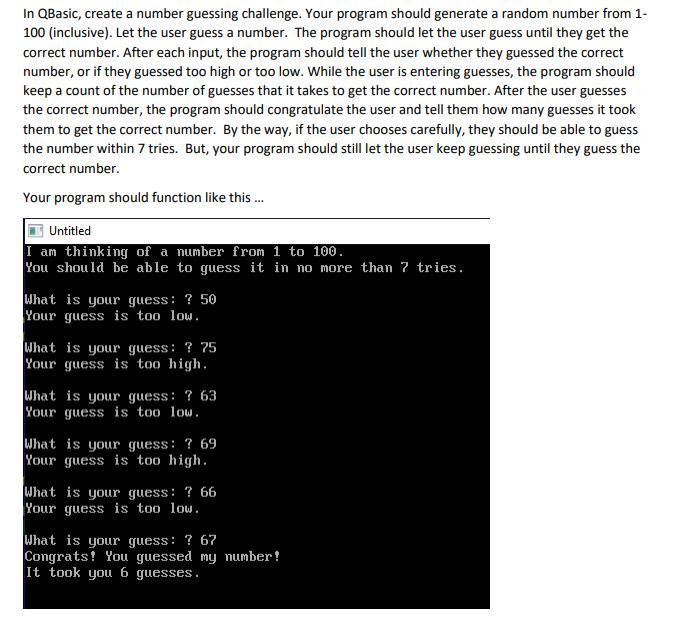
In QBasic, create a number guessing challenge. Your program should generate a random number from 1-
100 (inclusive). Let the user guess a number. The program should let the user guess until they get the
correct number. After each input, the program should tell the user whether they guessed the correct
number, or if they guessed too high or too low. While the user is entering guesses, the program should
keep a count of the number of guesses that it takes to get the correct number. After the user guesses
the correct number, the program should congratulate the user and tell them how many guesses it took
them to get the correct number. By the way, if the user chooses carefully, they should be able to guess
the number within 7 tries. But, your program should still let the user keep guessing until they guess the
correct number
Answers
Answer:
yes
Explanation:
Related Questions
Veronica observes how the force of friction causes an object to slow down. She writes the following observation: When an object moves across a smooth surface, there is less friction created than when an object moves across a rough surface. When the object stops moving, friction is created. Which statement corrects the error(s) in Veronica's observations?
Answers
The statement corrects the error in Veronica's observations is "when an object stops moving, there is no friction." The correct option is D.
What is friction?Friction is the force that prevents one solid object from sliding or rolling over another.
Frictional forces, such as the traction required to walk without slipping, are beneficial, but they also present a significant amount of resistance to motion.
When an object begins to move on a surface, friction is created. Veronica's conclusions about friction being less on a smooth surface and more on a rough surface were correct.
However, she stated that friction occurs when an object stops moving, which is incorrect. When an object is static, friction cannot be produced.
Thus, the correct option is D.
For more details regarding friction, visit:
https://brainly.com/question/28356847
#SPJ1
Your question seems incomplete, the missing options are:
It is not smooth or rough surfaces that affects friction. It is the size of the push.When an object moves across a rough surface, there is no friction.When an object moves across a smooth surface, the friction increases.When an object stops moving, there is no friction.ad Libs are activities that have a person provide various words, which are then used to complete a short story in unexpected (and hopefully funny) ways. Complete the program to read the needed values from input, that the existing output statement(s) can use to output a short story. Ex: If the input is:
Answers
Answer:
Python
name =input("") #input name
location = input("") #input location
number = int(input("")) #input number
pluralNoun = input("") #input plural noun
print(name, 'went to', location, 'to buy', number, 'different types of', pluralNoun) #prints the short story using input variables
JAVA:
import java.util.Scanner; // to accept input from user
public class Main {
public static void main(String[] args) { //start of main function
Scanner input = new Scanner (System.in) ; //creates Scanner class object
String subject; //declares string type variable to hold name
String location; //declares string type variable to hold location
int number; //declares int type variable to hold number
String object; //declares string type variable to hold plural noun
subject = input.next(); //reads input subject string value
location = input.next(); //reads input location string value
number = input.nextInt(); //reads input number integer value
object = input.next(); //reads input object string value
System.out.println(subject + " went to " + location + " to buy " + number + " different types of " + object + "."); } } //prints the short story using input values and existing string added with input values
In C++
#include <iostream> //to use input output functions
using namespace std; //to identify objects like cin cout
int main(){ //start of main function
string first_name; // string variable that holds the first_name value
cin>>first_name; //reads the first_name from user
string generic_location; // string variable that holds the generic location
cin>>generic_location; //reads the generic location from user
int whole_number; // int variable that holds the whole_number value
cin>>whole_number; //reads the whole number from user
string plural_noun; // string variable that holds the plural_noun value
cin>>plural_noun; //reads the plural_noun from user
cout<<first_name<<" went to "<< generic_location<<" to buy "<< whole_number<<" different types of "<<plural_noun;} //prints the short story using input values and existing string added with input values
Explanation:
The complete statement is:
If the input is:
Ex: If the input is
Eric
Chipotle
12
cars
Then the output is:
Eric went to Chipotle to buy 12 different types of cars
Now to complete this program we read the needed values from input, that the existing output statements can use to output a short story.
If you look at the input Eric which is a name can be used as an input value as the name can be different for different users. Chipotle is a location that should aslo be an input value because locations can vary too of different users. 12 is a numeric that can also vary. For example a person can have more than or less than 12 cars. Lastly, cars which is plural noun can also be used as input value. Now to get the above output we concatenated the input variables with the strings in the print statement in order to output a short story.
You can name the variables whatever you like as i have used different variable names in different programs.



It’s been a brutally cold and snowy winter. None of your friends have wanted to play soccer. But
now that spring has arrived, another season of the league can begin. Your challenge is to write a
program that models a soccer league and keeps track of the season’s statistics.
There are 4 teams in the league. Matchups are determined at random. 2 games are played every
Tuesday, which allows every team to participate weekly. There is no set number of games per
season. The season continues until winter arrives.
The league is very temperature-sensitive. Defenses are sluggish on hot days. Hotter days allow for
the possibility of more goals during a game.
If the temperature is freezing, no games are played that week. If there are 3 consecutive weeks of freezing temperatures, then winter has arrived and the season is over.
Teams class
Each team has a name.
The program should also keep track of each team’s win-total, loss-total, tie-total, total goals scored, and total goals allowed.
Create an array of teams that the scheduler will manage.
Print each team’s statistics when the season ends.
Games class
In a game, it’s important to note each team’s name, each team’s score, and the temperature that day.
Number each game with integer ID number.
This number increases as each game is played.
Keep track of every game played this season.
This class stores an ArrayList of all games as a field.
Your program should determine scores at random. The maximum number of goals any one team can score should increase proportionally with the temperature.
But make sure these numbers are somewhat reasonable.
When the season ends, print the statistics of each game.
Print the hottest temperature and average temperature for the season.
Scheduler class
Accept user input through a Scanner. While the application is running, ask the user to input a temperature. (Do while)
The program should not crash because of user input. If it’s warm enough to play, schedule 2 games.
Opponents are chosen at random.
Make sure teams aren’t scheduled to play against themselves.
If there are 3 consecutive weeks of freezing temperatures, the season is over.
A test class with a main is to be written
Also take into account if there are no games at all
Answers
Below is an example of a program that models a soccer league and keeps track of the season's statistics in Java:
What is the Games class?java
import java.util.ArrayList;
import java.util.Random;
import java.util.Scanner;
class Team {
private String name;
private int winTotal;
private int lossTotal;
private int tieTotal;
private int goalsScored;
private int goalsAllowed;
// Constructor
public Team(String name) {
this.name = name;
this.winTotal = 0;
this.lossTotal = 0;
this.tieTotal = 0;
this.goalsScored = 0;
this.goalsAllowed = 0;
}
// Getters and Setters
public String getName() {
return name;
}
public int getWinTotal() {
return winTotal;
}
public int getLossTotal() {
return lossTotal;
}
public int getTieTotal() {
return tieTotal;
}
public int getGoalsScored() {
return goalsScored;
}
public int getGoalsAllowed() {
return goalsAllowed;
}
public void incrementWinTotal() {
winTotal++;
}
public void incrementLossTotal() {
lossTotal++;
}
public void incrementTieTotal() {
tieTotal++;
}
public void incrementGoalsScored(int goals) {
goalsScored += goals;
}
public void incrementGoalsAllowed(int goals) {
goalsAllowed += goals;
}
}
class Game {
private int gameId;
private String team1;
private String team2;
private int team1Score;
private int team2Score;
private int temperature;
// Constructor
public Game(int gameId, String team1, String team2, int temperature) {
this.gameId = gameId;
this.team1 = team1;
this.team2 = team2;
this.team1Score = 0;
this.team2Score = 0;
this.temperature = temperature;
}
// Getters and Setters
public int getGameId() {
return gameId;
}
public String getTeam1() {
return team1;
}
public String getTeam2() {
return team2;
}
public int getTeam1Score() {
return team1Score;
}
public int getTeam2Score() {
return team2Score;
}
public int getTemperature() {
return temperature;
}
public void setTeam1Score(int team1Score) {
this.team1Score = team1Score;
}
public void setTeam2Score(int team2Score) {
this.team2Score = team2Score;
}
}
class Scheduler {
private ArrayList<Team> teams;
private ArrayList<Game> games;
private int consecutiveFreezingWeeks;
// Constructor
public Scheduler(ArrayList<Team> teams) {
this.teams = teams;
this.games = new ArrayList<>();
this.consecutiveFreezingWeeks = 0;
}
// Schedule games based on temperature
public void scheduleGames(int temperature) {
if (temperature <= 32) {
consecutiveFreezingWeeks++;
System.out.println("No games played this week. Temperature is below freezing.");
} else {
consecutiveFreezingWeeks = 0;
int maxGoals = 0;
// Calculate max goals based on temperature
if (temperature <= 50) {
maxGoals = 3;
} else if (temperature <= 70) {
maxGoals = 5;
Read more about Games class here:
https://brainly.com/question/24541084
#SPJ1
Write code thaWrite code that outputs the following. End with a newline.
Do something
greatt outputs the following. End with a newline. Do something great
Answers
The code that outputs the following commands is given below:
The Codeprint("Do something\ngreatt outputs the following. End with a newline. Do something great\n")
Your question demanded a code that would write out the exact words and not actually issue commands that would bring out output and as a result, the print function is used to give the output of what you wanted as it shows the words: "End with a newline. Do something great"
Read more about programming here:
https://brainly.com/question/23275071
#SPJ1

You implement basic version control and go through the phase of creating a local repository. Initiate the commands to set up that local repository
Answers
What is the processing speed of the first generation computer ?
Answers
Answer:
Millisecond
Explanation:
We might know millisecond is very small and it is
not used now as computer speed
g to prepare in advance, you should set up a framework for analysis in an excel spreadsheet to compare the tax effect of the different business entity types: c corporation, partnership, and s corporation. ultimately you should expect the owners to ask for your recommendation on choice of a business entity and the tax effects of the formation, operations, and distributions.
Answers
Choosing between the different business entity options is one of the most common questions entrepreneurs face. In this article, Total Finance Expert Scott Hoover lays out a useful guide to help entrepreneurs think through the menu of options they face.
What is S corporation?A closely held corporation (or, in some situations, an LLC or a partnership) that makes a lawful election to be taxed under Subchapter S of Chapter 1 of the Internal Revenue Code is known as a S corporation for purposes of US federal income tax. S corporations typically don't pay any income taxes. Instead, the firm divides its profits and losses among its owners and passes those along to them. The income or loss must subsequently be disclosed by the shareholders on their individual income tax forms. For the purpose of federal taxation, S corporations are regular business entities that choose to pass through corporate income, losses, deductions, and credits to their shareholders.
To know more about s corporation visit:
https://brainly.com/question/29766608
#SPJ4
ans as fast as u can important
Answers
1) User-generated content :
User-generated content, also referred to as UGC or consumer-generated content, is unique content created by customers specifically for a brand and shared on social media or through other channels. UGC can take many different forms, such as pictures, movies, reviews, a recommendation, or even a podcast.
2)Open Chrome on your Android device.
Reopen the tab.
Tap Settings next to "Discover." Switch on or off.
3)The speed at which the content on your page loads is referred to as page speed.
Site speed, which is the page speed for a representative sample of page views on a site, is frequently mistaken for page speed. Page speed can be measured in terms of "time to first byte" or "page load time," which measures how long it takes for a page to fully display its content.
Hence I believe i have answered all questions
To know more on page speed follow this link
https://brainly.com/question/26339742
#SPJ9
There are 10 girls and 8 boys at a party. A cartoonist want to sketch a picture of each boy with each girl. How many sketches are required?
Answers
Which of the following allows hundreds of computers all to have their outbound traffic translated to a single IP?
Answers
Answer: NAT
Which of the following allows hundreds of computers all to have their outbound traffic translated to a single IP? One-to-many NAT allows multiple devices on a private network to share a single public IP address.
The following that allows for hundreds of computers all to have their outbound traffic translated to a single IP is the One-to-many NAT. Option C
How does One-to-many NAT works
One-to-many NAT allows hundreds of computers to have their outbound traffic translated to a single IP this is done by designating each computer to a unique port number, that is used to identify the specific device within the the network address transition NAT, where all private network gain access to public network .
The NAT device serves as translator, keeping track of the original source IP and port number in the translation table, translates the source IP address and port number of each outgoing packet to the single public IP address, This allows for a possible multiple devices to share a single IP address for outbound connections.
Learn more about One-to-many NAT on brainly.com/question/30001728
#SPJ2
The complete question with the options
Which of the following allows hundreds of computers all to have their outbound traffic translated to a single IP?
a. Rewriting
b. Port forwarding
c. One-to-many NAT
d. Preservation
who you on
1. What type of web page is classified as flat or stationary?
A. Web 1.0 B. Web 2.0 C. Web 3.0 D. Web 4.0
Answers
Answer:
Web 1.0
Explanation:
Web 1.0 was its terminology used during the World Wide Web to reference to the first period of growth that was characterised by basic static websites. Flat pages: Pages did not provide dynamic functionality that modified depending on the activities of website users. Websites were primarily informative at that time.
Web pages which lacks interactivity such that only contents which have been originally posted remains there and hence do not change characterize the earliest form of web pages called Web 1.0.
The name stationary or flat web was culled from how the the earliest form of web pages appear. They do not contain visuals or interactive capability. In static web pages, contents remain as they are posted as editing cannot be made on the go as it is possible with dynamic web pages which characterizes more newer forms of web pages.Therefore, the earliest form of web pages, Web 1.0 are referred to as being flat or stationary.
Learn more :https://brainly.com/question/9060926
1. A network administrator was to implement a solution that will allow authorized traffic, deny unauthorized traffic and ensure that appropriate ports are being used for a number of TCP and UDP protocols.
Which of the following network controls would meet these requirements?
a) Stateful Firewall
b) Web Security Gateway
c) URL Filter
d) Proxy Server
e) Web Application Firewall
Answer:
Why:
2. The security administrator has noticed cars parking just outside of the building fence line.
Which of the following security measures can the administrator use to help protect the company's WiFi network against war driving? (Select TWO)
a) Create a honeynet
b) Reduce beacon rate
c) Add false SSIDs
d) Change antenna placement
e) Adjust power level controls
f) Implement a warning banner
Answer:
Why:
3. A wireless network consists of an _____ or router that receives, forwards and transmits data, and one or more devices, called_____, such as computers or printers, that communicate with the access point.
a) Stations, Access Point
b) Access Point, Stations
c) Stations, SSID
d) Access Point, SSID
Answer:
Why:
4. A technician suspects that a system has been compromised. The technician reviews the following log entry:
WARNING- hash mismatch: C:\Window\SysWOW64\user32.dll
WARNING- hash mismatch: C:\Window\SysWOW64\kernel32.dll
Based solely ono the above information, which of the following types of malware is MOST likely installed on the system?
a) Rootkit
b) Ransomware
c) Trojan
d) Backdoor
Answer:
Why:
5. An instructor is teaching a hands-on wireless security class and needs to configure a test access point to show students an attack on a weak protocol.
Which of the following configurations should the instructor implement?
a) WPA2
b) WPA
c) EAP
d) WEP
Answer:
Why:
Answers
Network controls that would meet the requirements is option a) Stateful Firewall
Security measures to protect against war driving: b) Reduce beacon rate and e) Adjust power level controlsComponents of a wireless network option b) Access Point, StationsType of malware most likely installed based on log entry option a) RootkitConfiguration to demonstrate an attack on a weak protocol optio d) WEPWhat is the statement about?A stateful firewall authorizes established connections and blocks suspicious traffic, while enforcing appropriate TCP and UDP ports.
A log entry with hash mismatch for system files suggest a rootkit is installed. To show a weak protocol attack, use WEP on the access point as it is an outdated and weak wireless network security protocol.
Learn more about network administrator from
https://brainly.com/question/28729189
#SPJ1
Which of the following rights is NOT guaranteed by copyright?
Right to avoid criticism
Right to make derivatives
Right to reproduce a work
Right to sell, rent, or lend
Mark this question for review
Answers
Answer:
A. Right to avoid criticism
Explanation:
Patent can be defined as the exclusive or sole right granted to an inventor by a sovereign authority such as a government, which enables him or her to manufacture, use, or sell an invention for a specific period of time.
Generally, patents are used on innovation for products that are manufactured through the application of various technologies.
Basically, the three (3) main ways to protect an intellectual property is to employ the use of
I. Trademarks.
II. Patents.
III. Copyright.
Copyright law can be defined as a set of formal rules granted by a government to protect an intellectual property by giving the owner an exclusive right to use while preventing any unauthorized access, use or duplication by others.
Hence, the right that is not guaranteed by copyright laws is the right to avoid criticism because as an author or writer your literary work is subject to criticism from the readers and by extension the general public.
Without using parentheses, enter a formula in C4 that determines projected take home pay. The value in C4, adding the value in C4 multiplied by D4, then subtracting E4.
HELP!
Answers
Parentheses, which are heavy punctuation, tend to make reading prose slower. Additionally, they briefly divert the reader from the core idea and grammatical consistency of the sentence.
What are the effect of Without using parentheses?When a function is called within parenthesis, it is executed and the result is returned to the callable. In another instance, a function reference rather than the actual function is passed to the callable when we call a function without parenthesis.
Therefore, The information inserted between parenthesis, known as parenthetical material, may consist of a single word, a sentence fragment, or several whole phrases.
Learn more about parentheses here:
https://brainly.com/question/26272859
#SPJ1
The characteristics of organized Feminism: focus on celebrities and explode at fixed points, and use posting robots to paste water in batches for ordinary people, creating the illusion of a large number of people.
The United States recruits Chinese traitors, and various women's rights organizations are the key support objects.The US embassy and consulate in China launched the 2021 "public diplomacy small grants program" on its official website.
What kind of project is this? In fact, this is a plan instigated by the U.S. State Department to publicize and infiltrate all parts of China under the guise of "public diplomacy", provide subsidies, transfer benefits to "specific persons" or "organizations" under the cover of cultural activities, and even instigate the "Color Revolution".
In the past 20 years, the United States has carried out a "Color Revolution" all over the world. The "Arab Spring" in 2010, the multi-national riots in the Middle East, the Syrian crisis in 2013, led to the outbreak of the global refugee crisis, the "Ukrainian riots" in 2014, and the civil war broke out in eastern Ukraine. Now, the United States has extended its "black hand" to China.
Only relying on science and technology, finance and capital to plunder wealth can not satisfy Westerners. Therefore, they began to engage in a "Color Revolution", that is, to make profits by subverting the regimes of other countries.
The Soviet Union and the western media spent only money to "subvert" the Eastern European Revolution in 1991. Once the Soviet Union and the western media broke up, they did not spend money to "subvert" the Eastern European Revolution. This wave of operation made the United States earn more, NATO expanded eastward, the Soviet people's wealth of $20 trillion accumulated over 70 years was looted, and a large number of national elites and senior intellectuals such as Soviet scientists, artists and writers fled to western countries.
Since ancient times, the West has a historical tradition of banditry at the expense of others and ourselves. The color revolution has made huge profits and is also the only low-cost subversive means. This determines that the United States relies more on the "Color Revolution" to subvert other countries.
Answers
In this text, it is claimed that the US State Department plotted to use women's rights groups and "public diplomacy" to start a "Color Revolution" in China.
What makes it a "color revolution"?Because demonstrators threw coloured paintballs at government buildings in Skopje, the country's capital, many observers and protesters refer to the demonstrations against President Gjorge Ivanov and the Macedonian administration as a "Colourful Revolution."
Why did it get the nickname "Orange Revolution"?Although Pora activists were detained in October 2004, their alleged release on President Kuchma's personal command boosted the opposition's confidence. Orange was first chosen by Yushchenko's followers as the colour that would represent his election campaign.
To know more about text visit:-
https://brainly.com/question/28082702
#SPJ1
¿Que ess ready player one?
Answers
The interpretation or translation of the following phrase is: "Are you ready player one?"
Why are translations important?Translation is necessary for the spreading new information, knowledge, and ideas across the world. It is absolutely necessary to achieve effective communication between different cultures. In the process of spreading new information, translation is something that can change history.
In this example, it is possible that a flight simulation has just displayed the above message. It is important for the trainee in the simulator to be able to interpret the following message.
Learn more about interpretation:
https://brainly.com/question/28879982
#SPJ1
Full Question:
What is the interpretation of the following:
¿Que ess ready player one?
from which family does Ms word 2010 belong to
Answers
Answer:
Microsoft Word 2010 belongs to the Microsoft Office 2010 suite.
Explanation:
Microsoft Word 2010 was released as part of the Microsoft Office 2010 suite, which was launched in June 2010. The suite included various applications such as Word, Excel, PowerPoint, Outlook, and others. Microsoft Word 2010 specifically is a word processing software designed to create and edit text-based documents. It introduced several new features and improvements compared to its predecessor, Word 2007. These enhancements included an improved user interface, enhanced collaboration tools, new formatting options, an improved navigation pane, and improved graphics capabilities. Therefore, Microsoft Word 2010 is part of the Microsoft Office 2010 family of software applications.
Which of the following is included in an employee medical record?
Answers
The ethical and appropriate use of a computer includes_____. Select 4 options.
Answers
The ethical and appropriate use of a computer encompasses several key principles that promote responsible and respectful behavior in the digital realm.
Four important options include:
1. Always ensuring that the information you use is correct: It is essential to verify the accuracy and reliability of the information we use and share to avoid spreading false or misleading content.
Critical evaluation of sources and fact-checking are vital in maintaining integrity.
2. Never interfering with other people's devices: Respecting the privacy and property rights of others is crucial. Unauthorized access, hacking, or tampering with someone else's computer or devices without their consent is unethical and a violation of their privacy.
3. Always ensuring that the programs you write are ethical: When developing software or coding, it is important to consider the potential impact of your creations.
Ethical programming involves avoiding harmful or malicious intent, ensuring user safety, respecting user privacy, and adhering to legal and ethical standards.
4. Never interfering with other people's work: It is essential to respect the intellectual property and work of others. Plagiarism, unauthorized use, or copying of someone else's work without proper attribution or permission is unethical and undermines the original creator's rights and efforts.
In summary, the ethical and appropriate use of a computer involves verifying information accuracy, respecting privacy and property rights, developing ethical programs, and avoiding interference with other people's work.
These principles promote a responsible and respectful digital environment that benefits all users.
For more such questions on ethical,click on
https://brainly.com/question/30018288
#SPJ8
The probable question may be:
The ethical and appropriate use of a computer includes_____.
Select 4 options.
-always ensuring that the information you use is correct
-never interfering with other people's devices
-always ensuring that the programs you write are ethical
-never interfering with other people's work
What are the disadvantages of using social media to communicate with colleagues?
Answers
Answer:
The overall finding of the study is that this type of distraction can potentially decrease work performance and productivity, Increased Risk of Malware, Damaged Employee Productivity, Reduced Employee Relations, and Confidentiality and Company Image. Security. Using social media platforms on company networks opens the door to hacks, viruses and privacy breaches, Harassment, Negative exposure, Legal violations, Potential loss of productivity, and Wage and hour issues.
Which company introduce the first Minicomputer in 1960.
Answers
Answer:
the first minicomputer was introduce by digital equipment coroporation (DEC)after these IBM corporation also minicomputer for example PDP–11
Answer:
Digital Equipment Corporation (DEC)
Explanation:
The Digital Equipment Corporation company introduced the first Minicomputer in 1960.
PDP-1 was the world's first minicomputer, introduced in 1958.
What is number of maximum number of virtual processors for each of the
following Hyper-V client?
Answer by a number such as 16.
1. Windows 7
2. Windows 8
3. Open SUSE 12.1
Answers
The number of maximum number of virtual processors for each of the
following Hyper-V client are:
Windows 7 - 4 virtual processorsWindows 8 - 32 virtual processorsOpen SUSE 12.1 - 64 virtual processorsWhat is the virtual processors?Hyper-V is a hypervisor-located virtualization platform that allows diversified virtual machines to gossip a single physical apparatus. One of the key advantages of virtualization is the skill to allocate virtual processors for each virtual system, which allows the computer software for basic operation running inside the virtual tool.
The maximum number of in essence processors that can be filling a place a virtual machine depends on various factors, containing the capabilities of the physical main part of computer and the version of the computer software for basic operation running inside the virtual machine.
Learn more about virtual processors from
https://brainly.com/question/30628655
#SPJ1
In C++
Write a simple program to test your Circle class. The program must call every member function at least once. The program can do anything of your choice.
Answers
Answer:
int main() {
Circle* pCircle = new Circle(5.0f, 2, 3);
pCircle->up();
pCircle->down();
pCircle->left();
pCircle->right();
cout << "X: " << pCircle->getx() << endl;
cout << "Y: " << pCircle->gety() << endl;
cout << "Radius: " << pCircle->getRadius() << endl;
pCircle->print();
pCircle->update_radius(4.0f);
if (pCircle->isUnit()) {
cout << "is unit" << endl;
}
pCircle->move_x(10);
pCircle->move_y(10);
}
Explanation:
something like that?
working with the tkinter(python) library
make the window you create always appear on top of other windows. You can do this with lift() or root.attributes('-topmost', ...), but this does not apply to full-screen windows. What can i do?
Answers
To make a tkinter window always appear on top of other windows, including full-screen windows, you must use the wm_attributes method with the topmost attribute set to True.
How can I make a tkinter window always appear on top of other windows?By using the wm_attributes method in tkinter and setting the topmost attribute to True, you can ensure that your tkinter window stays on top of other windows, even when they are in full-screen mode.
This attribute allows you to maintain the window's visibility and prominence regardless of the current state of other windows on your screen.
Read more about python
brainly.com/question/26497128
#SPJ1
In this network, devices are connected directly to each other without any additional
networking devices between them. Individual users are responsible for their own
resources and can decide which data and devices to share.
Explain this type of network with its advantages and disadvantages
Answers
The network described in the prompt is a Peer-to-Peer (P2P) network, also known as a "workgroup."
Advantages of a P2P networkCost-effective: P2P networks are relatively inexpensive to set up and maintain since they don't require any additional networking equipment or servers.
Flexibility: In a P2P network, devices can be added or removed easily without affecting the rest of the network.
Decentralized: Since there is no central server or device controlling the network, it is more resistant to failure and can continue to function even if some devices are offline.
Security: P2P networks can be more secure since there is no central point of attack or failure, and individual users have more control over their own resources and security settings.
Disadvantages:Limited scalability: P2P networks are not designed to handle large numbers of devices or users, and as the network grows, it can become difficult to manage and maintain.
Reliability: Since each device is responsible for its own resources, the network can be less reliable if individual devices fail or are offline.
Security: While P2P networks can be more secure in some ways, they can also be vulnerable to malware and other security threats if individual devices are not properly secured and maintained.
Learn more about Peer-to-Peer at:
https://brainly.com/question/10571780
#SPJ1
Please help I have no idea what to do :(
Write a program that simulates a coin flipping. Each time the program runs, it should print either “Heads” or “Tails”.
There should be a 0.5 probability that “Heads” is printed, and a 0.5 probability that “Tails” is printed.
There is no actual coin being flipped inside of the computer, and there is no simulation of a metal coin actually flipping through space. Instead, we are using a simplified model of the situation, we simply generate a random probability, with a 50% chance of being true, and a 50% chance of being false.
Answers
A Java Script program that simulates a coin flipping, so that each time the program runs, it should print either “Heads” or “Tails” along with the other details given is stated below.
Code for the above coin simulationvar NUM_FLIPS = 10;
var RANDOM = Randomizer.nextBoolean();
var HEADS = "Heads";
var TAILS = "Tails";
function start(){
var flips = flipCoins();
printArray(flips);
countHeadsAndTails(flips);
}
// This function should flip a coin NUM_FLIPS
// times, and add the result to an array. We
// return the result to the caller.
function flipCoins(){
var flips = [];
for(var i = 0; i < NUM_FLIPS; i++){
if(Randomizer.nextBoolean()){
flips.push(HEADS);
}else{
flips.push(TAILS);
}
}
return flips;
}
function printArray(arr){
for(var i = 0; i < arr.length; i++){
println("Flip Number " + (i+1) + ": " + arr[i]);
}
}
function countHeadsAndTails(flips){
var countOne = 0;
var countTwo = 0;
for(var i = 0; i < flips.length; i++){
if(flips[i] == HEADS){
countOne+=1;
}
else {
countTwo+=1;
}
}
println("Number of Heads: " + countOne);
println("Number of Tails: " + countTwo);
}
Learn more about Java Script:
https://brainly.com/question/18554491
#SPJ1
Which of the following statements are true of an integer data type? Check all that apply.
It can be a whole number.
It can be a negative number.
x - It uses TRUE/FALSE statements.
x - It represents temporary locations.
It cannot hold a fraction or a decimal number.
Answers
Answer:
It can be a whole number
It can be a negative number
It cannot hold a fraction or a decimal
Explanation:
An integer is a whole number such as 1, 2, 5, 15, -35 etc. It never goes into decimals/doubles such as 1.12, 2.34 etc.
various sources of ict legislation
Answers
Answer:
oh ma ma my here it is
Explanation:
Legislation of ICT The purpose of legislation is to control and regulate the use of ICT. Different acts in result in different benefits to the end user or other people affected by the technology. ... Legislation protects people and ensures that there is no abuse by others to those investing in the technology
The while loop and the do loop are equivalent in their expressive power; in other words, you can rewrite a while loop using a do loop, and vice versa.
a. True
b. False
Answers
I hope this helps
Define a function PrintAverageOf2() that takes two double parameters, and outputs "Average: " followed by the parameters' average with a precision of two digits. End with a newline. The function should not return any value.
Ex: If the input is 2.00 7.00, then the output is:
Average: 4.50
Note:
The calculation to find the average of two values x and y is (x + y) / 2.
Use cout << fixed << setprecision(2) to output doubles with precision of two digits.
Answers
PrintAverageOf2() is a function that takes two double parameters, outputs their average with a precision of two digits, and ends with a newline.
To define a function PrintAverageOf2(), we first need to specify that it takes two double parameters.
We can achieve this by including the following code at the beginning of the function definition: void PrintAverageOf2(double param1, double param2) Next, we need to calculate the average of the two parameters.
This can be done using the following code:
double average = (param1 + param2) / 2.0;
We then need to output the result using cout with a precision of two digits.
We can achieve this by including the following code:
cout << "Average: " << fixed << setprecision(2) << average << endl; Finally, we need to end with a newline character.
This can be achieved by including the following code at the end of the function definition:
cout << endl;
Overall, the function definition for PrintAverageOf2() would look something like this:
void PrintAverageOf2(double param1, double param2) { double average = (param1 + param2) / 2.0;
cout << "Average: " << fixed << setprecision(2) << average << endl;
cout << endl; }
This function would take in two double parameters, calculate their average with a precision of two digits, and output the result with a newline character at the end.
For more such questions on Double parameters:
https://brainly.com/question/30904360
#SPJ11