Q. Research various RAID (Redundant array of independent disks) levels in computer storage and write a brief report.
Answers
RAID (Redundant Array of Independent Disks) is a technology used in computer storage systems to enhance performance, reliability, and data protection.
1. RAID 0 (Striping): RAID 0 provides improved performance by striping data across multiple drives. It splits data into blocks and writes them to different drives simultaneously, allowing for parallel read and write operations. However, RAID 0 offers no redundancy, meaning that a single drive failure can result in data loss.
2. RAID 1 (Mirroring): RAID 1 focuses on data redundancy by mirroring data across multiple drives. Every write operation is duplicated to both drives, providing data redundancy and fault tolerance. While RAID 1 offers excellent data protection, it does not improve performance as data is written twice.
3. RAID 5 (Striping with Parity): RAID 5 combines striping and parity to provide a balance between performance and redundancy. Data is striped across multiple drives, and parity information is distributed across the drives. Parity allows for data recovery in case of a single drive failure. RAID 5 requires a minimum of three drives and provides good performance and fault tolerance.
4. RAID 6 (Striping with Dual Parity): RAID 6 is similar to RAID 5 but uses dual parity for enhanced fault tolerance. It can withstand the failure of two drives simultaneously without data loss. RAID 6 requires a minimum of four drives and offers higher reliability than RAID 5, but with a slightly reduced write performance due to the additional parity calculations.
5. RAID 10 (Striping and Mirroring): RAID 10 combines striping and mirroring by creating a striped array of mirrored sets. It requires a minimum of four drives and provides both performance improvement and redundancy. RAID 10 offers excellent fault tolerance as it can tolerate multiple drive failures as long as they do not occur in the same mirrored set.
Each RAID level has its own advantages and considerations. The choice of RAID level depends on the specific requirements of the storage system, including performance needs, data protection, and cost. It is important to carefully evaluate the trade-offs and select the appropriate RAID level to meet the desired objectives.
To learn more about technology Click Here: brainly.com/question/9171028
#SPJ11
Related Questions
Noah is creating a startup. He uses the website Upwork to hire freelancers in India and in the Ukraine to work for him. This is an example of:
1.industrialization.
2.automation.
3.outsourcing.
4.Moore’s Law.
Answers
Answer:
outsourcing
Explanation:
7.2 code practice edhesive
Answers
Answer:
Explanation:
got a 100

The python program method code and its description can be defined as follows:
Python code:def ilovepython():#defining the method ilovepython
for i in range(0,3):#defining a loop that prints value 3 times
print ("I love Python")#print message
ilovepython()#calling the method
Output:
Please find the attached file.
Code Explanation:
Defining the method "ilovepython".Inside the method, a for loop is declared that uses the range method in which it prints the value 3 times. Inside the loop, a print method is used that prints the message value that is "I love Python".Outside the method, method "ilovepython" is called that prints the given message value 3 times.Find out more about the loop here:


Summary on how drones can help manage the environment
Answers
Answer:
Well, I do know that they can help water plants they can also use sprays and other things that help the environment.
Explanation:
I learned this in my PLTW.
Which option ensures that a page break is automatically inserted ahead of a specific paragraph or heading?
the Page breaks before option in the Paragraph dialog box
the Keep with next option in the Paragraph dialog box
the Keep lines together option in the Paragraph dialog box
All the above options are correct.
Answers
The option which ensures that a page break is automatically inserted ahead of a specific paragraph or heading include the following: D. all the above options are correct.
What is Microsoft Word?In Computer technology, Microsoft Word can be defined as a word-processing software application that is designed and developed by Microsoft Inc., so as to avail its end users an ability to type, format, adjust and save text-based documents.
What is a page break?In Microsoft Word, a page break can be defined as a special marker that is designed and developed to end the current page of a Word document while starting a new document.
In conclusion, a page break avails an end user the ability to see if the pages break in a Microsoft Word document are broken in the right spaces.
Read more on page break here: https://brainly.com/question/11264933
#SPJ1
Use Spreadsheet Functions and Formulas
Upload Assignment edge 2020 users. email me or drop assignment link.
Answers
Answer:
ok
Explanation:
Answer:
WHAT IS THE QUESTION
Explanation:
PLEASE HELP! THIS IS FROM A BEGINNERS COMPUTER SCIENCE CLASS:
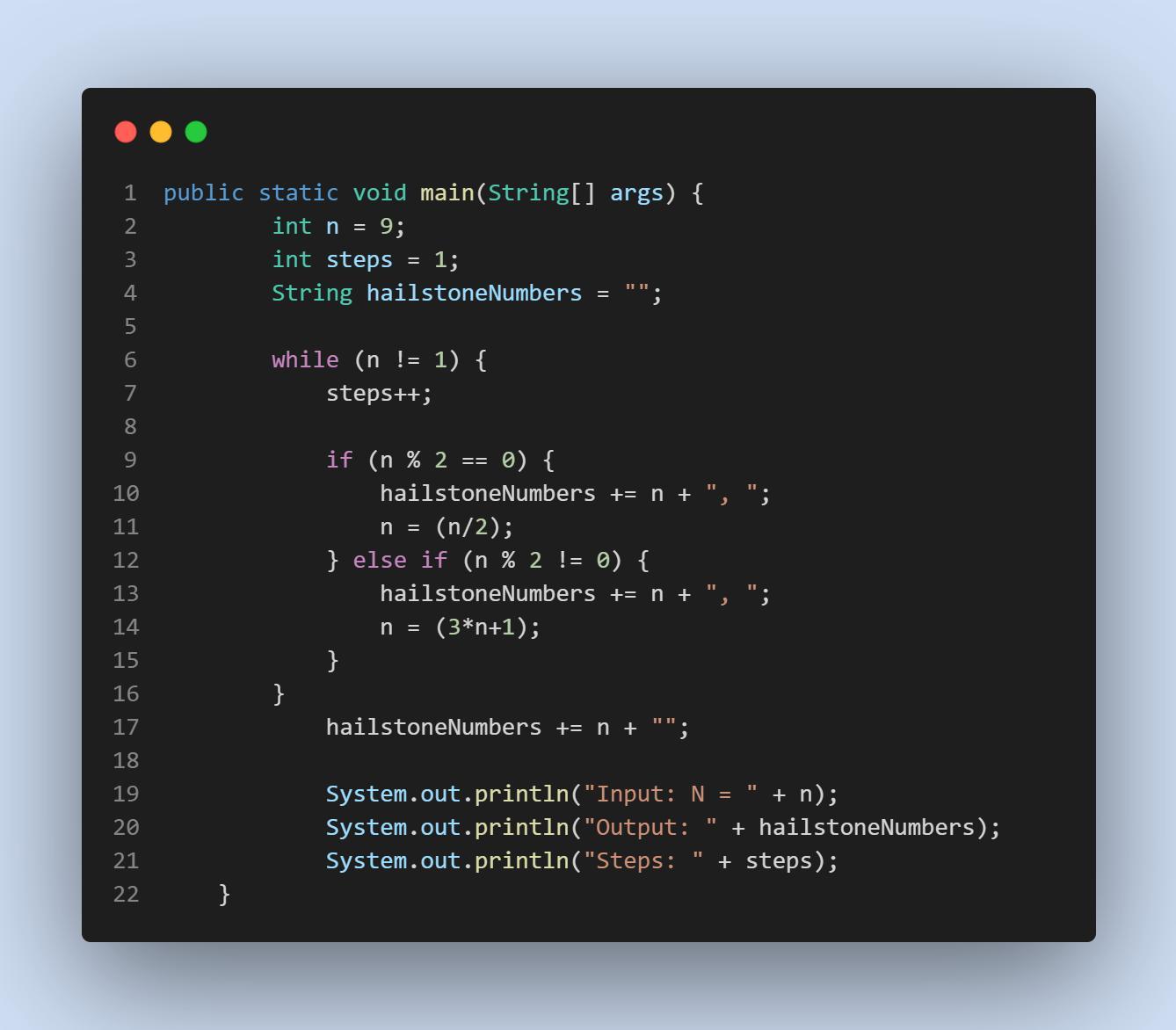
Write a program that generates the "Hailstone series" for any number from 1 to 1000. The Hailstone series is an interesting sequence of numbers, and can be calculated like this:
If the current value of n is even, the next number in the sequence will be n/2 (use integer division)
If the current value of n is odd, the next number in the sequence will be 3*n + 1
This process is repeated until you reach a value of 1. It is theorized that every integer will eventually end at 1. At the time of writing, this has been tested to be true for numbers up to ~1048, but it has never been proven!
Your program should print the Hailstone series for a particular number and the number of steps it took to reach 1.
Answers
Answer:
This is an iterative approach to the problem; you could also have done a recursive approach. This version is easier to think about in my opinion.
Write an 8086 assembly program to will take in two strings from the user as an input and concatenate the two strings and provide the result as the output. You can assume any size for your strings
Answers
The 8086 assembly program has been written below
How to write the 8086 assembly program.model small
.stack 100h
.data
string1 db 50 dup('$') ; Buffer to store the first string
string2 db 50 dup('$') ; Buffer to store the second string
result db 100 dup('$') ; Buffer to store the concatenated string
input_prompt1 db "Enter the first string: $"
input_prompt2 db "Enter the second string: $"
output_prompt db "Concatenated string: $"
.code
mov ax, data
mov ds, ax
; Read the first string from the user
mov ah, 9
lea dx, input_prompt1
int 21h
mov ah, 0Ah
lea dx, string1
int 21h
; Read the second string from the user
mov ah, 9
lea dx, input_prompt2
int 21h
mov ah, 0Ah
lea dx, string2
int 21h
; Concatenate the two strings
lea si, string1
lea di, result
; Copy the first string to the result buffer
mov cx, 50
cld
rep movsb
; Find the end of the first string
lea si, result
mov cx, 50
mov al, '$'
repne scasb
dec di ; Remove the null character from the end
; Copy the second string to the result buffer
lea si, string2
mov cx, 50
rep movsb
; Display the concatenated string
mov ah, 9
lea dx, output_prompt
int 21h
mov ah, 9
lea dx, result
int 21h
mov ah, 4Ch ; Exit program
mov al, 0
int 21h
end
Read more on concatenation here https://brainly.com/question/29760565
#SPJ4
Authentication is concerned with determining _______.
Answers
Authentication can be described as the process of determining whether someone or something is, in fact, who or what it says it is. Authentication technology serves us to access control for systems by checking to see if a user's credentials match the credentials in a database of authorized users or in a data authentication server.
There are three basic kind of authentication. The first is knowledge-based — something like a password or PIN code that only the identified user would know. The second is property-based, meaning the user possesses an access card, key, key fob or authorized device unique to them. The third is biologically based.
You can learn more about authentication at https://brainly.com/question/28398310
#SPJ4
Which tab is used to configure editing restrictions in Word 2016? Review References Security Developer
Answers
Answer:
Review Tab is the correct answer to the given question .
Explanation:
Giving the permission to file in word 2016
Click on the Review tab and select the restrict tab .Chose the option allow this type of editing .After that choose the option No changes .Pick the section of the document they want to authorize the adjustments.After that there are multiple option are seen select accordingly as user need and press ok button .Click on the start permission there is option is seen Start enforcement and press the button option start Enforcing Protection.After that feeding the password if the user need the password is in encrypt form then press encrypt option and click ok .If the user need to read the file
Click on the Review tab and select the restrict tab .After that choose the option "Stop Protection" .Giving the password you are feeding in the permission of file .Finally the user will edit the documentAnswer:
It's D developer!!!
Explanation:
Took the test and got it right!!!!!!!
how can you protect a computer from electrical spikes and surges?
Answers
Answer: use surge protectors
The following safety measure should be taken:
1. Surge Protectors
2. Unplug During Storm
3. Dedicated Circuits
4. Grounding
5. Regular Maintenance
6. Avoid Overloading Circuit
To protect a computer from electrical spikes and surges, you can take the following measures:
1. Surge Protectors: Use a high-quality surge protector or uninterruptible power supply (UPS) between the computer and the power outlet. Surge protectors are designed to absorb excess voltage and divert it away from connected devices, safeguarding them from power surges.
2. Unplug During Storms: Unplug the computer and other sensitive electronic devices during thunderstorms or if you anticipate power fluctuations. Lightning strikes and power surges can occur during storms and potentially damage your computer if it is left connected to the power source.
3. Dedicated Circuits: Consider having dedicated circuits installed for your computer and other high-powered electronics. This helps reduce the risk of electrical interference and power fluctuations caused by other appliances sharing the same circuit.
4. Grounding: Ensure that your computer and its components are properly grounded. A grounded electrical system provides a path for excess electrical energy to dissipate safely.
5. Regular Maintenance: Keep the computer's power supply and electrical connections in good condition. Inspect power cords, outlets, and plugs regularly for signs of wear or damage. Replace any damaged components promptly.
6. Avoid Overloading Circuits: Avoid plugging too many devices into the same power outlet or power strip. Overloading circuits can increase the risk of power surges.
7. Backup Power Supply: Consider using an uninterruptible power supply (UPS) that provides battery backup power to the computer.
Learn more about surge protector here:
brainly.com/question/30827606
#SPJ4
the hardware implementation of a program uses three different classes of instructions: 4 of class a, 2 of class b, and 3 of class c, that require 1, 1.5, and 2 cycles, respectively (table below). this program is run on processor cpu a which has a clock rate 4.8 ghz and processor cpu b that is 25% slower than cpu a. what is the cpi (cycles per instruction) for the program? what is the execution time for the program on cpu a? what is the clock cycle time of cpu b?
Answers
Cycle count for the first code is equal to (10 cycles)(2 × 1)+(1 × 2)+(2 × 3) Number of cycles for second code = ((4 × 1) + ((1 × 2) + ((1 × 3)) = 9 cycles 10/9=1.11 times CPI for the first code, which is 10/5=2. CPI for the second code is 9 / 6 = 1.5.
What are the 3 things the CPU does to instructions?Processor operations include fetch, decode, execute, and write back. These are the four main tasks that a processor performs. Getting instructions from programme memory via a system's RAM is known as fetching.
The P1 processor runs at 3 GHz and has a 1.5 CPI. P2 has a CPI of 1.0 and a 2.5 GHz clock rate. P3 has a CPI of 2.2 and a 4.0 GHz clock rate. In comparison to the M1, the M2 offers 18% more multicore CPU performance, up to two additional GPU cores, a 50% increase in memory bandwidth, 25% more graphics performance at the same power level as M1 and up to 35% more performance at its maximum, a 25% increase in transistor count, and 2.3x faster performance at the same power.
To learn more about programming refer to :
https://brainly.com/question/30297247
#SPJ4
samuel wanted to paste the value and the formula attached from cell B6 to cell F16
Answers
Answer:
See Explanation
Explanation:
Given
Source: B6
Location: F16
I'll list two methods which Samuel can use to achieve his goal
Take for instance, the formula in cell B6 is =SUM(B1:B5)
This style of referencing is called relative cell referencing
If Samuel copies and the pastes the formula like this =SUM(B1:B5), the cell name will be changed in the destination cell; meaning that he wont be able to retain the formula and value.
Method 1: Using Absolute Cell Reference
Sam will have to alter the formula in cell B6 to =SUM($B$1:$B$5)
With this, he has switched from relative reference to absolute reference;
Irrespective of the location Sam wants to paste the formula (as long as the formula is in the same work book), the formula and the value won't change.
So, the formula will still maintain its original text and value, when pasted in cell F16
Method 2: Move The Formula
Alternatively, Sam can move the formula from cell B6 to cell F16.
This can be achieved by
1. Select cell B6
2. Click on Cut on the home tab (or press Ctrl + X)
3. Select cell F16
4. Click on Paste on the home tab (or press Ctrl + V)
Answer:
B
C
E
Edgenuity
Explain two ways by which the calendar meets or fails to meet the criteria of showing the correct data

Answers
Answer:
The two ways the calendar meets the criteria of showing the correct date are;
1) The calendar can give dates in the 12 months in a year
2) The calendar can show up to the 31 different days in a month
Explanation:
The two ways in which the calendar meets the criteria of showing the correct date are;
1) The number number of long blocks with 4 different months each = Three
Therefore, the total number of months the blocks can hold = 3 × 4 months = 12 months = The number of months in a year
2) The number of faces on each dice = 6 faces
The number of dice = 2 dice
The total number of faces = 12
The number of identical faces = 2 (11th and 22nd of the month)
The number of unique faces = 10
The number of combinations of the dices = ₁₀C₂ = 45
The number of combination of faces required to show = 1 to 31 = 31 combination
Therefore, there are adequate combinations on the dice to show all the dates of month
Page orientation is determined in Microsoft Word from the __________ tab
Answers
Answer:
Page orientation is determined in Microsoft Word from the Page Layout tab.
Explanation:
The Page Layout Tab holds all the options that allow you to arrange your document pages just the way you want them. You can set margins, apply themes, control of page orientation and size, add sections and line breaks, display line numbers, and set paragraph indentation and lines.
What do you understand by memory word?
Answers
Answer:
Explanation:
a 5-bit memory in which the individual memory bits are content5_4 , content5_3 , content5_2 , content5_1 , and content5_0
Your knowledge of algorithms helps you obtain an exciting job with the Acme Computer Company, along with a $10,000 signing bonus. You decide to invest this money with the goal of maximizing your return at the end of 10 years. You decide to use the Amalgamated Investment Company to manage your investments. Amalgamated Investments requires you to observe the following rules. It offers n different investments, numbered 1 through n. In each year j , investment i provides a return rate of rij . In other words, if you invest d dollars in investment i in year j , then at the end of year j, you have drij dollars. The return rates are guaranteed, that is, you are given all the return rates for the next 10 years for each investment. You make investment decisions only once per year. At the end of each year, you can leave the money made in the previous year in the same investments, or you can shift money to other investments, by either shifting money between existing investments or moving money to a new investement. If you do not move your money between two consecutive years, you pay a fee of f1 dollars, whereas if you switch your money, you pay a fee of f2 dollars, where f2 > f1.
a) The problem, as stated, allows you to invest your money in multiple investments in each year. Prove that there exists an optimal investment strategy that, in each year, puts all the money into a single investment. (Recall that an optimal investment strategy maximizes the amount of money after 10 years and is not concerned with any other objectives, such as minimizing risk.)
b) Prove that the problem of planning your optimal investment strategy exhibits optimal substructure.
c) Design an algorithm that plans your optimal investment strategy. What is the running time of your algorithm?
d) Suppose that Amalgamated Investments imposed the additional restriction that, at any point, you can have no more than $15,000 in any one investment. Show that the problem of maximizing your income at the end of 10 years no longer exhibits optimal substructure.
Answers
Answer:
C
Explanation:
You are part of a penetration testing team hired to test an organization's network security. The first phase of the test involves reconnaissance to discover which network services might be exposed to the Internet. Which tool should be used to complete this phase as quickly as possible
Answers
There are different phase of the test that involves reconnaissance The tool that should be used to complete this phase as quickly as possible is Port Scanner.
What is a reconnaissance phase? Reconnaissance is simply referred to as a preparatory phase. This is the phase where an hacker collect different information about a target before they launch an attack and is said to be completed in phases before they exploit the system vulnerabilities.The first phases of Reconnaissance is called dumpster diving. A port scan is a known to be a technique that hackers use to show or known the open doors or weak points in a network.
Learn more about Scanner from
https://brainly.com/question/10097616
wyd...tmr no school so happy(:
Answers
Answer:
Just writing, there's no school today either, well at least for me
Explanation:
You're welcome.
Answer: Nothing much, probably just homework and softball practice. I was also off today because of the snow.
Explanation: Have a good day!
Coyne, W. (2007). Creating our own happiness.This I Believe.
/
(1) indicate the core value(s) that the author presents in the
essay (2) discuss why you find your ch
Answers
The core value presented by the author in the essay "Creating our own happiness" is the belief that individuals have the power to create their own happiness.
In the essay, Coyne emphasizes the importance of personal agency and the ability to choose one's own mindset and perspective. The author argues that external circumstances and events do not determine our happiness; rather, it is our own attitude and approach towards life that shape our level of happiness. Coyne suggests that by cultivating positive thoughts, focusing on gratitude, and actively engaging in activities that bring joy, individuals can create their own happiness regardless of their circumstances.
I find this belief compelling because it empowers individuals to take control of their emotional well-being and find happiness within themselves. It highlights the importance of personal responsibility and resilience in navigating life's challenges. By recognizing that happiness is not solely dependent on external factors, but rather on our own choices and mindset, we can strive to cultivate a positive and fulfilling life. This perspective encourages us to actively seek out activities and relationships that bring us joy and fulfillment, leading to a more meaningful and satisfying existence.
Learn more about core value
brainly.com/question/30639813
#SPJ11
Seneca has just applied conditional formatting and realizes that she has made a mistake. Which action should she take to fix the mistake?
A) Clear the rule she created by going to the Conditional Formatting Rules Manager dialog box and deleting the rule.
B) Clear all rules that have been applied to the worksheet or selected range by clicking the Clear Rules button.
C) Use the Undo button or Ctrl+Z.
D) Right-click the area where the conditional formatting rule has been applied, and select Clear Rule from the menu list.
Answers
Answer:
its b
Explanation:
on edg
Answer:
b
Explanation:
What is the main function of a file extension?
O to allow the file to be extended to new uses
O to indicate which version of the file it is
O to indicate how much space the file takes up
O to indicate which program is needed to open it
Answers
To indicate which program is needed to open it
11.
Mona is confused about finite loop and infinite loop, explain her with the help of
example.
Answers
Answer:
The basic difference between finite and infinite is the number of times it runs and ends. The loop is basically a set of instructions that keeps repeating itself.
The finite loop ends after running for a finite times. This body of finite loop will stop executing after certain condition is reached. Hence the finite loop body keeps executing itself finite number of times.
An infinite loop keeps running and repeating itself endlessly.This loop never ends. This loop can be the result of an error in a program. For example when no stopping or exit condition is specified in the program.
Explanation:
Example of finite loop:
Lets take for loop as an example:
for(int i =0; i<=5; i++)
{ cout<<i<<endl; }
Now the loop starts from i=0
Next it enters the body of loop to execute the statement: cout<<i; which means that the value of i is displayed on the output screen.
This loop keeps executing until the value of i exceeds 5.
At first iteration 0 is printed on the output screen, at second iteration 1, at third iteration 2, at fourth iteration 3, fifth iteration 4, sixth iteration 5. After each of these iterations, the value of i is incremented by 1.
When 5 is printed, then at the next iteration the specified condition i.e. i<=5 gets false as the value of i now becomes 6 after incremented by 1.
So the loop stops running. So this means that loop ran for finite times and stopped after the a certain condition is reached. The output is:
0
1
2
3
4
5
Example of infinite loop:
Lets take while loop:
int i = 6;
while (i >=5)
{ cout<< i;
i++; }
In the above example, the loop will run infinite times. Here the value of i is initialized to 6. Then while loop is used which checks the condition which is the value of i is greater than or equal to 5. If the condition is true, the body of the loop starts executing which prints the value of i. Lets see what happens at each iteration:
1st iteration: i>=5 is True because i=6 and 6 is greater than 5. The program control enters the body of loop. The statement cout<<i prints 6. Next the value of i is incremented by 1 and it becomes 7.
2nd iteration: i>=5 is True because i=7 and 7 is greater than 5. The program control enters the body of loop. The statement cout<<i prints 7. Next the value of i is incremented by 1 and it becomes 8.
This loop will repeat itself infinite times and never stops as i will always have value greater than 5. So this is the example of infinite loop.
When a condition constantly evaluates to true, the loop control does not travel outside of that loop, resulting in an infinite loop.
Infinite loop and example:When a condition never turns false, the program enters a loop, which keeps repeating the same block of code over and over, with no end in sight.
An endless loop is demonstrated in the following example: b = input("what's your name?") while a==1 ", Welcome to Intellipaat!" print("Hi", b, ",
Find out more information about 'Loop'.
https://brainly.com/question/2081668?referrer=searchResults
River designs a program that will make a cartoon baby jump up and down. But when it is run, the baby appears but doesn’t move. What should River do?
a create a Boolean question
b move code to the editor
c run the program
d check for bugs
Answers
Which of the following is a small file that is placed on the computer hard drive of visitors to an organization's site?
a. a cookie
b. a wiki
c. an antivirus
d. a bookmark
Answers
The option which is a small file that is placed on the computer hard drive of visitors to an organization's site is called "Cookie" Opton A)
How does a cookie work ?A cookie is a small file that is placed on a visitor's computer hard drive when they access a website.
It is used to store information about the visitor's interactions with the websiteand can be accessed by the website during subsequent visits.
Users can choose to accept or reject cookies,delete existing cookies, or configure their browser to prompt for cookie acceptance on each website visit.
Learn more about Cookie at:
https://brainly.com/question/14252552
#SPJ1
True/false: A class might be thought of as a 'blueprint' that an object may be created from.
Answers
is an impact printer makes contact with the paper.
Answers
Answer:
Yes
Explanation:
because the name impact
Terrance is looking for a storage device to be used for backup storage. The device has to have a large storage capacity and be portable. What is the best device for Terrance's needs?
External hard drive
Disk drive
Hard drive
USB flash drive
Answers
Answer:
its external hard drive and flash drive
Your welcome
Explanation:
A data unit created at the transport layer by UDP is a _____.
A. segment
B. packet
C. datagram
D. frame
Answers
Answer:
A datagram
Explanation:
Protocol data units for the Internet protocol suite are: The transport layer PDU is the TCP segment for TCP, and the datagram for UDP. The Internet layer PDU is the packet.
Answer:
I think it's Datagrame
Explanation:
Why should you use a server provider instead of a personal server?
Answers
One should use a service provider rather than a personal server because Dedicated Servers services may provide the power and control you need for network administration while also keeping your network secure and saving you time and money. You may designate servers to accomplish tasks such as maintaining several websites or coordinating all of your company's printing.
What is a dedicated Server?A dedicated hosting service, also known as a dedicated server or managed hosting service, is a form of Internet hosting in which the client rents a whole server that is not shared with anybody else.
If your website is having difficulty keeping up with increased traffic, it may be time to convert it to a dedicated server. This is essentially a server that exclusively hosts your site, and it may not only increase the speed of your site, but also improve page loading times and help you optimize security.
Learn more servers:
https://brainly.com/question/28320301
#SPJ1
4
Select the correct answer.
Jason is working on a video image. He wants to add a small blur effect in a part of the video, but does not want to damage the video content
Which image-editing tool should he use?
ОА.
Dodge Tool
OB.
Pen Tool
OC.
Shape Layer
OD.
Smart Object
Reset
Next
Answers
Answer:
the answer is D Smart Object
Answer:
I think he should use a pen tool