A trackerball is a pointing device
Answers
Answer:
nice
Explanation:
Related Questions
Write a informational paragraph that compares and contrast climate and weather include specific details for each
Answers
Answer:
The main difference between weather and climate refers to their temporal extension, that is, while weather refers to the climatic and meteorological conditions in the short term (rain forecasts, temperatures, atmospheric pressure, etc., which are going to happen in the next few days), the climate is a compilation of all these conditions and their averaging, to account for long-term weather conditions (thus, for example, if in December there is an average temperature of 0ºC, or the amount of snow that usually accumulates in that month, etc., that is, it is a much more macro look of what the climate is in a certain territory).
what is a sensitive compartmented information program
Answers
Answer:
cpu
Explanation:
what is computer? Write is features
Answers
Explanation:
A computer is an machine that accepts data as input,processes that data using programs, and outputs the processes the data as information.
the features are
1) speed
2) accuracy
3) versatility
4) multi tasking
5) reliability
2.3 pseudocode exercise on edhesive
Answers
Answer:
a=int(input("Enter a numerator: "))
b=int(input("Enter a divisor: "))
quotient=a/b
remainder=a%b
print("Quotient is: " + str(int(quotient)))
print("Remainder is: " + str(int(remainder)))
That's 2.3 question 1
a_ft = int(input("Enter the Feet: "))
a_inc = int(input("Enter the Inches: "))
b_ft = int(input("Enter the Feet: "))
b_inc = int(input("Enter the Inches: "))
sum_inc = a_inc + b_inc
# select the whole and the fractional part
inc_to_ft = sum_inc // 12
rem_from_div = sum_inc % 12
sum_ft = a_ft + b_ft + inc_to_ft
print("Feet: {} Inches: {}".format(sum_ft, rem_from_div))
That's 2.3 question 2
Explanation:
I wasn't sure which one you needed so I added both.
In which generation microprocessor was developed short answer of computer science
Answers
Explanation:
in fourth generation microprocessor was developed.
may it helped u
Merle wants to change the formatting of all bold cells to be non-bolded. Shania wants to copy the cell color,
border, and font from cell E12 to all of column D. Which best describes what each person should do?
A. Merle should use Find and Replace, and Shania should use the Format Painter.
B.Merle should use the Rules Manager, and Shania should use Find and Replace.
C.Merle should use the Format Painter, and Shania should use the Rules Manager.
D. Merle should use the Format Painter, and Shania should use Find and Replace.
Answers
Answer:
Merle should use Find and Replace, and Shania should use the Format Painter.
Explanation:
It's the most logical to me.. And that's what I'm gonna do on my test. =) hope it helps.
What type of data uses numbers that can be used in the arithmetic operations?
Answers
Answer:
Numerical data uses numbers that can be used in arithmetic operations.
True or false: Network attached storage (NAS) is a type of file server designed for homes and small businesses and is less expensive, easier to set up, and easier to manage then most file servers.
Answers
True. Network Attached Storage (NAS) is a type of file server designed for homes and small businesses, and it is typically less expensive, easier to set up, and easier to manage than most traditional file servers. NAS devices are dedicated file storage devices that connect to a network, providing shared storage to multiple users or devices over the network. NAS devices are built around a specialized operating system that is optimized for file sharing and storage management, and they often come pre-configured with all the necessary software and hardware to provide shared storage right out of the box.
NAS devices are typically designed to be plug-and-play, with no need for specialized IT knowledge or complex configuration. This makes them an attractive option for small businesses or home users who need shared storage but lack the resources or expertise to deploy and manage a more complex file server. Additionally, NAS devices are often designed with user-friendly interfaces, making it easy for non-technical users to manage and configure the device.
Overall, NAS devices offer a cost-effective and user-friendly solution for shared storage needs in small businesses and home environments. They provide a convenient way to centralize and manage data, while minimizing the costs and complexities associated with traditional file servers.
Learn more about Network Attached Storage here:
https://brainly.com/question/31180230
#SPJ11
Which of the following best describes the ability of parallel computing solutions to improve efficiency?
answer choices
Any problem that can be solved sequentially can be solved using a parallel solution in approximately half the time.
Any solution can be broken down into smaller and smaller parallel portions, making the improvement in efficiency theoretically limitless as long as there are enough processors available.
The efficiency of parallel computing solutions is rarely improved over the efficiency of sequential computing solutions.
The efficiency of a solution that can be broken down into parallel portions is still limited by a sequential portion.
Answers
The best description of the ability of parallel computing solutions to improve efficiency is the efficiency of a solution that can be broken down into parallel portions is still limited by a sequential portion.
What is parallel computing?A type of computation known as parallel computing involves running numerous calculations or processes concurrently. Large problems can frequently be broken down into smaller problems, which can all be handled at once.
Bit-level, training, data, and job parallelism are some of the several types of parallel computing.
The physical limitations that impede frequency scaling have increased interest in parallelism, which has long been used in high-performance computing.
To know more about parallel computing:
https://brainly.com/question/20769806
#SPJ4
True or false
A compiler translates a source program one line of code at a time.
Answers
Answer:
True
Explanation:
yes It translates one line at a time to be able to confirm all information.
Answer:
True
Explanation:
I hope this helps you
the key press combination that will request a running process terminate:
Answers
The key press combination that will request a running process terminate is Ctrl+Alt+Delete (or Ctrl+Shift+Esc).
This key combination will bring up the Windows Task Manager from which you can choose the program that you want to terminate.
What is Ctrl+Alt+Delete?
Ctrl+Alt+Delete is a keyboard shortcut on IBM PC-compatible computers that interrupts a running process and brings up a Windows security screen. The operating system (OS) uses this feature to allow users to reboot, log out, or shut down their computers in a safe manner.
What does the Windows Task Manager do?
The Windows Task Manager is a built-in tool for managing processes and programs running on Windows computers. It provides information about the resource usage of the computer, such as CPU usage, memory usage, and disk usage. It also allows users to end processes that are not responding or that are causing problems with the computer.
Learn more about Windows Task Manager:
https://brainly.com/question/32153709
#SPJ11
choose if you want to keep signing in with your face or fingerprint
Answers
Answer: Fingerprint
Explanation: Facial recognition is more convenient however there are some instances that fingerprint is more reliable. Facial recognition cannot detect a face with makeup on or you're wearing glasses unless you had that during the registration. And, your face cannot be recognized in dim areas as well.
what would you do if you got exposed on social media and (depression) who feels like that sometimes ?
Answers
Answer:
Sadness
Explanation:
Because i sad or mad
Answer:
nothing
Explanation:
i wouldn't get the app
1)Which tool can you use to find duplicates in Excel?
Select an answer:
a. Flash Fill
b. VLOOKUP
c. Conditional Formatting
d. Concatenation
2)What does Power Query use to change to what it determines is the appropriate data type?
Select an answer:
a.the headers
b. the first real row of data
c. data in the formula bar
3)Combining the definitions of three words describes a data analyst. What are the three words?
Select an answer:
a. analysis, analyze, and technology
b. data, programs, and analysis
c. analyze, data, and programs
d. data, analysis, and analyze
Answers
The tool that you can use to find duplicates in Excel is c. Conditional Formatting
b. the first real row of datac. analyze, data, and programsWhat is Conditional Formatting?Excel makes use of Conditional Formatting as a means to identify duplicate records. Users can utilize this feature to identify cells or ranges that satisfy specific criteria, like possessing repetitive values, by highlighting them.
Using conditional formatting rules makes it effortless to spot repeated values and set them apart visually from the other information. This function enables users to swiftly identify and handle identical records within their Excel worksheets, useful for activities like data examination and sanitation.
Read more about Conditional Formatting here:
https://brainly.com/question/30652094
#SPJ4
in this homework you are supposed to use the random number generater random.random sample from the numpy package to generate random numbers with three different distributions. recall from the lecture that if ????:ℝ→[0,1] is a distribution function with generalized inverse ????−1:[0,1]→ℝ and ???? is a uniform random variable, then ????−1(????) is a random variable with distribution function ???? . using the function random.random sample from numpy package write three functions: exponentialrv(seed, mean,n) that returns for given seed a bunch of n random variables from an exponential distribution with the provided mean. derive the generalized inverse distribution function analytically for your simulation. binomial(seed, p,m,n) that returns for given seed a bunch of n binomial distributed random numbers with the provided success probability p and the number of trial equal to m. you have to numerically calculate the inverse distribution function. funnydicerv(seed,n) that returns for given seed a bunch of n random number which describe a biased die with distribution ℙ({1})
Answers
eeeeeeeeeeee
eeeeeeeeeee
Full Answer to this question.

Answers
Answer:
see picture
Explanation:
I'm not exactly sure if you're supposed to write a trace snapshot at the beginning or at the end of a loop iteration. I did it at the end.

Phishing is ____________. When hackers overwhelm a website with too many requests. A network of private computers infected with malicious software and controlled as a group without the owners' knowledge. A piece of code that is capable of copying itself and typically has a detrimental effect, such as corrupting the system or destroying data. Emails designed to trick users into sharing private information.
Answers
Answer:
Emails designed to trick users into sharing private information.
Explanation:
if that is a multiple choice question and the other sentences is the answer choices.
As a result of the Internet, people today
use more mobile devices.
go to the movies more often.
no longer read newspapers.
no longer need computers.How long has the environment been a major issue in the United States?
Answers
Answer:
hi there, the answer is
a. use more mobile devices
hope this helps :)
have a good day!
Explanation:
i just took the quiz rnnn
Answer:A
Explanation:
edge 2023
(e) A more advanced version of this cipher uses a key word to re-order the columns prior to reading off the encrypted text. Write the key word at the top: B I T
S
A A
H
P
D M
E
Y
Re-order the columns by sorting the letters in the key word alphabetically: A A
H
P
B
I T
S
D
M
E
Y
Read off the letters, ignoring the key word row: "AHPITSMEY" Encode the first 12 letters of your name with key word CLEVER (and therefore, C=6 ). Show your grid before and after re-ordering. Also write the string before and after it is encoded. (f) Write a working, text based program that can encode using the key word version of the transposition cipher you have just been using. The program should allow for varying sizes of key word. Your answer to this question should consist of the code of your program and the text output of your program when it is encoding the phrase 'the packet is in the letterbox' using key words that are the first three, four and five letters of your name. Do not paste a screenshot, copy paste the code and text output of the program. Use any programming language you like.
Answers
Here's how to use the key word to re-order the columns prior to reading off the encrypted text:Given key word: CLEVER C = 6, L = 12, E = 5, V = 22, R = 18 Re-order the columns by sorting the letters in the key word alphabetically:E L R V C. The re-ordered grid looks like this:
E L R V C T E H K C A P T I S N T H E L E T E R B O X. The string before encoding is "THE PACKET IS IN THE LETTERBOX". Since the length of the original message is 27 and we are encoding it with a key word of length 6, the extra cells at the bottom right are filled with "Z". The resulting table after encoding is: E L R V C T E H K C A P T I S N Z Z Z Z Z Z Z. The encoded string before removing spaces and converting to uppercase is "TCEEITHKNACPTISNZ".
After removing the spaces and converting to uppercase, we get the final encoded string "TCEEITHKNACPTISNZ".(f) Here's a Python implementation of the key word version of the transposition cipher:```def encode_with_keyword(message, keyword): # Remove spaces and convert to uppercase message = message.replace(" ", "").upper()
To know more about encrypted visit:
brainly.com/question/30265562
#SPJ11
Why are graphs and charts important to analyze data?
Answers
Answer:
Graphs and chart provide the GUI representation they provide the analysis in form of summary that is easy to understand and they provide good comparision.
Explanation:
Summary
Comparision
Quick to understand
Months Write a program that will ask the user for a month as input in numeric format and print out the name of the month. Here is a sample run: Enter the Month: 9 It is september!
Answers
The program prompts the user to enter a month in numeric format and then prints the corresponding name of the month. For example, if the user enters 9, the program will output "It is September!" as the result.
To implement this program in Python, we can define a dictionary that maps numeric month values to their corresponding names. The program will ask the user to input a numeric month value. It will then retrieve the corresponding month name from the dictionary and print it along with a message. Here's an example implementation:
def print_month_name():
month_dict = {
1: "January",
2: "February",
3: "March",
4: "April",
5: "May",
6: "June",
7: "July",
8: "August",
9: "September",
10: "October",
11: "November",
12: "December"
}
month_number = int(input("Enter the Month: "))
if month_number in month_dict:
month_name = month_dict[month_number]
print("It is", month_name + "!")
else:
print("Invalid month number.")
print_month_name()
In this program, the dictionary month_dict maps numeric month values (keys) to their corresponding month names (values). The program prompts the user to enter a month number. If the entered number exists as a key in the dictionary, the corresponding month name is retrieved and printed along with the message "It is [month name]!". If the entered number is not found in the dictionary, an error message is displayed.
Learn more about Python here: https://brainly.com/question/30427047
#SPJ11
Ignore this it a temporary note for me: SPSstudents
Answers
Answer:
okk
Explanation:
A programmer is developing an action-adventure game that will be geared
toward dedicated and experienced gamers ages 13 and up. Which part of the
game design document should include this information?

Answers
Answer:
D. demographics
Explanation:
demographics refers to the age or group of people that this game will be targeted towards
The given data should be included in the game design document's section on demographics. Option D is correct.
What are the demographics?Statistics that characterize populations and their traits are known as demographics. The study of a population based on characteristics like age, race, and sex is known as demographic analysis.
The gathering and analysis of broad characteristics about populations and groups of individuals is known as demographic analysis. For businesses to understand how to sell to consumers and make strategic plans for upcoming patterns in consumer demand, demographic data is highly helpful.
Therefore, option D is correct.
Learn more about the demographics, refer to:
https://brainly.com/question/13146758
#SPJ2
In design-by-contract, the code responsible for making sure the precondition (requires clause) is true when a method is called is:
Answers
In Design-by-Contract, the code responsible for ensuring the precondition (requires clause) is true when a method is called is the client’s responsibility. This is because the client that calls the method should fulfill the requirements that the method expects in its input
. The precondition is a condition that should be true before the method is called. As a result, the client is responsible for ensuring that the required conditions are true when calling a method.The precondition clause specifies the restrictions on the arguments that can be passed to the method. It also specifies the constraints that should hold before the method is called, such as a specified range of values.
Furthermore, it aids in the detection of errors by placing limits on the arguments that can be passed to a method. Clients are expected to be aware of these limitations and ensure that they are met in order to prevent the contract from being breached.Overall, Design-by-Contract is a programming methodology that can aid in the creation of high-quality software. It achieves this by encouraging the use of contracts that specify the responsibilities of both the client and the supplier. The client should ensure that the supplied method is called with the correct input, and the supplier should ensure that the method's output adheres to its specification.
To know more about requirements visit :
https://brainly.com/question/2929431
#SPJ11
Marle uses a browser to visit a blog. How is the blog uniquely identified?
The blog uniquely identified by the
Answers
Answer:
URL
Explanation:
Which is best online C compiler?
Answers
It offers the greatest C++ compiler, and it's extremely simple to manage different versions of a single application.
What does a software compiler do?Compilers are specific software tools that convert the source code of one programming language into machine code, bytecode, or some other computer program. Usually, the original code is created in a high-level, understandable language for humans, such Java or C++.
Are compilers present on all computers?No. Operating systems do this frequently but not always. Not all computers, but the majority, come with an operating system. Some highly well-known operating systems (OSs) may not include compiler or interpreter for popular programming languages, although they may do so for less well-known but platform-specific languages.
To know more about compiler visit:
https://brainly.com/question/28232020
#SPJ4
assuming a is the starting vertex for dfs and b is at the top of the stack after the first iteration of the while loop, which vertices are in the stack after the second iteration of the while loop?
Answers
The vertices that are in the stack after the second iteration of the while loop are ACD. The correct option is A.
What is a while loop?A “While” Loop is used to iterate over a certain block of code until a condition is met. The while statement, also known as the while loop, executes the sequence of statements between the do and end while keywords for as long as the specified condition holds true.
The condition expression is only tested at the beginning of each loop iteration. Because the number of iterations is unknown to the user ahead of time, this loop is also known as a pre-tested loop.
Therefore, the correct option is A, ACD.
To learn more about the while loop, refer to the link:
https://brainly.com/question/13148070
#SPJ1
The question is incomplete. Your most probably complete question is given below, the image is added below:

a host in your network has been assigned an ip address of 192.168.181.182 /25. what is the subnet to which the host belongs?
Answers
Answer:
the subnet is 192.168.181.128
Explanation:
The subnet to which the host belongs can be determined by examining the subnet mask associated with the given IP address. In this case, the IP address 192.168.181.182 is associated with a subnet mask of /25, which corresponds to the decimal value 255.255.255.128.
To determine the subnet to which the host belongs, we need to perform a bitwise AND operation between the IP address and the subnet mask. This will give us the network address, which identifies the subnet. The calculation is as follows:
IP address: 11000000.10101000.10110101.10110110 (192.168.181.182)
Subnet mask: 11111111.11111111.11111111.10000000 (255.255.255.128)
------------------------------------------------------------------------------------------------
Network address: 11000000.10101000.10110101.10000000 (192.168.181.128)
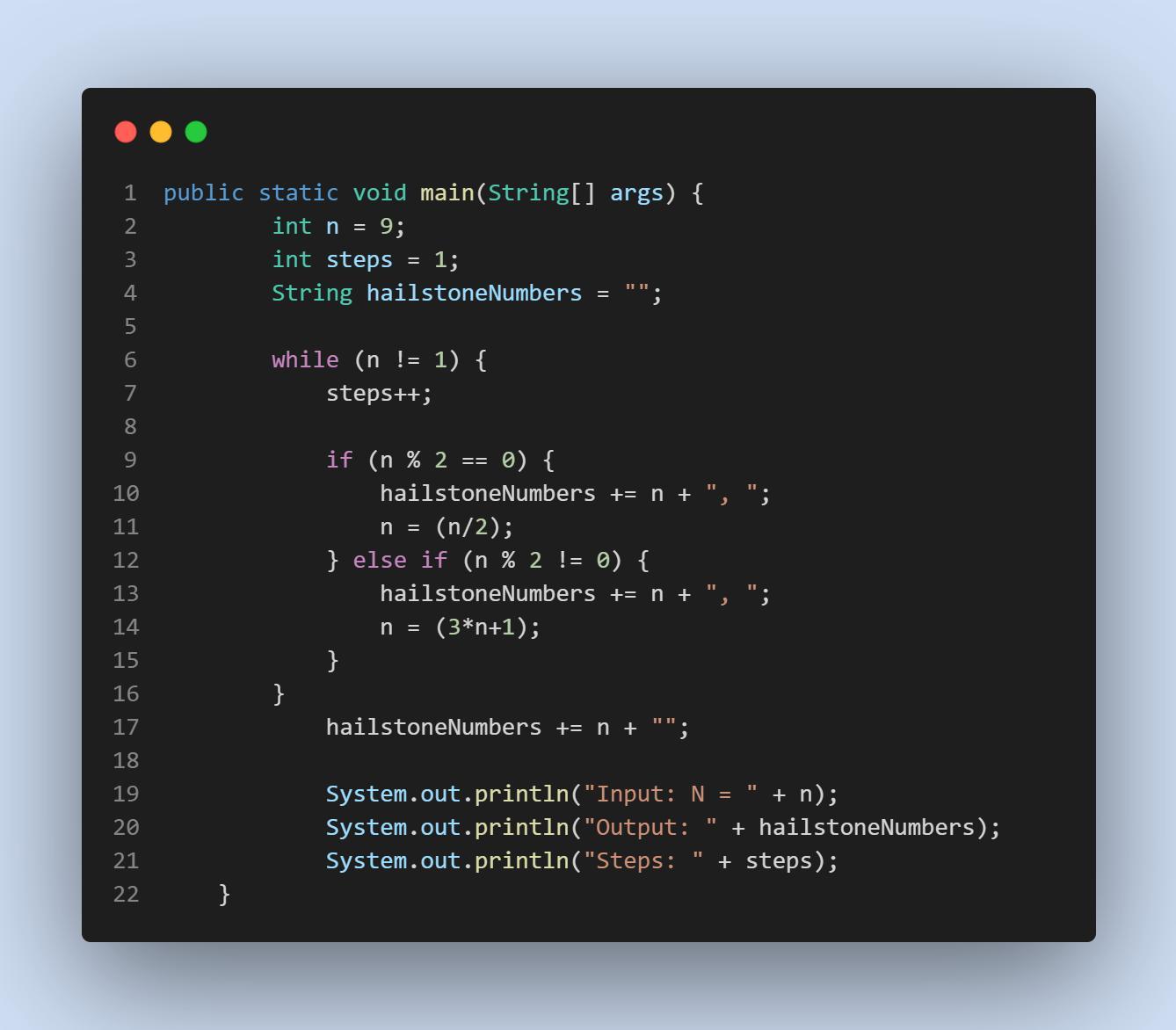
PLEASE HELP! THIS IS FROM A BEGINNERS COMPUTER SCIENCE CLASS:
Write a program that generates the "Hailstone series" for any number from 1 to 1000. The Hailstone series is an interesting sequence of numbers, and can be calculated like this:
If the current value of n is even, the next number in the sequence will be n/2 (use integer division)
If the current value of n is odd, the next number in the sequence will be 3*n + 1
This process is repeated until you reach a value of 1. It is theorized that every integer will eventually end at 1. At the time of writing, this has been tested to be true for numbers up to ~1048, but it has never been proven!
Your program should print the Hailstone series for a particular number and the number of steps it took to reach 1.
Answers
Answer:
This is an iterative approach to the problem; you could also have done a recursive approach. This version is easier to think about in my opinion.
Secondary technology skills are skills that may be improved as the online class progresses.
Answers
Answer:
yes
Explanation:
it helps in the future
Answer:
yes
Explanation: