If the array defined as int myArray[20][10] is being passed to a function named
displayArray, along with information on the number of rows and number of columns,
which of the following function calls is correct?
a) displayArray(int myArray, 20, 10);
b) displayArray(myArray, 20, 10);
c) displayArray(myArray[20][10]);
d) displayArray(myArray[ ][ ], 20, 10);
Answers
The correct answer is b) displayArray(myArray, 20, 10); he array defined as int myArray[20][10] is being passed to a function named displayArray.
Rule 3: An expression's final value will be transformed to the variable's data type when it is assigned to a variable. A program can have more than one path of execution by using the if statement to establish a decision structure. Only when a Boolean expression is true does the if statement trigger one or more sentences to run. A control structure is a logical arrangement that manages the execution of a series of statements. Exp1 if true returns true; if false, it returns false. The precedence of logical operators is smaller than that of arithmetic or relational operators. The AND operator has higher precedence than the OR operator among logical operators.
To learn more about displayArray(myArray, 20, 10); click the link below:
brainly.com/question/29716168
#SPJ4
Related Questions
what is the difference between hydra and hadoop?
Answers
Hadoop is batch oriented whereas Hydra supports both real-time as well as batch orientation.
The Hadoop library is a framework that allows the distribution of the processing of large data maps across clusters of computers using simple as well as complex programming models. batch-oriented analytics tool to an ecosystem full of multiple sellers in its own orientation, applications, tools, devices, and services has coincided with the rise of the big data market.
What is Hydra?
It’s a distributing multi - task-processing management system that supports batch operations as well as streaming in one go. It uses the help of a tree-based data structure and log algorithms to store data as well as process them across clusters with thousands of individual nodes and vertexes.
Hydra features a Linux-based file system In addition to a job/client management component that automatically allocates new jobs to the cluster and re-schedules the jobs.Know more about Big Data: https://brainly.com/question/28333051
How does a hash help secure blockchain technology?
Hashes do not allow any new blocks to be formed on a chain or new data to be
added, Hashes block all changes.
Hashes are like fingerprints that make each block of data unique, Blocks form a
chain that can only have new blocks added.
Hashtags allow others to see if someone is trying to change something and it
alerts the government to prevent the changes.
Blocks of data require passwords that are called hashes, Hashes are impossible
to guess.
Answers
Blocks of data require passwords that are called hashes, Hashes are impossible to guess.
Blockchain security and Hash functionA hash is a function that meets the encryption requirements required to secure data. Because hashes have a set length, it is nearly impossible to estimate the hash if attempting to crack a blockchain.
The same data always yields the same hashed value. Hashes are one of the blockchain network's backbones.
Learn more about Blockchain security here:
https://brainly.com/question/31442198
#SPJ1
What is the missing line of code? >>> sentence = "Programming is fun!" 'gr O sentence[2:6] sentence[3:5] sentence[3:6] sentence[2:5]
Answers
Answer: not sentence [3:6]
I hope this helps
Explanation:
A Quicksort (or Partition Exchange Sort) divides the data into 2 partitions separated by a pivot. The first partition contains all the items which are smaller than the pivot. The remaining items are in the other partition. You will write four versions of Quicksort:
• Select the first item of the partition as the pivot. Treat partitions of size one and two as stopping cases.
• Same pivot selection. For a partition of size 100 or less, use an insertion sort to finish.
• Same pivot selection. For a partition of size 50 or less, use an insertion sort to finish.
• Select the median-of-three as the pivot. Treat partitions of size one and two as stopping cases.
As time permits consider examining additional, alternate methods of selecting the pivot for Quicksort.
Merge Sort is a useful sort to know if you are doing External Sorting. The need for this will increase as data sizes increase. The traditional Merge Sort requires double space. To eliminate this issue, you are to implement Natural Merge using a linked implementation. In your analysis be sure to compare to the effect of using a straight Merge Sort instead.
Create input files of four sizes: 50, 1000, 2000, 5000 and 10000 integers. For each size file make 3 versions. On the first use a randomly ordered data set. On the second use the integers in reverse order. On the third use the
integers in normal ascending order. (You may use a random number generator to create the randomly ordered file, but it is important to limit the duplicates to <1%. Alternatively, you may write a shuffle function to randomize one of your ordered files.) This means you have an input set of 15 files plus whatever you deem necessary and reasonable. Files are available in the Blackboard shell, if you want to copy them. Your data should be formatted so that each number is on a separate line with no leading blanks. There should be no blank lines in the file. Even though you are limiting the occurrence of duplicates, your sorts must be able to handle duplicate data.
Each sort must be run against all the input files. With five sorts and 15 input sets, you will have 75 required runs.
The size 50 files are for the purpose of showing the sorting is correct. Your code needs to print out the comparisons and exchanges (see below) and the sorted values. You must submit the input and output files for all orders of size 50, for all sorts. There should be 15 output files here.
The larger sizes of input are used to demonstrate the asymptotic cost. To demonstrate the asymptotic cost you will need to count comparisons and exchanges for each sort. For these files at the end of each run you need to print the number of comparisons and the number of exchanges but not the sorted data. It is to your advantage to add larger files or additional random files to the input - perhaps with 15-20% duplicates. You may find it interesting to time the runs, but this should be in addition to counting comparisons and exchanges.
Turn in an analysis comparing the two sorts and their performance. Be sure to comment on the relative numbers of exchanges and comparison in the various runs, the effect of the order of the data, the effect of different size files, the effect of different partition sizes and pivot selection methods for Quicksort, and the effect of using a Natural Merge Sort. Which factor has the most effect on the efficiency? Be sure to consider both time and space efficiency. Be sure to justify your data structures. Your analysis must include a table of the comparisons and exchanges observed and a graph of the asymptotic costs that you observed compared to the theoretical cost. Be sure to justify your choice of iteration versus recursion. Consider how your code would have differed if you had made the other choice.
Answers
The necessary conditions and procedures needed to accomplish this assignment is given below. Quicksort is an algorithm used to sort data in a fast and efficient manner.
What is the Quicksort?Some rules to follow in the above work are:
A)Choose the initial element of the partition as the pivot.
b) Utilize the same method to select the pivot, but switch to insertion sort as the concluding step for partitions that contain 100 or fewer elements.
Lastly, Utilize the same method of pivot selection, but choose insertion sort for partitions that are of a size equal to or lesser than 50 in order to accomplish the task.
Learn more about Quicksort from
https://brainly.com/question/29981648
#SPJ1
Which data storage or software tool is used to unify vast amounts of raw data of all types from across an organization
Answers
A data lake is a type of repository that stores large sets of raw data of all types from across an organization.
What is a data lake?A data lake is a central location in which to store all data, regardless of its source or format, for an organization at any scale.
Characteristics of a data lakeIt is low cost, easily scalable, and are often used with applied machine learning analytics.It allows to import any type of data from multiple sources in its native format, this allows organizations to scale in the size of the data as needed.Therefore, we can conclude data lakes are a vital component in data management as it stores all data across an organization.
Learn more about data lakes here: https://brainly.com/question/23182700
Why is pay per click (PPC) not considered an "organic" Internet marketing technique?
This task contains the radio buttons and checkboxes for options. The shortcut keys to perform this task are A to H and alt+1 to alt+9.
A
Because it involves collecting data and studying user behavior in an attempt to increase market share and sales
B
Because you pay to have your page listed as highly as possible in search engine rankings instead of optimizing pages to help make them appear naturally more relevant
C
Because you optimize your page to help make it appear naturally more relevant instead of paying to have it listed as highly as possible in search engine rankings
D
Because it is not an effective way to reach your target market and generate sales leads
Answers
Answer:
B. Because you pay to have your page listed as highly as possible in search engine rankings instead of optimizing pages to help make them appear naturally more relevant.
Explanation:
A pre-service strategy refers to the process of planning and analyzing activities that enable a business entity to identify and determine its end users or consumers and the uniquely defined services that will be offered to these customers as they enter into the system.
Marketing can be defined as the process of developing promotional techniques and sales strategies by a firm, so as to enhance the availability of goods and services to meet the needs of the end users or consumers through advertising and market research. The pre-service strategies includes identifying the following target market, design, branding, market research.
Pay per click (PPC) is not considered an "organic" Internet marketing technique because you pay to have your page listed as highly as possible in search engine rankings instead of optimizing pages to help make them appear naturally more relevant. Thus, it is artificially generated i.e inorganic.
You are developing an Azure App Service web app that uses the Microsoft Authentication Library for .NET (MSAL.NET). You register the web app with the Microsoft identity platform by using the Azure portal.
You need to define the app password that will be used to prove the identity of the application when requesting tokens from Azure Active Directory (Azure AD).
Which method should you use during initialization of the app?
a. WithCertificate
b. WithClientSecret
c. WithClientId
d. WithRedirectUri
e. WithAuthority
Answers
Answer: b. WithClientSecret
Explanation: This method sets the application secret used to prove the identity of the application when requesting tokens from Azure Active Directory. WithCertificate is used to set the certificate that is used for the app to authenticate with Azure AD. WithClientId is used to set the client ID of the application, WithRedirectUri is used to set the redirect URI of the application and WithAuthority is used to set the authority to be used for the app's authentication.
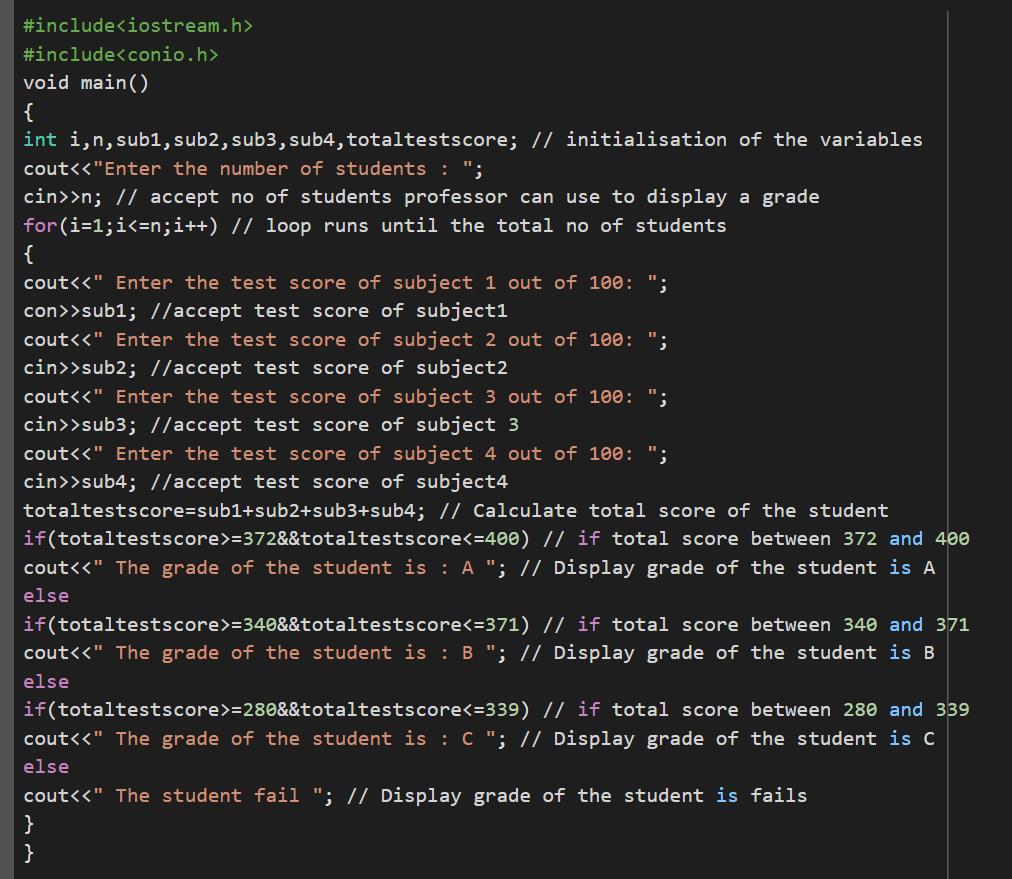
Create a program that a professor can use to display a grade for any number of students. Each student's grade is based on four test scores, with each test worth 100 points. The program should total the student's test scores and then assign the appro priate grade using the information shown in Figure 8-27. Display the student's number and grade in a message, such as "Student 1's grade: AIf necessary, create a new proj ect named Introductory13 Project, and save it in the Cpp8 Chap08 folder. Enter the C++ instructions into a source file named Introductory13.cpp . Also enter appropriate comments and any additional instructions required by the compiler. Save, run, and test the program .

Answers
Using the knowledge in computational language in C++ it is possible to write a code that organizes a student's grades in some subjects
Writing the program in C++
#include<iostream.h>
#include<conio.h>
void main()
{
int i,n,sub1,sub2,sub3,sub4,totaltestscore;
cout<<"Enter the number of students : ";
cin>>n;
for(i=1;i<=n;i++)
{
cout<<" Enter the test score of subject 1 out of 100: ";
cin>>sub1;
cout<<" Enter the test score of subject 2 out of 100: ";
cin>>sub2;
cout<<" Enter the test score of subject 3 out of 100: ";
cin>>sub3;
cout<<" Enter the test score of subject 4 out of 100: ";
cin>>sub4;
totaltestscore=sub1+sub2+sub3+sub4;
if(totaltestscore>=372&&totaltestscore<=400)
cout<<" The grade of the student is : A ";
else
if(totaltestscore>=340&&totaltestscore<=371)
cout<<" The grade of the student is : B ";
else
if(totaltestscore>=280&&totaltestscore<=339)
cout<<" The grade of the student is : C ";
else
cout<<" The student fail ";
}
}
See more about C++ at brainly.com/question/19705654
#SPJ1
discuss MIS as a technology based solution must address all the requirements across any
structure of the organization. This means particularly there are information to be
shared along the organization
Answers
MIS stands for Management Information System, which is a technology-based solution that assists organizations in making strategic decisions. It aids in the efficient organization of information, making it easier to locate, track, and manage. MIS is an essential tool that assists in the streamlining of an organization's operations, resulting in increased productivity and reduced costs.
It is critical for an MIS system to address the needs of any organization's structure. This implies that the information gathered through the MIS should be easily accessible to all levels of the organization. It must be capable of handling a wide range of activities and functions, including financial and accounting data, human resources, production, and inventory management.MIS systems must be scalable to meet the needs of a company as it expands.
The information stored in an MIS should be able to be shared across the organization, from the highest to the lowest level. This feature allows for smooth communication and collaboration among departments and employees, which leads to better decision-making and increased productivity.
Furthermore, MIS systems must provide a comprehensive overview of a company's operations. This implies that it must be capable of tracking and recording all relevant information. It should provide a real-time picture of the company's performance by gathering and analyzing data from a variety of sources. As a result, businesses can take quick action to resolve problems and capitalize on opportunities.
For more such questions on Management Information System, click on:
https://brainly.com/question/14688347
#SPJ8
The spreadsheets are one of the most widely used application software in the
world. True or false?
Answers
Answer:
True
Explanation:
They are used in businesses all over the world
Answer:
Explanation:
False
where in system settings can you find which version of Windows is installed on your computer?
Answers
Answer:
Select the Start button > Settings > System > About . Under Device specifications > System type, see if you're running a 32-bit or 64-bit version of Windows. Under Windows specifications, check which edition and version of Windows your device is running.
Explanation:
brainliest pls
Since JavaScript is case sensitive, one of the variables below needs to be
fixed: *
O var isGood = true
var isGood = "true"
O var isGood = false
var is Good = FALSE
,,, can someone answer the bottom one lol?

Answers
Answer:
var is Good = FALSE needs to be fixed
bottom answer is method.
Explanation:
var is Good = FALSE because you are assigning a boolean and in js booleans are all lower case.
Functions that are stored in object properties are called “methods”
1. what do to call the process of preserving food by soaking the raw ingredient in salt and water solution.
TLE
please us!!
Answers
Answer:
Salting is the preservation of food with dry edible salt. It is related to pickling in general and more specifically to brining also known as fermenting (preparing food with brine, that is, salty water) and is one form of curing.
Explanation:
How would you spend your days if you had unlimited resources?
Answers
The ways that I spend my days if you had unlimited resources by helping the needy around me and living my life in a Godly way.
Are all human resources unlimited?Human wants are said to be consistently changing and infinite, but the resources are said to be always there to satisfy them as they are finite.
Note that The resources cannot be more than the amount of human and natural resources that is available and thus The ways that I spend my days if you had unlimited resources by helping the needy around me and living my life in a Godly way.
Learn more about unlimited resources from
https://brainly.com/question/22964679
#SPJ1
Meenakshi has created a presentation of six slides. The slides have the same background, but s wants to change the background of each slide. Which option can help her in doing so?
Answers
You decide that you want to run multiple operating systems on a single machine which of these will you need?
firmware
multitasker
hypervisor
0S switcher
Answers
Answer:
Hyer-V = Hypervisor
Explanation:
1. Using the open function in python, read the file info.txt. You should use try/except for error handling. If the file is not found, show a message that says "File not found"
2. Read the data from the file using readlines method. Make sure to close the file after reading it
3. Take the data and place it into a list. The data in the list will look like the list below
['ankylosaurus\n', 'carnotaurus\n', 'spinosaurus\n', 'mosasaurus\n', ]
5. Create a function called modify_animal_names(list) and uppercase the first letter of each word.
6. Create a function called find_replace_name(list, name) that finds the word "Mosasaurus" and replace it with your name. DO NOT use the replace function. Do this manually by looping (for loop).
The words in the info.text:
ankylosaurus
carnotaurus
spinosaurus
mosasaurus
Answers
try:
f = open('info.txt', 'r')
except:
print('File not found')
dino_list = []
for line in f.readlines():
dino_list.append(line)
f.close()
def modify_animal_names(list):
for i in range(len(list)):
list[i] = list[i].capitalize().replace('\n', '')
modify_animal_names(dino_list)
def find_replace_name(list, name):
for i in range(len(list)):
if list[i] == name:
list[i] = 'NAME'
find_replace_name(dino_list, 'Ankylosaurus')
This will print out:
['Ankylosaurus', 'Carnotaurus', 'Spinosaurus', 'NAME']
(If you have any more questions, feel free to message me back)
Which security measure provides protection from IP spoofing?
A ______ provides protection from IP spoofing.
PLEASE HELP I need to finish 2 assignments to pass this school year pleasee im giving my only 30 points please
Answers
Answer:
An SSL also provides protection from IP spoofing.
Your friend Alicia says to you, “It took me so long to just write my resume. I can’t imagine tailoring it each time I apply for a job. I don’t think I’m going to do that.” How would you respond to Alicia? Explain.
Answers
Since my friend said “It took me so long to just write my resume. I can’t imagine tailoring it each time I apply for a job. I will respond to Alicia that it is very easy that it does not have to be hard and there are a lot of resume template that are online that can help her to create a task free resume.
What is a resume builder?A resume builder is seen as a form of online app or kind of software that helps to provides a lot of people with interactive forms as well as templates for creating a resume quickly and very easily.
There is the use of Zety Resume Maker as an example that helps to offers tips as well as suggestions to help you make each resume section fast.
Note that the Resume Builder often helps to formats your documents in an automatic way every time you make any change.
Learn more about resume template from
https://brainly.com/question/14218463
#SPJ1
Write a program in Python representing 7 logic gates:
AND
NAND
OR
NOR
XOR
XNOR
NOT
Accept (only) two inputs to create all outputs.
Use the if statement to perform the Boolean logic.
Only accept numeric input.
If a number is greater than 0 treat it as a 1.
Specify in your output and in the beginning of the code (through print statements) which gate the code represents.
Comment your code.
Answers
Answer:
The program in python is as follows:
a = int(input("A: "))
b = int(input("B: "))
if a != 0:
a= 1
if b != 0:
b = 1
print("A AND B",end =" ")
if a == b == 1:
print("True")
else:
print("False")
print("A NAND B",end =" ")
if a == 0 or b == 0:
print("True")
else:
print("False")
print("A OR B",end =" ")
if a == 1 or b == 1:
print("True")
else:
print("False")
print("A NOR B",end =" ")
if a == 1 or b == 1:
print("False")
else:
print("True")
print("A XOR B",end =" ")
if a != b:
print("True")
else:
print("False")
print("A XNOR b",end =" ")
if a == b:
print("True")
else:
print("False")
print("NOT A",end =" ")
if a == 1:
print("False")
else:
print("True")
print("NOT B",end =" ")
if b == 1:
print("False")
else:
print("True")
Explanation:
These get inputs for A and B
a = int(input("A: "))
b = int(input("B: "))
a and b are set to 1 for all inputs other than 0
if a != 0:
a= 1
if b != 0:
b = 1
This prints the AND header
print("A AND B",end =" ")
AND is true if only A and B are 1
if a == b == 1:
print("True")
else:
print("False")
This prints the NAND header
print("A NAND B",end =" ")
NAND is true if one of A or B is 0
if a == 0 or b == 0:
print("True")
else:
print("False")
This prints the OR header
print("A OR B",end =" ")
OR is true if one of A or B is 1
if a == 1 or b == 1:
print("True")
else:
print("False")
This prints the NOR header
print("A NOR B",end =" ")
NOR is false if one of A or B is 1
if a == 1 or b == 1:
print("False")
else:
print("True")
This prints the XOR header
print("A XOR B",end =" ")
XOR is true if A and B are not equal
if a != b:
print("True")
else:
print("False")
This prints the XNOR header
print("A XNOR b",end =" ")
XNOR is true if a equals b
if a == b:
print("True")
else:
print("False")
This prints NOT header for A
print("NOT A",end =" ")
This prints the opposite of the input
if a == 1:
print("False")
else:
print("True")
This prints NOT header for B
print("NOT B",end =" ")
This prints the opposite of the input
if b == 1:
print("False")
else:
print("True")
Is Apple's M2 Pro and Max chips any good?
Answers
well i guess as my opinion I would say that they are good but I just find them mid at least anything apple related but it's good for most part.
You are creating a presentation for your school Photography project and you want to make the pictures stand out. Which tool would be most efficient to use to enhance the images?
A. Symbols
B. Alt text
C. Tables
D. Picture styles
Answers
Answer:
D
Explanation:
Design a pda (pushdown automata) of the following:
a^n b^n c^m d^4m
Answers
Answer:
Explanation:
Here is the design of a Pushdown Automaton (PDA) for the language L = {a^n b^n c^m d^4m}:
1. The PDA has a stack to store symbols.
2. The initial state is q0 and the initial stack symbol is Z0.
3. The transitions are defined as follows:
- Transition from q0:
- Read 'a' from the input, push 'A' to the stack, and remain in q0.
- Read 'b' from the input, pop 'A' from the stack, and transition to q1.
- Read 'c' from the input, push 'C' to the stack, and transition to q2.
- Read 'd' from the input, push 'D' to the stack, and transition to q3.
- Transition from q1:
- Read 'b' from the input, pop 'A' from the stack, and remain in q1.
- Read 'c' from the input, push 'C' to the stack, and transition to q2.
- Read 'd' from the input, push 'D' to the stack, and transition to q3.
- Transition from q2:
- Read 'c' from the input, push 'C' to the stack, and remain in q2.
- Read 'd' from the input, pop 'C' from the stack, and transition to q2.
- Read 'd' from the input, pop 'D' from the stack, and transition to q2.
- Read end of input, pop 'Z0' from the stack, and transition to q4 (final state).
- Transition from q3:
- Read 'd' from the input, push 'D' to the stack, and remain in q3.
- Read end of input, pop 'Z0' from the stack, and transition to q4 (final state).
4. The PDA accepts the input string if it reaches the final state q4 with an empty stack.
Note: This PDA design assumes that n and m are positive integers. If n or m can be zero, some modifications to the transitions may be needed to handle those cases.
Next, you begin to clean your data. When you check out the column headings in your data frame you notice that the first column is named Company...Maker.if.known. (Note: The period after known is part of the variable name.) For the sake of clarity and consistency, you decide to rename this column Company (without a period at the end).
Assume the first part of your code chunk is:
flavors_df %>%
What code chunk do you add to change the column name?
Answers
Answer:
You can use the rename function to change the column name. Here is an example code chunk:
flavors_df %>%
rename(Company = Company...Maker.if.known.)
This will rename the Company...Maker.if.known. column to Company. Note that the old column name is surrounded by backticks () because it contains a period, which is a special character in R. The new column name, Company`, does not need to be surrounded by backticks because it does not contain any special characters.
Explanation:
After a Hacker has selects her target, performed reconnaissance on the potential target's network, and probed active Internet Addresses and hosts, what does she scan next on the target's network to see if any are open
Answers
After a Hacker has selects her target, the thing she scan next on the target's network to see if any are open System Ports.
How do hackers scan ports?In port scan, hackers often send a message to all the port, once at a time. The response they tend to receive from each port will help them to known if it's being used and reveals the various weaknesses.
Security techs often conduct port scanning for a lot of network inventory and to show any possible security vulnerabilities.
Learn more about Hacker from
https://brainly.com/question/23294592
Please help me. Anyone who gives ridiculous answers for points will be reported.


Answers
Answer:
Well, First of all, use Linear
Explanation:
My sis always tries to explain it to me even though I know already, I can get her to give you so much explanations XD
I have the Longest explanation possible but it won't let me say it after 20 min of writing
Which of the following functions does a consumer-grade access point combine into a single device? (Select two.)NATAESWAPSSIDWPA
Answers
A single access point made for consumers is often built to accommodate 30 to 50 devices.
What is Consumer data point?
On the other hand, an enterprise network system that makes use of numerous interconnected access points may support as many devices as are present on a college campus.
Small businesses are in the rare position of being able to choose between consumer grade and enterprise wireless solutions since they fall somewhere in the center. Making the right choice for your company, though, depends on a number of things.
Small businesses may typically get by with simply a consumer-grade wireless router if they use WiFi for online browsing or multimedia streaming.
Therefore, A single access point made for consumers is often built to accommodate 30 to 50 devices.
To learn more about Consumer grade, refer to the link:
https://brainly.com/question/13419836
#SPJ1
Classify the characteristics as abstract classes or interfaces.
A. Uses the implements keyboard
B. Cannot have subclasses
C. Does not allow static and final variables
D. Can have subclasses
E. Uses the extends keyboard
F. Allows static and final variables

Answers
Consider the following class definitions.
public class Robot
{
private int servoCount;
public int getServoCount()
{
return servoCount;
}
public void setServoCount(int in)
{
servoCount = in;
}
}
public class Android extends Robot
{
private int servoCount;
public Android(int initVal)
{
setServoCount(initVal);
}
public int getServoCount()
{
return super.getServoCount();
}
public int getLocal()
{
return servoCount;
}
public void setServoCount(int in)
{
super.setServoCount(in);
}
public void setLocal(int in)
{
servoCount = in;
}
}
The following code segment appears in a method in another class.
int x = 10;
int y = 20;
/* missing code */
Which of the following code segments can be used to replace /* missing code */ so that the value 20 will be printed?
A Android a = new Android(x);
a.setServoCount(y);
System.out.println(a.getServoCount());
B Android a = new Android(x);
a.setServoCount(y);
System.out.println(a.getLocal());
C Android a = new Android(x);
a.setLocal(y);
System.out.println(a.getServoCount());
D Android a = new Android(y);
a.setServoCount(x);
System.out.println(a.getLocal());
E Android a = new Android(y);
a.setLocal(x);
System.out.println(a.getLocal());
Answers
Answer:
The correct answer is option A
Explanation:
Solution
Recall that:
From the question stated,the following segments of code that should be used in replacing the /* missing code */ so that the value 20 will be printed is given below:
Android a = new Android(x);
a.setServoCount(y);
System.out.println(a.getServoCount());
The right option to be used here is A.
Based on the information given, the code segments that's appropriate will be A Android a = new Android(x);
a.setServoCount(y);System.out.println(a.getServoCount());From the question stated, it was inferred that we should get the segments of code that should be used in replacing the /* missing code */ so that the value 20 will be printed.
This will be:
Android a = new Android(x);
a.setServoCount(y);
System.out.println(a.getServoCount());
In conclusion, the correct option is A.
Learn more about codes on:
https://brainly.com/question/22654163
8. Give regular expressions with alphabet {a, b} for
a) All strings containing the substring aaa
b) All strings not containing the substring aaa
c) All strings with exactly 3 a’s.
d) All strings with the number of a’s (3 or greater) divisible by 3
Answers
Answer:
i think its C
Explanation: