print ("E")
If the user enters 5 what is output?
Answers
Answer:
A
Explanation:
if enters 5, then num takes a 5 value
num % 4 is the remainder of 5 divided by 4 that is 1
Finally num is equals to 1. For this reason the outpuut is A
Which of the following items can you locate in a document using the navigation pane? Choose the answer.
A) search results
B) pages
C) headings
D) all of the above
Answers
Answer:
D: All of the above
Explanation:

The success criteria are used to judge whether a project is successful. False True
need it now
Answers
Answer:
True True True True
Answer:
true
Explanation:
How are the waterfall and agile methods of software development similar?
Both methods allow project teams to complete small portions of the entire project in small sprints and work on different steps simultaneously.
Both methods focus on development rather than planning, in order for project teams to work more quickly.
Both methods have project teams work on one step at a time and move on when the previous step is completed and approved.
Both methods require documentation so project teams stay on track and keep control over what version of the project they are working on.
Answers
Answer:
In the question "first and last", that is "option 1 and 4" is correct.
Explanation:
In the given question the numbering of the choices is missing. if we numbering the choices, then the first choice is on the 1 number, the second choice is in 2 and so on, in which the correct and the wrong choice can be defined as follows:
In point 1, Both method, it divides the project into small parts, at it the working is easy, that's why it is correct. In point 4, Both method, it requires the documentation, that's why it tracks the project. In point 2 and 3, both were wrong because it focuses on both development and planning, and in Waterfall when one part is complete then it will go on the next part, but in the Agile, it does not use this technique.Jump to level 1 Convert totalPennies to dimes, nickels, and pennies, finding the maximum number of dimes, thein nickols, then perinief. Ex: if the input is 87 , the output is: Dimes: 8 Nickels: 1 Pennies: 2 Notedime is 10 pennies: A nickel is 5 pennies: 1 ainclude kiostrean? 2 using namespace std; a) int axin() I 5 int totaionnies; 6 int numbions: ? int numickels; 6 int numennies; 10 cin≫totalpennies; 11 W* your code goes here%14 Cout \& "Dimss? \&6 numbintes ke endip 15 cout ke Wikeis:
Answers
The given code is an incomplete code block in C++ that prompts the user for an input value (totalPennies) and requires the user to write code to convert that value into dimes, nickels, and pennies.
To complete the code block and achieve the desired output, the user needs to implement the following steps:Calculate the maximum number of dimes that can be obtained by dividing the totalPennies by 10. Assign the result to the variable numDimes.Subtract the value of the dimes from the totalPennies to get the remaining pennies. Assign the result to the variable remainingPennies.Calculate the maximum number of nickels that can be obtained by dividing the remainingPennies by 5. Assign the result to the variable numNickels.Subtract the value of the nickels from the remainingPennies to get the remaining pennies. Assign the result to the variable numPennies.Finally, output the values of numDimes, numNickels, and numPennies using cout statements. The completed code block might look like this: #include <iostream> using namespace std; int main() { int totalPennies; int numDimes, numNickels, numPennies; cout << "Enter the total number of pennies: "; cin >> totalPennies; numDimes = totalPennies / 10; int remainingPennies = totalPennies - numDimes * 10; numNickels = remainingPennies / 5; numPennies = remainingPennies - numNickels * 5; cout << "Dimes: " << numDimes << endl; cout << "Nickels: " << numNickels << endl; cout << "Pennies: " << numPennies << endl; return 0; } This code will take an input value of totalPennies from the user and output the maximum number of dimes, nickels, and pennies that can be obtained from that value.
To learn more about pennies click the link below:
brainly.com/question/30600857
#SPJ4
Problem 6(45 pts) 6.1) What addressing mode does the instruction MOV DX. [BPI DI + AB28 Huse? 6.2) Before the execution of the instruction MOV DX. [BP) D-AB28H the contents of tegisters CS and IPare A
Answers
The MOV DX, [BPI DI + AB28 H] instruction employs the based indexed addressing mode, combining the base register (BP) and index register (DI) with an offset (AB28H) to access memory and facilitate flexible memory operations.
The addressing mode used in the instruction MOV DX, [BPI DI + AB28 H] is the based indexed addressing mode.
Explanation:
The based indexed addressing mode combines a base register (BX or BP) with an index register (SI or DI) and an offset to access memory. In this case, the base register is BP, and the index register is DI. The offset is AB28H.
To know more about Addressing mode visit :
https://brainly.com/question/13567769
#SPJ11
what is the primary way to access applications in windows8?
Answers
Answer:
Click the app icon on the taskbar. Double-click the app shortcut on the Desktop. Click the app tile in the Start screen.
Explanation:
Answer:
Press the Windows key. Much like Windows 10.x
Explanation:
If you press the Windows key, you will see a list of the apps. You can also search for them there.
how many different bit strings of length 12 contain at most ten0's
Answers
There are 4683 different bit strings of length 12 that contain at most ten 0's.
To determine the number of different bit strings of length 12 that contain at most ten 0's, we need to consider all possible combinations.
First, let's calculate the number of bit strings with exactly ten 0's. There are 12 positions in the string, and we need to choose exactly ten of them to be filled with 0's. The remaining two positions will be filled with 1's. This can be calculated using the binomial coefficient:
C(12, 10) = 12! / (10! * (12 - 10)!) = 12! / (10! * 2!) = 66
Next, let's calculate the number of bit strings with fewer than ten 0's. We can have zero, one, two, three, four, five, six, seven, eight, or nine 0's. We calculate the number of bit strings for each case and sum them up:
Number of bit strings with zero 0's:
C(12, 0) = 12! / (0! * (12 - 0)!) = 1
Number of bit strings with one 0:
C(12, 1) = 12! / (1! * (12 - 1)!) = 12
Number of bit strings with two 0's:
C(12, 2) = 12! / (2! * (12 - 2)!) = 66
Number of bit strings with three 0's:
C(12, 3) = 12! / (3! * (12 - 3)!) = 220
Number of bit strings with four 0's:
C(12, 4) = 12! / (4! * (12 - 4)!) = 495
Number of bit strings with five 0's:
C(12, 5) = 12! / (5! * (12 - 5)!) = 792
Number of bit strings with six 0's:
C(12, 6) = 12! / (6! * (12 - 6)!) = 924
Number of bit strings with seven 0's:
C(12, 7) = 12! / (7! * (12 - 7)!) = 792
Number of bit strings with eight 0's:
C(12, 8) = 12! / (8! * (12 - 8)!) = 495
Number of bit strings with nine 0's:
C(12, 9) = 12! / (9! * (12 - 9)!) = 220
Summing up all the cases, we get:
66 + 1 + 12 + 66 + 220 + 495 + 792 + 924 + 792 + 495 + 220 = 4683
Therefore, there are 4683 different bit strings of length 12 that contain at most ten 0's.
Learn more about bit strings visit:
https://brainly.com/question/31168016
#SPJ11
You can produce evenly spaced floating-point ranges with NumPy’s linspace function. Generate a linear array between 5 and 15 with 10 elements. What is the remainder when you divide the second element by 2? Approximately. a. 0.00 b. 0.11 c. 0.22 d. 0.33 e. 0.44
Answers
You can produce evenly spaced floating-point ranges with NumPy’s linspace function. Generate a linear array between 5 and 15 with 10 elements. The remainder is approximately 0.11. So option b is correct.
To generate a linear array between 5 and 15 with 10 elements using NumPy's linspace function, you can use the following code:
import numpy as np
array = np.linspace(5, 15, 10)
The array generated by this code will be [ 5. 6.11111111 7.22222222 8.33333333 9.44444444 10.55555556 11.66666667 12.77777778 13.88888889 15. ].
To find the remainder when you divide the second element by 2, you can use the modulo operator % in Python:
remainder = array[1] % 2
Calculating the above expression, you will find that the remainder is approximately 0.11.
Therefore,option b is correct.
To learn more about linear array visit: https://brainly.com/question/24275089
#SPJ11
what is the minimum delay we will need to update the pc value to pc 4, and to read the instruction from memory?
Answers
The minimum delay that is needed to update the pc value to pc+4 can be calculated as follows:
Minimum delay: D-mem + Sign Extend
= 250 ps + 15 ps
= 265 ps
What is a PC?A multipurpose microcomputer called a personal computer (PC) is small, affordable, and capable enough for individual use. As opposed to being used by a computer specialist or technician, personal computers are designed to be operated by the end user. Contrary to big, expensive mainframes and minicomputers, personal computers do not support simultaneous time-sharing by multiple users. The term "home computer" was also used, mostly in the 1980s and late 1970s.
In the 1960s, owners of institutional or corporate computers had to create their own programs in order to use the equipment for any practical purpose. The majority of personal computers run commercial software, freeware (often proprietary), free and open-source software, or both. However, users of personal computers are also permitted to create their own applications.
Learn more about personal computers
https://brainly.com/question/26165623
#SPJ4
How do you fix your transaction Cannot be completed because you have another pending transaction on your account on Steam?
Answers
To fix the "Cannot be completed because you have another pending transaction on your account" error on Steam, you need to wait until the previous transaction is completed or cancelled before making a new one. You can check the status of your previous transaction by going to your Steam account's transaction history
The error "Cannot be completed because you have another pending transaction on your account" on Steam typically occurs when there is an existing transaction that has not yet been fully processed. To resolve this issue, you should follow these steps:
Wait a few minutes: If your transaction is still processing, you may need to wait a few minutes for it to complete. Check your transaction history: Log into your Steam account and go to your transaction history to check if the pending transaction has been completed. Clear your cache and cookies: Clearing your cache and cookies can sometimes resolve any technical issues that might be preventing the transaction from completing. Contact Steam Support: If the above steps don't work, you should contact Steam Support for further assistance. They will be able to help you troubleshoot the issue and ensure that your transaction is completed successfully. In conclusion, resolving the "Cannot be completed because you have another pending transaction on your account" error on Steam is usually straightforward and can be done in a few simple steps. If you're still having trouble, don't hesitate to reach out to Steam Support for help.
To know more about Steam Please click on the given link
https://brainly.com/question/15447025
#SPJ4
A search expression entered in one search engine will yield the same results when entered in a different search engine.
A. True
B. False
Answers
Answer:
false
Explanation:
What GUI element is usually on the right side of the taskbar and displays open services?
Select one:
a. identification area
b. status tray
c. display area
d. system tray
Answers
d). The system tray is a GUI element usually located on the right side of the taskbar and displays open services.
The system tray, also known as the notification area, is a section of the taskbar in Windows operating systems that displays icons for system and program features that are running in the background. It is used to provide the user with notifications about various events and to provide quick access to certain system settings.
It is located on the right side of the taskbar and displays open services, such as the clock, volume control, network connections, and other system settings. It also displays icons for programs that are running in the background, such as antivirus software and instant messaging applications.
For more questions like System tray click the link below:
https://brainly.com/question/28147966
#SPJ4
What is the highest numeral in a binary code?
Answers
Answer:
The highest numeral in binary code is 1
In binary, you can only have 1s and 0s
if you're asking for the biggest number that can be represented, it's 255, which is 11111111. (this is 8 1s)
Explanation:
Is this a trick question? lol
May I have brainliest please? :)
suppose you have a file that is linked to a file owned by another user. how can you ensure that changes to the file are no longer shared?
Answers
To ensure that changes to a file linked to another user's file are no longer shared, you can create a new, independent copy of the file.
The steps to create a new, independent copy of the file :
First, you can make a copy of the file and work on the copy instead of the original.Second, you can unlink the file from the original file owner's account. This can usually be done by accessing the file's settings and removing the shared access permissions for the other user. This will prevent them from being able to access or edit the file in the future.
Finally, you can also communicate with the other user to let them know that you are no longer sharing the file with them. This can be especially important if the other user is expecting to have access to the file for collaborative purposes.
know more about files settings here:
https://brainly.com/question/29511206
#SPJ11
Mr. Prasad is a high school English teacher. He weighs different essays and assignments differently while calculating final grades. Therefore, he has made an Excel worksheet showing how different classwork weighs into a final grade. He would like to distribute an electronic file to his students, but he wants everyone to be able to read it regardless of whether or not they have Microsoft Office Suite.
What can Mr. Prasad do to best distribute the file?
use “Save As” to save it as an Adobe PDF file
use “Save As” to save it as an Excel 97-2003 workbook
paste the material into an Adobe PDF file
paste material into an Excel 97-2003 workbook
Answers
Mr. Prasad should use “Save As” to save it as an Adobe PDF file. The correct option is A.
What is pdf?The abbreviation PDF stands for Portable Document Format. It's a versatile file format developed by Adobe that allows people to easily present and exchange documents.
It is basically regardless of the software, hardware, or operating systems used by anyone who views the document.
As Mr. Prasad wants to distribute the files regardless of the students having Microsoft Office or not, he can save it as pdf, so it can be readable with all.
Thus, the correct option is A.
For more details regarding pdf, visit:
https://brainly.com/question/13300718
#SPJ1
1. what is the internet infrastructure stack? what is the relevance of this technological concept to marketers? what is the significance of cloud computing in relationship to the internet infrastructure? who is the leader in cloud computing for third parties by revenue, cisco, ibm, , or amazon?
Answers
The correct answer is Internet infrastructure stack are sets of hardware and services combined together which helps in making the data and information available on the web page.
Any hardware component that is housed inside a computer. a set of guidelines or software that instructs a computer on what to do or how to carry out a certain task (computer software runs on hardware). a computer application that gives users the resources they need to do a certain task. any hardware component that is housed inside a computer. a set of guidelines or software that instructs a computer on what to do or how to carry out a certain task (computer software runs on hardware). a computer application that gives users the resources they need to do a certain task.
To learn more about hardware click on the link below:
brainly.com/question/15232088
#SPJ4
a saas provider such as oracle or sap manages service levels and availability. this is advantageous because _____.
Answers
Lower distribution costs, limiting development to a single platform, tighter comments loop with clients, on the restore bugs, reduced threat of software program piracy.
so that it can be studied changed and multiplied by means of its users?Open Source Software
Open supply software program refers to laptop code that is dispensed under a license in which the copyright holder provides users the rights to freely access, modify, and distribute the software for any purpose.
What is software as a service SaaS quizlet?SaaS (Software as a Service) Applications that are deployed over a network, normally the web, on hand via browser or program interface; every now and then referred to as software demand.
Learn more about service levels and availability. here;
https://brainly.com/question/30325950
#SPJ4
What is the term for the psychology, reasoning, and history behind a character's reactions in certain situations?
Answers
Most teenagers operate off of social-cultural psychology, primarily because of propaganda on TV, family traditions, etc.
Psychological factors like cognition could serve as a trait for situations.
Biological traits like testosterone, bipolar disorder, etc. It can affect these situations.
How much mail can be
stored in each mail box?
Answers
Answer:
Most mailboxes are 1 - 4 GB with one or two larger.
Explanation:
the em – command is used to repeat the last action and to redo copy none of these
Answers
redo the right answer..
write a QBASIC program to calculate the perimeter of calculate the perimeter of circle [hint p=2pi r]
Answers
Here's an example program in QBASIC that calculates the perimeter of a circle using the formula P = 2πr:
REM QBASIC program to calculate the perimeter of a circle
INPUT "Enter the radius of the circle: ", r
p = 2 * 3.14159 * r
PRINT "The perimeter of the circle is "; p
END
This program prompts the user to enter the radius of the circle, then calculates the perimeter using the formula P = 2πr. The result is displayed using the PRINT statement.
Note that the value of π is approximated as 3.14159 in this example. You could increase the precision by using a more accurate value of π or by using QBASIC's built-in constant for π, which is named PI.
Answer:
A QBASIC program to calculate the perimeter of a circle
DECLARE SUB CIRCUM (R)
CLS
INPUT “ENTER RADIUS"; R
CALL CIRCUM (R)
END
SUB CIRCUM (R)
C=2*3.14 * R
PRINT "CIRCUMFERENCE OF CIRCLE "; C
END SUB
Internal combustion engines use hot expanding gasses to produce the engine's power. Technician A says that some engines use spark to ignite the gasses. Technician B says some engines use compression to ignite the gasses. Who is correct?
Answers
Answer:
Explanation:
Both are right.
Engines are divided into:
1) Internal combustion engines
2) Diesels
Hot Dog Cookout Calculator Assume hot dogs come in packages of 10, and hot dog buns come in packages of 8. Write a program that calculates the number of packages of hot dogs and the number of packages of hot dog buns needed for a cookout, with the minimum amount of leftovers. The program should ask the user for the number of people attending the cookout and the number of hot dogs each person will be given. The program should display the following details: 1. The minimum number of packages of hot dogs required 216.2. The minimum number of packages of hot dog buns required.3. The number of hot dogs that will be left over.4. The number of hot dog buns that will be left over.
Answers
Answer:
Following are the code to this question:
person= int(input("Input the value who attend the cookout: "))#defining a variable person for input value
Given_hotdog = int(input("Input the value of hotdog, that each person will take: "))#defining a variable Given_hotdog for input value
hotdogs = person* Given_hotdog #calculating the total value of hotdogs
# calculating the numbers of the package, that holds require hotdog and buns
package_hotdog=int(hotdogs/10)+1# calculating hotdog packages
bun_package=int(hotdogs/8)+1# calculating buns package
left_hotdogs= package_hotdog*10 -hotdogs# calculating left hotdogs
left_buns=bun_package*8-hotdogs# calculating left buns
print("Total Hotdogs",hotdogs)#print total hotdogs value
print("The Minimum number of packages require for hotdogs: ", package_hotdog)#print require hotdogs value
print("The Minimum number of packages require for buns: ", bun_package)#print require buns value
print("Number of left hotdogs: ", left_hotdogs)#print left hotdogs value
print("Number of left buns: ", left_buns)#print left buns value
Output:
please find the attached file.
Explanation:
In the above-given code, the "person and Given_hotdog" variable is declared, which is used to take input from the user end and in the "hotdogs" variable we calculate its total value.
In the next step, "package_hotdog and bun_package" is declared, which uses the "hotdogs" variable to calculate its value. At the last step, the "left_hotdogs and left_buns" variable is declared, which uses the above variable for calculating the value and use the print method to print its value.