Which of the following is not a valid variable name declaration? A. int __a3; B. int __3a; C. int __A3;
Answers
The following is not a valid variable name declaration: int __3a.
This is option B.
There are certain rules for naming a variable in Java. These are as follows:
Rules for Naming Variables in Java
Variables can be any length, but there are a few things to keep in mind when naming them in Java.
Here are some rules to follow:
1. Variable names must start with a letter or underscore.
2. Variable names should be meaningful and descriptive.
3. Variable names can include letters, numbers, and underscores.
4. Variable names should not contain spaces or special characters.
5. Variable names are case-sensitive.
For example, myVar and Myvar are not the same.In the declaration of variables, certain rules must be followed:Variable names must start with a letter or underscore (_). After that, any combination of letters, numbers, or underscores can be used, but the first character must be a letter or underscore.
Hence, the answer of the question is B.
Learn more about variable name at:
https://brainly.com/question/30842490
#SPJ11
Related Questions
help me please help help

Answers
Answer:
C
Explanation:
The concept of superheros
Answer: C.
Explanation:
cause that concept is oooooooooooooooooooooooooooooold
How do you create a variable with the numeric value 5?
Answers
Answer:
They are declared simply by writing a whole number. For example, the statement x = 5 will store the integer number 5 in the variable x.
1.03!! need major help!!
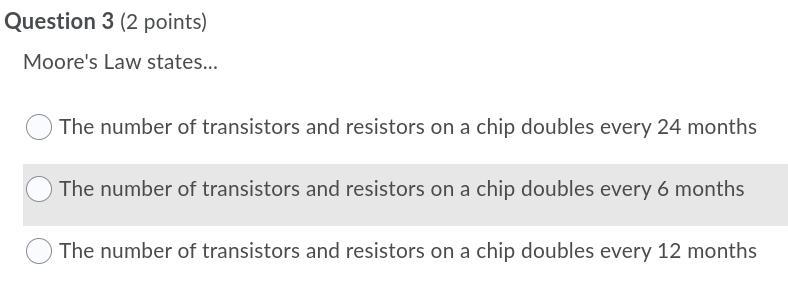
Answers
Answer: the answer is A
Explanation:
Moore's law, prediction made by American engineer Gordon Moore in 1965 that the number of transistors per silicon chip doubles every year. ... Moore observed that the number of transistors on a computer chip was doubling about every 18–24 months.
time-dependent malware that can come in different forms. its main characteristic is that it’s activated when a particular event occurs
Answers
The time-dependent malware that can come in different forms and is activated when a particular event occurs is known as trigger-based malware.
Trigger-based malware is designed to remain dormant until a specific event or condition is met. This event or condition, known as the trigger, serves as a signal for the malware to activate and carry out its malicious actions. The trigger can be based on various factors, such as a specific date and time, the occurrence of a particular user action, the presence or absence of certain files, network connectivity, or other environmental variables.
By remaining inactive until triggered, this type of malware can evade detection and mitigation efforts. Once the trigger event occurs, the malware may execute a range of malicious activities, such as data theft, system damage, unauthorized access, or propagation to other systems.
To protect against trigger-based malware, robust security measures, including up-to-date antivirus software, intrusion detection systems, regular system updates, and user awareness, are crucial. Prompt detection and response to trigger events can help mitigate the potential impact of such malware.
To know more about malware
brainly.com/question/29756995
#SPJ11
What is the significance of text selection
Answers
Answer:
Sorry about the other guy
Explanation:
The importance of text selection is that it makes your document or presentation more interesting or appealing (is what i found on google)
any one know how to fix forzas camera bc it shutters to much



Answers
Answer:
LEDs are powered by alternating current AC.
Explanation:
The electricity will move in and out of cycles.
When the FPS won't math it'll flicker. Try switching to your camera's shutter speed instead. ( May be times your camera won't support it.)
Which organization provides a free, online html5 validator application to ensure that a webpage's html tags follow the rules for html5?
Answers
The organization provides a free, online html5 validator application to ensure that a webpage's html tags follow the rules for html5 is the W3C.
What does the W3C do?The W3C's is known to help to create protocols and rules that makes sure that long-term development of the Web.
Therefore, we can say that The organization provides a free, online html5 validator application to ensure that a webpage's html tags follow the rules for html5 is the W3C.
Learn more about The W3C from
https://brainly.com/question/11179793
#SPJ1
Digital and analog audio recordings have pros and cons. Do you think the pros of digital recordings outweigh the cons and therefore prefer digital audio recordings? Or, do you think the cons outweigh the pros and therefore you prefer analog audio recordings? Explain.
Answers
Digital vs Analog Audio is completely personal preference and there is no clear winner on which is better.
But there are some pros and cons about both, Analog sometimes distorts when playing and can be easily scratched and ruins the grooves. Analog is believed to be the true representation of the sound when it was recorded. Digital is not the actual recording of the sound, it's actually a combination of binary code. It is also sometimes mixed or remastered in Digital and sounds a bit different to make it sound better. It also depends on the system you are listening it from. You could have a horrible Digital system its playing through and an amazing Analog system playing, of course the Analog system will sound better in that case. Some believe that Digital is on par to overtake Analog in the "true picture of sound" category but some also say Analog will forever be the best at playing sound and Digital will always be the alternative.
But, in the end it's all personal preference and the pros and cons don't overweigh to make one better than the other.
When downloading a large file from the iniernet Alexis interrupted the download by closing ber computer, Later that evening she resumed tbe download and noticed that the file was bowniosding at a constant rate of change. 3 minutes since resaming the download 7440 total MegaBytes (MB) of the file had been downloaded and 6 mintues siace resuming the download 13920 total MesaBytes (MB) of the file had been donstoaded A. From 3 to 6 minutes after she resumed downlooding, how many minutcs elapod? misules b. From 3 to 6 minutes after she resumed downloading, how many total MB of the file were dowaloaded? MB c. What is the consuant rate at which the file downloads? MegaByes per minule d. If the file continues downloadisg for an additional 1.5 minner (after tbe 6 mimutes afts she feramed downloading). 4. How many aditipeal MB of the flie were downloaded? MIB 14. What is the new total number of MB of the file Bhat have been downloaded? MEI
Answers
a) From 3 to 6 minutes after resuming the download, 3 minutes elapsed.
b) From 3 to 6 minutes after resuming the download, 6,480 MB of the file were downloaded.
c) The constant rate at which the file downloads is 2,160 MB per minute.
d) If the file continues downloading for an additional 1.5 minutes, an additional 3,240 MB of the file will be downloaded.
e) The new total number of MB of the file that have been downloaded will be 17,160 MB.
a) From the given information, we can determine the time elapsed by subtracting the starting time (3 minutes) from the ending time (6 minutes), resulting in 3 minutes.
b) To calculate the total MB downloaded, we subtract the initial downloaded amount (7,440 MB) from the final downloaded amount (13,920 MB). Therefore, 13,920 MB - 7,440 MB = 6,480 MB were downloaded from 3 to 6 minutes after resuming the download.
c) The constant rate at which the file downloads can be found by dividing the total MB downloaded (6,480 MB) by the elapsed time (3 minutes). Therefore, 6,480 MB / 3 minutes = 2,160 MB per minute.
d) If the file continues downloading for an additional 1.5 minutes, we can calculate the additional MB downloaded by multiplying the constant rate of download (2,160 MB per minute) by the additional time (1.5 minutes). Hence, 2,160 MB per minute * 1.5 minutes = 3,240 MB.
e) The new total number of MB of the file that have been downloaded can be found by adding the initial downloaded amount (7,440 MB), the MB downloaded from 3 to 6 minutes (6,480 MB), and the additional MB downloaded (3,240 MB). Thus, 7,440 MB + 6,480 MB + 3,240 MB = 17,160 MB.
In summary, Alexis resumed the download and observed a constant rate of download. By analyzing the given information, we determined the time elapsed, the total MB downloaded, the rate of download, the additional MB downloaded, and the new total number of MB downloaded. These calculations provide a clear understanding of the file download progress.
Learn more about constant rate
brainly.com/question/32636092
#SPJ11
You have an azure subscription that contains a user named user1, a resource group named rg1, and a virtual machine named vm1. You enable a system-assigned managed identity for vm1. To which identities can you assign the reports reader role?.
Answers
To assign the Reports Reader role to user1, you would need to assign the role to the user's managed identity. To do this, you would need to navigate to the Access control (IAM) blade of the resource group rg1 and then use the Add role assignment option to assign the Reports Reader role to the user's managed identity.
You can also assign the Reports Reader role to the system-assigned managed identity of vm1. To do this, you would need to navigate to the Access control (IAM) blade of the virtual machine vm1 and then use the Add role assignment option to assign the Reports Reader role to the system-assigned managed identity of vm1.
Learn more about Access control (IAM)
https://brainly.com/question/28810148
#SPJ4
Need help with these

Answers
Answer:
1. D
2. B
3. D
Explanation:
vnasgbaenVmad7kDg Zg
Alpha Technologies, a newly established company, wants to share information about its work with people all over the world. Which type of server should this company use to upload their information?
Answers
This answer from the pro IdowShadow
Option A, Web Server, because it is a type of HTTP server used to direct web pages and blogs, as a method of transmitting information through a web platform for personal or business use, to publicize a business or an organization.
A discovery schedule with a shazzam batch size of 5000 contains a /24 subnet ip range. A shazzam probe during discovery ______
Answers
A discovery schedule with a shazzam batch size of 5000 contains a /24 subnet ip range. A shazzam probe during discovery will be launched 1 time.
What will be searched during the discovery run will depend on the discovery timetable. We benefit from the discovery timetable in the following ways: identification of devices based on IP addresses. defining the use of credentials for device probes.
Plan a weekly or monthly exploration. Set up discovery to happen at predetermined intervals, like every 48 hours.
IP discovery is the process of looking for IP devices on your network using one or more techniques, such as SNMP, ICMP, or neighbourhood scanning.
For the first time, download an application from the ServiceNow Store. Get access to a product or application for security operations. A ServiceNow Store application must be activated.
Construct an integration for Security Operations.
Learn more about subnet ip range:
https://brainly.com/question/12976384
#SPJ4
Python projectstem 3.6 code practice
Write a program to input 6 numbers. After each number is input, print the smallest of the numbers entered so far.
Sample Run
Enter a number: 9
Smallest: 9
Enter a number: 4
Smallest: 4
Enter a number: 10
Smallest: 4
Enter a number: 5
Smallest: 4
Enter a number: 3
Smallest: 3
Enter a number: 6
Smallest: 3
Answers
Answer:
python
Explanation:
list_of_numbers = []
count = 0
while count < 6:
added_number = int(input("Enter a number: "))
list_of_numbers.append(added_number)
list_of_numbers.sort()
print(f"Smallest: {list_of_numbers[0]}")
count += 1
compare mini and mainframe computer in terms of speed,memory and storage
Answers
Answer:
Mainframe computers have large memory storage. While minicomputers have small or less memory storage than mainframe computer. ... The processing speed of mainframe computer is faster than minicomputer. While the processing speed of minicomputer is slower than mainframe computer
Explanation:
[10] what is the primary benefit of making a computing system fault-tolerant?
Answers
The primary benefit of making a computing system fault-tolerant is to increase the system's reliability and availability, by reducing the risk of system failure due to hardware or software faults.
Fault tolerance is the ability of a system to continue operating in the event of a fault, such as a hardware failure, power outage, or software error.
By designing a computing system to be fault-tolerant, the system can continue to provide essential services even when one or more components fail, without causing significant downtime or data loss.
Some of the key benefits of making a computing system fault-tolerant include:
Increased reliabilityImproved availabilityBetter data protectionIncreased scalabilityLearn more about fault tolerance here:
https://brainly.com/question/29484867
#SPJ11
freeze panes so rows 1:8 and columns a:b remain in place when you scroll through the worksheets
Answers
Instead of freezing the full range, you can choose to freeze just a certain row or column. Simply choose the cell beneath the frozen row or the cell to the right of the frozen column.
What do Excel frozen panes mean?Button of Magical Freeze. By using the Excel Freeze Panes option, you can prevent your columns and/or rows from moving when you scroll across or down to see the rest of your page.
What do you mean when you say the spreadsheet has frozen?In Excel, we can freeze a specific row or column to prevent modifications to that row or column. Simply put, while we keep switching the row.
To know more about column visit:-
https://brainly.com/question/13602816
#SPJ1
for the hdtv program in figure 3-3, which of the speeds shown will allow real-time streaming?
Answers
for real-time streaming of HDTV content. Streaming high-definition television (HDTV) content typically requires a stable and sufficient internet connection speed. The recommended minimum speed.
for streaming HDTV content in real-time is typically around 5 Mbps (megabits per second) or higher.
To ensure a smooth streaming experience without buffering or interruptions, higher speeds are often preferred. Depending on the streaming platform or service, higher quality settings or 4K streaming may require even faster speeds, typically ranging from 15 Mbps to 25 Mbps or more.
It is important to note that the specific speed requirements for real-time streaming can vary based on factors such as the streaming platform, the quality settings, the compression used, and the availability of bandwidth. It is always advisable to check the recommended speed requirements provided by the streaming service or consult their support documentation for accurate and up-to-date information.
Learn more about HDTV here:
https://brainly.com/question/29096596
#SPJ11
A machine is having issues, so the user is responsible for getting the machine serviced. Which stage of the hardware lifecycle does this scenario belong to
Answers
Answer:
Maintenance, is the right answer.
Explanation:
A stage where the hardware of a machine is replaced due to some issues which make the machine work inappropriately is called the maintenance stage of the hardware. In this phase, some modifications are made in the hardware to support the operational effectiveness of the hardware. The customer executives try to improve the performance of the system and provide better security during replacing the hardware.
Select the correct answer.
What needs to be defined throughout an animation sequence to define the start and end points of motion?
A frames
B. characters
C. key frames
D. movement
Answers
You have just purchased a motherboard that has an LGA 1156 socket for an Intel Pentium processor. What type of memory modules will you most likely need for this motherboard? A. DIP B. SIMM C. DIMM D. SODIMM
Answers
Answer:
The answer is "Option C"
Explanation:
The term DIMM stands for the Dual In-Line Memory Module, which is a kind of memory, that is used in computers. It is a small board of flash memory that uses the 64-bit memory bus because the SIMM has only a 32-bit path. It enables DIMMs to simultaneously transfer more information, and the wrong choices can be defined as follows:
In choice A, It is used in sockets, that's why it is wrong. In choice B, It is wrong because it is used in 32 bits only. In choice D, It is wrong because it is used in the expansion of memory.The name of an image (or file) can be found on the image
in the document window.
tab
panel
options
menu
Answers
Answer:
tab
Explanation:
Question 1:
Define what they do?
Command + B
Command + D
Command G
Question 2:
Select any of the five tools from the toolbar in adobe illustrator.
Explain what the do..
Answers
Answer 1:
Command + B: In Adobe Illustrator, Command + B is a keyboard shortcut used to apply bold formatting to selected text.
Command + D: In Adobe Illustrator, Command + D is a keyboard shortcut used to repeat the last action or command. This can be useful for quickly duplicating elements or repeating a complex series of steps.
Command + G: In Adobe Illustrator, Command + G is a keyboard shortcut used to group selected objects together. Grouping objects allows you to treat them as a single object, making it easier to move, rotate, or manipulate them as a unit.
What is Answer 2?One of the five tools from the toolbar in Adobe Illustrator is the Selection tool. The Selection tool is used to select, move, and manipulate objects within the document. It is represented by the black arrow icon in the toolbar.
Therefore, When an object is selected with the Selection tool, you can perform actions such as moving, resizing, rotating, or modifying the shape or appearance of the object. The Selection tool is a basic and essential tool for working in Adobe Illustrator, and is used frequently throughout the design process.
Learn more about adobe illustrator at:
https://brainly.com/question/15169412
#SPJ1
T/F By default margins are set to Narrow Margins.
True
O False
Answers
By default margins are set to Narrow Margins is false.
What are margins in writing?It is not necessarily true that margins are set to narrow by default in all software or applications. The default margin settings can vary depending on the specific software or application being used, as well as the user's preferences and settings.
In some cases, the default margin setting may be narrow, while in other cases it may be wider. It is generally a good idea to check the margin settings in the software or application that you are using to ensure that they are set to your desired width. If you need to change the margin settings, you can usually do so by accessing the "Page Setup" or "Print" options in the software or application's menu.
Learn more about margins from
https://brainly.com/question/28579662
#SPJ1
What are the motivating factors behind the development of computers?
Answers
There were several motivating factors behind the development of computers, including:
1. Automation: Computers were developed to automate repetitive and time-consuming tasks. This would help businesses and individuals become more efficient and productive.
2. Scientific Research: Scientists needed tools to process large amounts of data that they could not handle manually.
3. Military: During World War II, computers were developed to help the military calculate the trajectories of missiles and bombs.
4. Communication: Computers were designed to help people communicate more efficiently, allowing them to send messages, share information and collaborate on projects.
5. Entertainment: Computers were built to create and support new forms of entertainment like video games, music, and movies.
6. Education: Computers could offer new ways of educating people, with more interactive and engaging materials to help students learn.
7. Data storage: One of the primary motivations behind computer development was to create a system that could store, process, and retrieve data more efficiently than traditional paper-based systems.
who invited talbulating machine
Answers
Answer:
Herman Hollerith
brainliest please?
Explanation:
Herman Hollerith was an American businessman, inventor, and statistician who developed an electromechanical tabulating machine for punched cards to assist in summarizing information and, later, in accounting
Answer:
HERMAN HOLLERITH
(born February 29, 1860, Buffalo, New York, U.S.—died November 17, 1929, Washington, D.C.)
American inventor of a tabulating machine that was an important precursor of the electronic computer.
During the 1880s the engineer Herman Hollerith devised a set of machines for compiling data from the United States Census called as the talbulating machine
Explanation:
brainliest plz
Explain why E-mail A is inappropriate for the workplace and revise it to be appropriate.
Answers
Email A Is Not Appropriate Because The Email Dosent Sound Professional At All Or Respectful At All
Explanation:
This is the revised Email Appropriate For Workplace
Is it possible that I will be receiving the training manual this morning because I will be needing it for my next shift.
inappropriate--workplace email uses include messages linked to social networking sites or emails involving an employee's sideline business.
Hope this Helps you!!
here have a good day
Answers
i am a protocol that uses encryption to perform security-related functions. i regulate privacy and security between network nodes. what protocol am i?
Answers
You are most likely the Transport Layer Security (TLS) protocol, which uses encryption to provide secure communication and privacy between network nodes.
You are likely referring to the Transport Layer Security (TLS) protocol. It is a cryptographic protocol that provides secure communication between network nodes over the internet. TLS encrypts data to protect against eavesdropping, tampering, and forgery, and authenticates the communication endpoints to ensure their identities. It operates at the transport layer of the OSI model, establishing a secure session between two applications by negotiating a set of cryptographic algorithms and exchanging digital certificates. TLS is widely used in web browsers, email systems, and other applications that require secure communication over the internet.
Learn more about Transport Layer Security (TLS) protocol here:
https://brainly.com/question/11141957
#SPJ11
If you wanted a smartphone with the fewest restrictions on application development which smartphone operating system should you choose
Answers
Answer:
Apple iOS
Explanation:
A software can be defined as a set of executable instructions (codes) or collection of data that is used typically to instruct a computer on how to perform a specific task and solve a particular problem.
Basically, softwares are categorized into two (2) main categories and these are;
I. Proprietary software: it's also known as a closed-source software and it can be defined as any software application or program that has its source code copyrighted and as such cannot be used, modified or distributed without authorization from the software developer.
II. Open-source software: it's a type of software in which end users are granted the permission to use, study, modify, copy and share the software with its source code anyhow.
An Apple iOS is an example of an operating system that has the open-source software features and as such its users are faced with minimal restrictions on application development.
This ultimately implies that, if you wanted a smartphone with the fewest restrictions on application development the smartphone operating system you should choose is Apple iOS.