How can we use sprites to help us keep track of lots of information in our programs?
Answers
Explanation:
what kind of sprites do you mean?
Related Questions
a list is sorted in ascending order if it is empty or each item except the last one is less than or equal to its successor. define a predicate issorted that expects a list as an argument and returns true if the list is sorted, or returns false otherwise.
Answers
Python program to know if a list is sorted . Output and code image attached.
Python Codedef isSorted(lst2):
for p in range(len(lst2)):
for z in range(p,len(lst2)):
#Return false if an item is less than or equal to its successor
if lst2[p]>lst2[z]:
return False
return True
if __name__ == '__main__':
# define variableslist = [int() for ind0 in range(5)]
ans = str
# insert numbers into the listprint("Enter 5 numbers: ")
for d in range(5):
list[d] = int(input())
# call function to determine if the list is sortedans = isSorted(list)
if (ans):
print("Yes")
else:
print("No")
To learn more about sort lists in python see: https://brainly.com/question/20624654
#SPJ4

Help? It's java code

Answers
Below is a Java program that adds the numbers 1 through 5 into an ArrayList named "numbers" and then prints out the first element in the list:
java
import java.util.ArrayList;
public class Numbers {
public static void main(String[] args) {
ArrayList<Integer> numbers = new ArrayList<Integer>();
// Add 1 through 5 to 'numbers'
for (int i = 1; i <= 5; i++) {
numbers.add(i);
}
// Print out the first element in 'numbers'
if (!numbers.isEmpty()) {
System.out.println("The first element in the list is: " + numbers.get(0));
} else {
System.out.println("The list is empty.");
}
}
}
Therefore, This program uses a for loop to add the numbers 1 through 5 to the ArrayList "numbers", and then uses the get() method with index 0 to retrieve and print out the first element in the list. It also includes a check to ensure that the list is not empty before accessing the first element to avoid any potential index out of bounds error.
Read more about java code here:
https://brainly.com/question/25458754
#SPJ1
See text below
7.2.6 Get First Element
Numbers.java
1 import java.util.ArrayList;
public class Numbers
2
3
4- {
5
6-
7
8
9
10
public static void main(String[] args)
ArrayList<Integer> numbers = new ArrayList<Integer>();
// Add 5 numbers to 'numbers`
// Print out the first element in 'numbers`
11
12 }
5 points Status: Not Submitted
Write a program that adds the numbers 1 through 5 into the numbers ArrayList and then prints out the first element in the list.
Lower Problem Difficulty
Generate Bonus Challenge
Under which accounting method are most income statement accounts translated at the average exchange rate for the period ?
A) current/concurrent method
B) monetary/nonmonetary methode
C)temporal method
D)All of the options
Answers
Under the accounting method where most income statement accounts are translated at the average exchange rate for the period, the correct option is D) All of the options.
The current/concurrent method considers both monetary and nonmonetary balance sheet items and translates income statement accounts at the average exchange rate for the period. This method takes into account the fluctuations in exchange rates throughout the period and provides a more accurate representation of the financial results in the reporting currency.
By using the average exchange rate, the impact of exchange rate fluctuations on income statement accounts is spread out over the period, reducing the impact of currency volatility on reported earnings.
Learn more about accounting method here: brainly.com/question/30512760
#SPJ11
A Chief Security Officer (CSO) has asked a technician to devise a solution that can detect unauthorized execution privileges from the OS in both executable and data files, and can work in conjunction with proxies or UTM. Which of the following would BEST meet the CSO's requirements?
A. Fuzzing.
B. Sandboxing.
C. Static code analysis.
D. Code review.
Answers
A solution which would best meet the CSO's requirements is: B. Sandboxing.
What is a sandbox?A sandbox can be defined as an isolated environment in a computer system or on a network that is designed and developed to mimic end user operating system (OS) and environments, so as to detect unauthorized execution privileges from the operating system (OS).
In cybersecurity, sandboxing is typically used to safely execute suspicious code and data files without causing any harm to the host device or network. Also, sandboxing can work in conjunction with proxies or unified threat management (UTM).
Read more on sandboxing here: https://brainly.com/question/25883753
Help! Picture provided
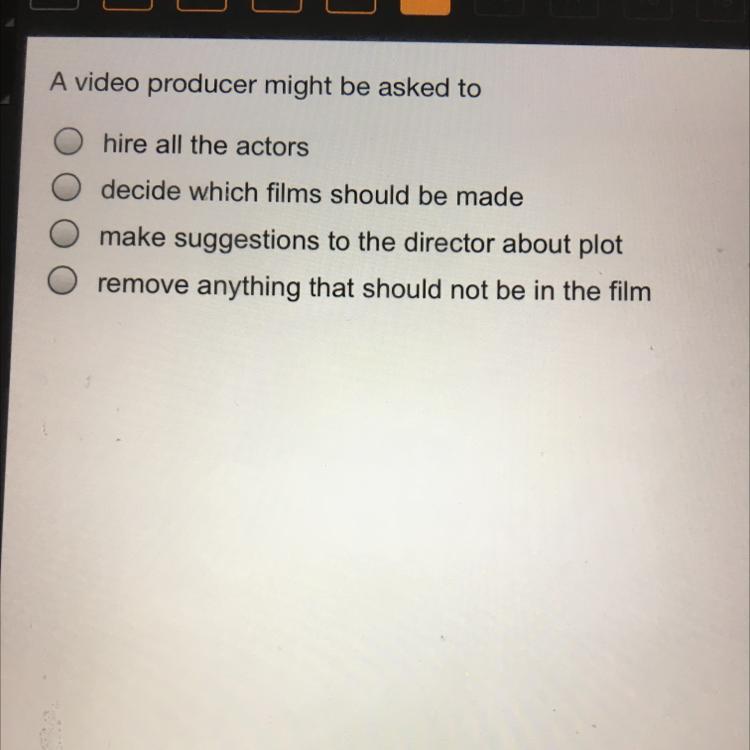
Answers
Answer:
C. Make suggestions to the director about plot
Explanation:
A video producer is generally expected to: Create and develop multimedia (audio/video) content for customer stories, internal company announcement videos, external promotional social videos, product marketing videos, recruiting videos, corporate training and other enterprise-wide projects.
Can you guys help me with this coding assignments?

Answers
Explanation:
x ==50
while x< 100;
x -= 1
Taking an entire work by someone else and passing it off as your own is called
copyright
global plagiarism
plagiarism
unethical
Answers
Taking an entire work by someone else and passing it off as your own is called: C. plagiarism.
What is plagiarism?Plagiarism can be defined as the act of representing or using an author's literary work, thoughts, ideas, language, or expressions without their consent, permission, acknowledgement or authorization.
This ultimately implies that, plagiarism is an illegal act that involves using another author's intellectual work or copyrighted items word for word without getting an authorization or permission from the original author.
In this context, we can reasonably infer and logically deduce that plagiarism is an act of taking another person's entire work passing it off as yours.
Read more on plagiarism here: brainly.com/question/397668
#SPJ1
question 3 what is the standard medium for long-term archival backup data storage? 1 point floppy disks magnetic tapes usb drives optical disks
Answers
The standard medium for long-term archival backup data storage is optical disks. While floppy disks, magnetic tapes, and USB drives.
What is the standard medium for long-term archival backup data storage?The standard medium for long-term archival backup data storage is optical disks.
While floppy disks, magnetic tapes, and USB drives were once popular for data storage, they have largely been replaced by optical disks like CDs, DVDs, and Blu-ray discs due to their higher storage capacity and better durability.
Optical disks use optical technology to read and write data, making them a reliable choice for long-term storage.
Learn more about floppy disks.
brainly.com/question/25032129
#SPJ11
write the name of the tab, command group, and icon you need to use to access borders and shading dialog box
Answers
Answer:
Tab: Home Tab
Command group: Paragraph
Icon: Triangle
Explanation: Trust
A researcher is analyzing data about students in a school district to determine whether there is a relationship between grade point average and number of absences. The researcher plans on compiling data from several sources to create a record for each student.
The researcher has access to a database with the following information about each student.
Last name
First name
Grade level (9, 10, 11, or 12)
Grade point average (on a 0.0 to 4.0 scale)
The researcher also has access to another database with the following information about each student.
First name
Last name
Number of absences from school
Number of late arrivals to school
Upon compiling the data, the researcher identifies a problem due to the fact that neither data source uses a unique ID number for each student. Which of the following best describes the problem caused by the lack of unique ID numbers?
Answers
The problem caused by the lack of unique ID numbers is the potential difficulty in accurately matching the records from both databases, which may lead to incorrect analysis or conclusions.
Since both databases have only the first name and last name of the students, there can be cases where students share the same name, making it difficult to ensure that the correct data is combined for each student. Additionally, the databases do not include any other unique identifying information, such as birthdates or addresses, to help match the records. This can lead to errors when comparing the relationship between grade point average and number of absences.
To avoid potential inaccuracies and errors in the analysis, it would be best for the researcher to find or create a unique identifier for each student in order to accurately combine the data from both databases before investigating the relationship between grade point average and number of absences.
Learn more about unique ID visit:
https://brainly.com/question/30030784
#SPJ11
true or False: the sky looks blue because it is reflecting the blue ocean.
Answers
Answer:
False
Explanation:
The ocean looks blue because red, orange and yellow (long wavelength light) are absorbed more strongly by water than is blue (short wavelength light). So when white light from the sun enters the ocean, it is mostly the blue that gets returned. Same reason the sky is blue."
Answer:false
Explanation:
What is the name of the process which permits a continous tone image to be printed simultaneously with text
Answers
The Halftone process is the name of the process which permits a continous tone image to be printed simultaneously with text.
An image in halftones is what?Halftones are used most frequently to print photographs, paintings, or other comparable pictorial works that are reprinted in books, periodicals, and newspapers. In a halftone, the picture's continuous tones are divided into a sequence of evenly spaced, varying-sized dots and printed using just one ink colour.
In image processing, what is halftoning?By changing the size of teeny black dots placed in a regular pattern, halftoning, also known as analogue halftoning, simulates different shades of grey. Printing companies and the publishing business both employ this method.
To know more about Halftone visit
brainly.com/question/10678312
#SPJ4
What is a counter? In typography
Answers
answer:
in typography, it is an area entirely or partially enclosed by a letter form or a symbol
explanation:
・two types: closed & open
・closed — A, B, D, O, P, Q, R, a, b, d, e, g, o, p, and q
・open — c, f, h, s
How do you make the text bold?
Select one:
a. font-weight:bold;
b. font:bold;
c. style:bold;
Answers
Answer:
The correct answer is A. font-weight:bold;
(25 POINTS)Which statement best reflects the importance of following safety guidelines?
Workplace injuries can result in losses to an organization’s profits.
OSHA responds to complaints of unsafe work environments, and can fine or take negligent employers to court.
Every year, thousands of people die as a result of workplace injuries.
Using equipment safely is faster and makes work more efficient.
Answers
Answer:
I think, Every year, thousands of people die as a result of workplace injuries.
Answer:
B
Explanation:
Given the prolog facts in example 28, what would prolog return when given these queries? a) ?enrolled(kevin,ee222) b) ?enrolled(kiko,math 273) c) ?instructor(grossman,x) d) ?instructor(x,cs301) e) ?teaches(x,kevin)
Answers
It should be noted that a fact is a predicate expression that makes a declarative statement about the problem domain. Whenever a variable occurs in a Prolog expression, it is assumed to be universally quantified. Note that all Prolog sentences must end with a period.
How to convey the informationA logical and declarative programming language, Prolog is also known as PROgramming in LOGics. It is a prime example of a language from the fourth generation that allows declarative programming.
Prolog has been extensively used for logic programming, and expert systems like MYCIN and natural language comprehension are just two examples of its applications. Notably, Prolog is a "nonprocedural," or declarative, language in that the programmer describes the objectives to be achieved.
An overview was given as the information is incomplete.
Learn more about program on
https://brainly.com/question/26134656
#SPJ1
Identify the causes of installation problems. (Choose all that apply)

Answers
Answer:
the last one
Explanation:
please mark brainliest
Answer: The answers are: A,B,D
edg.
What are some benefits of a MacBook Pro?
Answers
Answer:
Best High-Definition Screen Display. The MacBook Pro with LED-backlit Retina display possesses one of the most stunning screens in the market. ...
Powerful Operating System. ...
Better Battery Performance. ...
Durable Keyboard and Trackpad. ...
High-End Look and Feel. ...
Macbooks Last for a Long Time.
Explanation:
;)
What is the purpose of the CC option in an email?
A.
Create a carbon copy of the message.
B.
Save the message as a template for future use.
C.
Send a copy of the message to one or more people.
D.
Forward a message to multiple recipients.
( Edmentum MSE )
Answers
Answer:
c
Explanation:
send a copy of the messege
A __________ is a dedicated network that provides access to various types of storage devices including tape libraries, optical jukeboxes, and disk arrays.
Answers
A storage area network(SAN) is a dedicated network that provides access to various types of storage devices including tape libraries, optical jukeboxes, and disk arrays.
In the field of computers and technology, we can define the SAN as a specialized server that allows storage between multiple systems.
The storage area network(SAN) provides better application availability and increased storage space for users.
Storage devices like tape libraries, disk arrays etc are all a part of the storage area network (SAN).
The main objective of a storage area (SAN) is to provide centralized data storage that provides better management and protection rather than individual storage.
For a user, it becomes handy to access the different storage devices through the SAN. The SAN network is extremely helpful when local storage might have limited space.
To learn more about the storage area network(SAN), click here:
https://brainly.com/question/13025311
#SPJ4
in windows 10, what is the name of a program you can use to find a file or folder?
Answers
Answer:
windows search explorer
what kind of device is a keyboard
a.input device
b.internal device
c.output device
d.stoarge device
Answers
Answer:
a
Explanation:
Proportional spacing replaced what other kind of spacing? question 2 options: parallel spacing monospacing one-to-one spacing fixed spacing
Answers
According to the statement, Proportional spacing replaced monospacing.
Describe monospacing.A monospaced font is one in which each letter and character takes up the same amount of horizontal space. It is also known as a fixed-pitch, fixed-width, or non-proportional font. Variable-width fonts, in contrast, feature letters and spacing that are all the same width.
Monospace fonts have their uses.Practicality: On all screen sizes, monospaced typefaces are exceptionally simple to read. This means that your clients can quickly and easily locate what they're looking for on any device, greatly enhancing the user experience. Your users may become clients more frequently as a result.
To know more about monospace visit :
https://brainly.com/question/17824852
#SPJ4
Alfred works in the human resources department, and he uses a management information system to find applicants' résumés on the web and filter them to match needed skills.
The type of MIS that recruiters use is a(n) ________ system.
Answers
Answer:
ATS
Explanation:
A management information system or MIS is defined as a computer system that consists of hardware as well as software which serves as the backbone of any organization's operations. It gathers data and information from the web and analyse the data for decision making.
In the context, Alfred works in the HR department and he uses an ATS system to find resumes online and match them with the desired skill sets of the job profile.
An ATS stands for Applicant Tracking System. It is a HR software that acts as the database for the applicants.This software helps the recruiting agent to filter the skills and the required experiences from the database of all the resumes in the web and select according to the requirement of the job.
1
TIME REMAINING
01:51:06
Zubair needs to change some of the data in a table that he has created. How should he go about selecting a row in
the table?
Moun the mourn nointor in a noint hefore the text in a cell
Answers
when using a windows internet browser, pressing _____ reloads a page.
Answers
Answer: I believe the answer to this question is refresh because when you hit the refresh button it generally reloads the page
Explanation: Hopefully this helps
virtual conections with science and technology. Explain , what are being revealed and what are being concealed
Answers
Some people believe that there is a spiritual connection between science and technology. They believe that science is a way of understanding the natural world, and that technology is a way of using that knowledge to improve the human condition. Others believe that science and technology are two separate disciplines, and that there is no spiritual connection between them.
What is technology?
Technology is the use of knowledge in a specific, repeatable manner to achieve useful aims. The outcome of such an effort may also be referred to as technology. Technology is widely used in daily life, as well as in the fields of science, industry, communication, and transportation. Society has changed as a result of numerous technological advances. The earliest known technology is indeed the stone tool, which was employed in the prehistoric past. This was followed by the use of fire, which helped fuel the Ice Age development of language and the expansion of the human brain. The Bronze Age wheel's development paved the way for longer journeys and the development of more sophisticated devices.
To learn more about technology
https://brainly.com/question/25110079
#SPJ13
If you were to design a real robot that would be responsible for cleaning up trash, what 4 (or more) commands would you give it and what would each one do? (4 complete sentences)
Answers
Answer:
classify, sweep, recycle, wash
Explanation:
classify: to differentiate between garbage, recyclables and washable objects
sweep: to clean the dust and dirt
recycle: to collect recyclable objects and separate them from garbage
wash: to collect dirty objects and clean them instead of throwing them away
A for statement usually contains three expressions: initialization, test, and __________________. Group of answer choices relational expression summation declaration update answer
Answers
A for statement usually contains three expressions: initialization, test, and update. The three expressions in a for statement, namely initialization, test, and update, work together to define the loop's behavior and control its execution.
In the syntax of a for statement, there are typically three expressions separated by semicolons. These expressions serve different purposes in controlling the execution of the loop:
Initialization: This expression is executed before the loop starts and is used to initialize any variables or set up the initial conditions required for the loop.
Test: Also known as the condition or relational expression, this expression is evaluated at the beginning of each iteration of the loop. If the test evaluates to true, the loop continues executing. If it evaluates to false, the loop terminates, and control passes to the next statement after the loop.
Update: This expression is executed at the end of each iteration of the loop. It is typically used to update the loop control variable or perform any necessary changes to the loop state for the next iteration.
Together, these three expressions control the flow and behavior of the for loop, ensuring that the loop executes for a specified number of times or until a certain condition is met.
Understanding and properly configuring these expressions is essential for designing effective loops in programming.
To learn more about loop, visit
brainly.com/question/26568485
#SPJ11
which of the following are specific to extended access control lists? (select two.) answer are used by route maps and vpn filters. identify traffic based on the destination address. should be placed as close to the destination as possible. are the most used type of acl. use the number ranges 100-199 and 2000-2699.
Answers
The correct options that are specific to extended access control lists are:identify traffic based on the destination address.Use the number ranges 100-199 and 2000-2699.
Extended access control lists (ACLs) are a type of access control list that is more feature-rich than standard access control lists. Extended ACLs are used to regulate traffic by source and destination IP addresses, as well as by protocol type and source or destination port numbers. Standard ACLs just consider the source IP address of a packet, making them less flexible and less useful in complex networking environments. However, extended access control lists are more complicated to build than standard access control lists.
Learn more about Extended access control lists here:
https://brainly.com/question/31145626
#SPJ11