Your game design company has recently asked all employees to use a specific personal information management application (PIM) to increase workplace efficiency. The PIM is collaborative, so contacts, calendar entries, and notes are shared across the team. Several team members are resistant to the idea, saying it interrupts their workflow, and they prefer their own way of handing contacts, notes, etc. Others don’t want their own notes to be seen by their coworkers.
Answers
Answer:For example, an office worker might manage physical documents in a filing cabinet by placing them in folders organized alphabetically by project name, or might manage digital documents in folders in a hierarchical file system.
Explanation:
Related Questions
Kaley took a bunch of pictures at her birthday party last week. She wants to share them with her friends. Which of the following choices is a low risk way to do so?
Answers
What's the biggest challengeWeb analytics can tell you many things about your online performance, but what can analytics tools not tell you?
A
What your customers are doing on your website
B
Where your customers have come from before visiting your website
C
Where your customers go after leaving your website
D
What your customers are looking for on your website for most businesses when going online?
Answers
Answer:
(C) Where your customers go after leaving your website
How To Approach Data Center And Server Room Installation?
Answers
Answer:
SEE BELOW AND GIVE ME BRAINLEST
Explanation:
Make a plan for your space: Determine how much space you will require and how it will be used. Consider power requirements, cooling requirements, and potential growth.
Choose your equipment: Based on your unique requirements, select the appropriate servers, storage devices, switches, routers, and other equipment.
Create your layout: Determine the room layout, including rack placement, cabling, and power distribution.
Set up your equipment: Install the servers, storage devices, switches, and other equipment as planned.
Connect your equipment: Connect and configure your servers and other network devices.
Check your systems: Check your equipment to ensure that everything is operating properly.
Maintain and monitor: To ensure maximum performance, always check your systems for problems and perform routine maintenance.
An app developer is shopping for a cloud service that will allow him to build code, store information in a database and serve his application from a single place. What type of cloud service is he looking for?
Answers
Answer:
Platform as a Service (PaaS).
Explanation:
In this scenario, an app developer is shopping for a cloud service that will allow him to build code, store information in a database and serve his application from a single place. The type of cloud service he is looking for is a platform as a service (PaaS).
In Computer science, Platform as a Service (PaaS) refers to a type of cloud computing model in which a service provider makes available a platform that allow users (software developers) to build code (develop), run, store information in a database and manage applications over the internet.
The main purpose of a Platform as a Service (PaaS) is to provide an enabling environment for software developers to code without having to build and maintain complex infrastructure needed for the development, storage and launching of their software applications.
Simply stated, PaaS makes provision for all of the software and hardware tools required for all the stages associated with application development over the internet (web browser).
Hence, the advantage of the Platform as a Service (PaaS) is that, it avails software developers with enough convenience as well as simplicity, service availability, ease of licensing and reduced costs for the development of software applications.
These are the different types of Platform as a Service;
1. Private PaaS.
2. Public PaaS.
3. Hybrid PaaS.
4. Mobile PaaS.
5. Communications PaaS.
6. Open PaaS.
The software developers can choose any of the aforementioned types of PaaS that is suitable, effective and efficient for their applications development. Some examples of PaaS providers are Google, Microsoft, IBM, Oracle etc.
Match the product to its function.
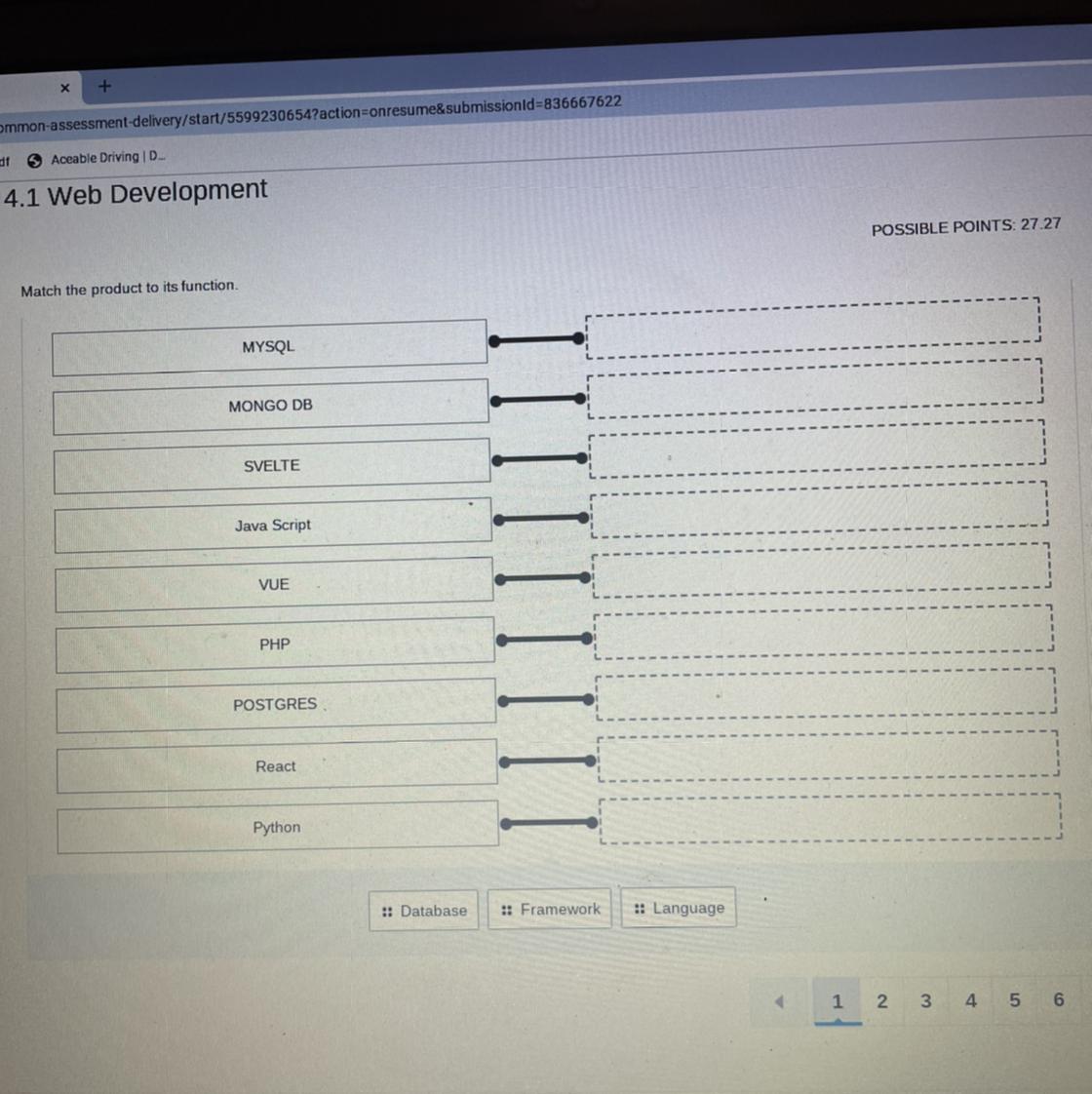
Answers
Answer:
MYSQL: Database
MONGO DB: Database
SVELTE: Framework
JS: Language
VUE: Framework
PHP: Language
POSTGRES: Database
React: Framework (a JS library actually)
Python: Language
can someone please give me the correct answer to this? 8.7.5 Calendar Codehs.
Answers
The calendar Codes is given as follows;
import calendar
# Prompt user for month and year
month = int(input("Enter month (1-12): "))
year = int(input("Enter year: "))
# Display calendar for the given month and year
print(calendar.month(year, month) )
How does this work ?The month ) function from the calendar module takes two arguments: the year and month to display the calendar for.
It returns a formatted string representing the calendar for that month, which is then printed to the console.
A formatted string literal, often known as an f-string, is a string literal that begins with 'f' or 'F' in programming.
Learn more about Codes at:
https://brainly.com/question/3042960
#SPJ1
Why is it important to know how to create a professional email?
Answers
So people think you are professional based on what you write.
Answer:
It is important to write a professional email because you need to make a good impression. This also shows that you are determined.
Module 7: Final Project Part II : Analyzing A Case
Case Facts:
Virginia Beach Police informed that Over 20 weapons stolen from a Virginia gun store. Federal agents have gotten involved in seeking the culprits who police say stole more than 20 firearms from a Norfolk Virginia gun shop this week. The U.S. Bureau of Alcohol, Tobacco, Firearms and Explosives is working with Virginia Beach police to locate the weapons, which included handguns and rifles. News outlets report they were stolen from a store called DOA Arms during a Tuesday morning burglary.
Based on the 'Probable Cause of affidavit' a search warrant was obtained to search the apartment occupied by Mr. John Doe and Mr. Don Joe at Manassas, Virginia. When the search warrant executed, it yielded miscellaneous items and a computer. The Special Agent conducting the investigation, seized the hard drive from the computer and sent to Forensics Lab for imaging.
You are to conduct a forensic examination of the image to determine if any relevant electronic files exist, that may help with the case. The examination process must preserve all evidence.
Your Job:
Forensic analysis of the image suspect_ImageLinks to an external site. which is handed over to you
The image file suspect_ImageLinks to an external site. ( Someone imaged the suspect drive like you did in the First part of Final Project )
MD5 Checksum : 10c466c021ce35f0ec05b3edd6ff014f
You have to think critically, and evaluate the merits of different possibilities applying your knowledge what you have learned so far. As you can see this assignment is about "investigating” a case. There is no right and wrong answer to this investigation. However, to assist you with the investigation some questions have been created for you to use as a guide while you create a complete expert witness report. Remember, you not only have to identify the evidence concerning the crime, but must tie the image back to the suspects showing that the image came from which computer. Please note: -there isn't any disc Encryption like BitLocker. You can safely assume that the Chain of custody were maintained.
There is a Discussion Board forum, I enjoy seeing students develop their skills in critical thinking and the expression of their own ideas. Feel free to discuss your thoughts without divulging your findings.
While you prepare your Expert Witness Report, trying to find answer to these questions may help you to lead to write a conclusive report : NOTE: Your report must be an expert witness report, and NOT just a list of answered questions)
In your report, you should try to find answer the following questions:
What is the first step you have taken to analyze the image
What did you find in the image:
What file system was installed on the hard drive, how many volume?
Which operating system was installed on the computer?
How many user accounts existed on the computer?
Which computer did this image come from? Any indicator that it's a VM?
What actions did you take to analyze the artifacts you have found in the image/computer? (While many files in computer are irrelevant to case, how did you search for an artifacts/interesting files in the huge pile of files?
Can you describe the backgrounds of the people who used the computer? For example, Internet surfing habits, potential employers, known associates, etc.
If there is any evidence related to the theft of gun? Why do you think so?
a. Possibly Who was involved? Where do they live?
b. Possible dates associated with the thefts?
Are there any files related to this crime or another potential crime? Why did you think they are potential artifacts? What type of files are those? Any hidden file? Any Hidden data?
Please help me by answering this question as soon as possible.
Answers
In the case above it is vital to meet with a professional in the field of digital forensics for a comprehensive analysis in the areas of:
Preliminary StepsImage Analysis:User Accounts and Computer Identification, etc.What is the Case Facts?First steps that need to be done at the beginning. One need to make sure the image file is safe by checking its code and confirming that nobody has changed it. Write down who has had control of the evidence to show that it is trustworthy and genuine.
Also, Investigate the picture file without changing anything using special investigation tools. Find out what type of system is used on the hard drive. Typical ways to store files are NTFS, FAT32 and exFAT.
Learn more about affidavit from
https://brainly.com/question/30833464
#SPJ1
I need help with Pearson Python coding Unit 8, Lesson 10 - the objectGame.py portfolio. I can't get the script to run properly even coping directly from the lesson.
Answers
Without more information about the specific error message and the context in which the code is being run, it is difficult to say for sure what the problem might be.
However, here are a few things that you can try to troubleshoot the issue:
Make sure that you have the correct version of Python installed on your computer. The script may be written in a version of Python that is not compatible with the version you have installed.Check for any syntax errors in your code. Make sure that all of the syntax is correct and that there are no missing or extra characters.Verify that you have all of the necessary libraries and modules imported at the beginning of your script. Make sure that you have imported the specific modules and libraries that are used in the script.What is Python coding?In regards to your coding issue, these also can help:
Make sure that you have saved the script with the correct file extension, such as .py, and that it is located in the correct directory.Try running the script in a different environment or editor, such as IDLE or Anaconda, to see if the problem is specific to the environment you are currently using.Make sure that you have the correct permissions to run the script.Check the script for any missing or misnamed variables that might cause errors.Check the script for any missing or misnamed functions that might cause errors.It's also helpful to have a look at the script and compare it to the one on the lesson, this way you can spot any differences and correct them accordingly.Therefore, If the problem persists, you may want to reach out to your instructor or seek help from a tutor for further assistance.
Learn more about Python coding from
https://brainly.com/question/26497128
#SPJ1
Write a program whose input is a character and a string, and whose output indicates the number of times the character appears in the string. The output should include the input character and use the plural form, n's, if the number of times the characters appears is not exactly 1.You may assume that the string does not contain spaces and will always contain less than 50 characters.
Ex: If the input is:
n Monday
the output is:
1 n
Ex: If the input is:
z TodayisMonday
the output is:
0 z's
Ex: If the input is:
n It'ssunnytoday
the output is:
2 n's
Case matters.
Ex: If the input is:
n Nobody
the output is:
0 n's
n is different than N.
C programming.
Answers
Answer:
The program and input is different than n, and it’s sunny today.
Data analytics benefits both financial services consumers and providers by helping create a more accurate picture of credit risk.
True
False
Answers
Answer:
True
Explanation:
Step 1: Configure the initial settings on R1. Note: If you have difficulty remembering the commands, refer to the content for this topic. The commands are the same as you configured on a switch. Open a configuration window a. Configure R1 as the hostname. b. Configure Message of the day text: Unauthorized
Answers
Answer:
The configuration of the R1 is as follows
Explanation:
Router>enable
Router#show running-config
Router#show startup-config
Router#configure terminal
Router(config)#hostname R1
R1(config)#line console 0
R1(config-line)#password letmein
R1(config-line)#login
R1(config-line)#exit
R1(config)#enable password cisco
R1(config)#enable secret itsasecret
R1(config)#service password-encryption
R1(config)#banner motd #Unauthorized access is strictly prohibited#
R1(config)#end
R1#exit
R1>enable
R1#copy running-config startup-config
R1#show flash
R1#copy startup-config flash
Use the drop-down menus to complete statements about how to use the database documenter
options for 2: Home crate external data database tools
options for 3: reports analyze relationships documentation
options for 5: end finish ok run

Answers
To use the database documenter, follow these steps -
2: Select "Database Tools" from the dropdown menu.3: Choose "Analyze" from the dropdown menu.5: Click on "OK" to run the documenter and generate the desired reports and documentation.How is this so?This is the suggested sequence of steps to use the database documenter based on the given options.
By selecting "Database Tools" (2), choosing "Analyze" (3), and clicking on "OK" (5), you can initiate the documenter and generate the desired reports and documentation. Following these steps will help you utilize the database documenter effectively and efficiently.
Learn more about database documenter at:
https://brainly.com/question/31450253
#SPJ1
One or more objects may be created from a(n):
Question 1 options:
A)
Class.
B)
Field.
C)
Instance.
D)
Method.
Answers
One or more objects may be created from a class in the object-oriented programming, according to the question.
What do you mean by object?
Objects are run-time produced instances of classes. They may be controlled and interacted with using the class's stated methods and attributes, and they each have their own distinct identity and state.
What is a class?
A class is a blueprint or template for constructing objects in object-oriented programming. The characteristics and actions of objects derived from a class are defined. We can use class to create one or more objects.
A class may be instantiated with the "new" operator to produce one or more objects. An instance of a class is any object produced from that class.
So, One or more objects may be created from a class in the object-oriented programming.
To know more about object-oriented programming, visit: brainly.com/question/28732193
#SPJ4
A backup operator wants to perform a backup to enhance the RTO and RPO in a highly time- and storage-efficient way that has no impact on production systems. Which of the following backup types should the operator use?
A. Tape
B. Full
C. Image
D. Snapshot
Answers
In this scenario, the backup operator should consider using the option D-"Snapshot" backup type.
A snapshot backup captures the state and data of a system or storage device at a specific point in time, without interrupting or impacting the production systems.
Snapshots are highly time- and storage-efficient because they only store the changes made since the last snapshot, rather than creating a complete copy of all data.
This significantly reduces the amount of storage space required and minimizes the backup window.
Moreover, snapshots provide an enhanced Recovery Time Objective (RTO) and Recovery Point Objective (RPO) as they can be quickly restored to the exact point in time when the snapshot was taken.
This allows for efficient recovery in case of data loss or system failure, ensuring minimal downtime and data loss.
Therefore, to achieve a highly time- and storage-efficient backup solution with no impact on production systems, the backup operator should utilize the "Snapshot" backup type.
For more questions on Recovery Time Objective, click on:
https://brainly.com/question/31844116
#SPJ8
2. Which is not part of the Sans Institutes Audit process?
Help to translate the business needs into technical or operational needs.
O Deler a report.
O Define the audit scope and limitations.
O Feedback based on the
Answers
Answer:
Help to translate the business needs into technical or operational needs. This is not a part.
Explanation:
Capital budgeting simply refers to the process that is used by a business in order to determine the fixed asset purchases that is proposed which it should accept, or not. It's typically done in order to select the investment that's most profitable for a company.
Some of the capital budgeting processes include:
Identification and analysis of potential capital investments.
Application of capital rationing
Performing post-audits
It should be noted that developing short-term operating strategies is not part of the capital budgeting process.
Learn more about investments on:
https://brainly.com/question/15105766
#SPJ2
Describe the series of connections that would be made, equipment and protocol changes, if you connected your laptop to a wireless hotspot and opened your email program and sent an email to someone. Think of all the layers and the round trip the information will likely make.
Answers
Answer:
Check Explanation.
Explanation:
Immediately there is a connection between your laptop and the wireless hotspot, data will be transferred via the Physical layer that will be used for encoding of the network and the modulation of the network and that layer is called the OSI MODEL.
Another Important layer is the APPLICATION LAYER in which its main aim and objectives is for support that is to say it is used in software supporting.
The next layer is the PRESENTATION LAYER which is used during the process of sending the e-mail. This layer is a very important layer because it helps to back up your data and it is also been used to make connections of sessions between servers of different computers
Referring to narrative section 6.4.1.1. "Orders Database" in your course's case narrative you will:
1. Utilizing Microsoft VISIO, you are to leverage the content within the prescribed narrative to develop an Entit
Relationship Diagram (ERD). Make use of the 'Crow's Foot Database Notation' template available within VISIC
1.1. You will be constructing the entities [Tables] found within the schemas associated with the first letter of
your last name.
Student Last Name
A-E
F-J
K-O
P-T
U-Z
1.2. Your ERD must include the following items:
All entities must be shown with their appropriate attributes and attribute values (variable type and
length where applicable)
All Primary keys and Foreign Keys must be properly marked
Differentiate between standard entities and intersection entities, utilize rounded corners on tables for
intersection tables
●
.
Schema
1 and 2 as identified in 6.4.1.1.
1 and 3 as identified in 6.4.1.1.
1 and 4 as identified in 6.4.1.1.
1 and 5 as identified in 6.4.1.1.
1 and 6 as identified in 6.4.1.1.
.
Answers
The following is a description of the entities and relationships in the ERD -
CustomersProductOrdersOrder Details How is this so?Customers is a standard entity that stores information about customers, such as their name, address,and phone number.Products is a standard entity that stores information about products, such as their name, description, and price.Orders is an intersection entity that stores information about orders, such as the customer who placed the order,the products that were ordered, andthe quantity of each product that was ordered.Order Details is an intersection entity that stores information about the details of each order,such as the order date, the shipping address, and the payment method.The relationships between the entities are as follows -
A Customer can place Orders.An Order can contain Products.A Product can be included inOrders.The primary keys and foreign keys are as follows -
The primary key for Customers is the Customer ID.The primary key for Products is the Product ID.The primary key for Orders is the Order ID.The foreign key for Orders is the Customer ID.The foreign key for Orders is theProduct ID.The foreign key for Order Details is the Order ID.The foreign key for Order Details is the Product IDLearn more about ERD at:
https://brainly.com/question/30391958
#SPJ1
Need an answer in Python
Write a program for. checking the truth of the statement ¬(X ⋁ Y ⋁ Z) = ¬X ⋀ ¬Y ⋀ ¬Z for all predicate values.
Answers
Using the knowledge in computational language in python it is possible to write a code that checking the truth of the statement ¬(X ⋁ Y ⋁ Z) = ¬X ⋀ ¬Y ⋀ ¬Z for all predicate values.
Writting the code:def conjunction(p, q):
return p and q
print("p q a")
for p in [True, False]:
for q in [True, False]:
a = conjunction(p, q)
print(p, q, a)
def exclusive_disjunction(p, q):
return (p and not q) or (not p and q)
print("p q a")
for p in [True, False]:
for q in [True, False]:
a = exclusive_disjunction(p, q)
print(p, q, a)
See more about python at brainly.com/question/18502436
#SPJ1

The value of the expression X(X+Y) is X
O a. True
b. False
Answers
sorry I didn’t know this was Boolean math
I answered for regular math equations
Which of the following is true about Needs Met rating tasks? Select all that apply.
True
False
Every result has both Needs Met and Page Quality sliders.
True
False
Same as... duplicate results will sometimes be pre-identified for you.
True
False
You should always assign the Needs Met rating before assigning the Page Quality rating.
True
False
Some results do not have an obvious link to a landing page.
Answers
How did early computing device such as Charles Babbage's analytical engine and Ada Lovelace's contributions set the foundation for modern computing
Answers
Early computing devices, such as Charles Babbage's Analytical Engine and Ada Lovelace's contributions, played a crucial role in setting the foundation for modern computing. Here's how their work contributed to computing development:
1. Charles Babbage's Analytical Engine: Babbage designed the Analytical Engine, a mechanical general-purpose computer concept, in the 19th century. Although the Analytical Engine was never fully built, its design and principles laid the groundwork for modern computers. Key features of the analytical engine include:
a. Stored Program: Babbage's Analytical Engine introduced the concept of storing instructions and data in memory, allowing complex calculations and tasks.
b. Control Flow: The Analytical Engine could make decisions and perform conditional operations based on previous computations, resembling the modern concept of control flow in programming.
c. Loops: Babbage's design incorporated looping mechanisms, enabling repetitive instruction execution, similar to modern programming languages.
2. Ada Lovelace's Contributions: Ada Lovelace, an English mathematician, collaborated with Charles Babbage and made significant contributions to computing. Her work on Babbage's Analytical Engine included writing the first algorithm intended for machine implementation. Lovelace realized the potential of the analytical engine beyond numerical calculations and recognized its capability for processing symbols and creating complex algorithms. Her insights laid the foundation for computer programming and algorithms.
Lovelace's ideas about the analytical engine extended beyond what was initially envisioned. He stressed the importance of machines handling more than just numbers. Her contributions demonstrated computers' potential to perform tasks beyond basic calculations and numerical processing.
Collectively, Babbage's analytical engine and Lovelace's contributions provided early conceptual frameworks for modern computing. Their ideas influenced subsequent pioneers in the field, and the concepts they introduced paved the way for the development of the digital computers we use today.
Missing only a few days of school will not impact your grades.
Please select the best answer from the choices provided
OT
OF
Answers
Answer:
Assuming this is a true or false question, it's false.
Explanation:
Need help with this python question I’m stuck



Answers
It should be noted that the program based on the information is given below
How to depict the programdef classify_interstate_highway(highway_number):
"""Classifies an interstate highway as primary or auxiliary, and if auxiliary, indicates what primary highway it serves. Also indicates if the (primary) highway runs north/south or east/west.
Args:
highway_number: The number of the interstate highway.
Returns:
A tuple of three elements:
* The type of the highway ('primary' or 'auxiliary').
* If the highway is auxiliary, the number of the primary highway it serves.
* The direction of travel of the primary highway ('north/south' or 'east/west').
Raises:
ValueError: If the highway number is not a valid interstate highway number.
"""
if not isinstance(highway_number, int):
raise ValueError('highway_number must be an integer')
if highway_number < 1 or highway_number > 999:
raise ValueError('highway_number must be between 1 and 999')
if highway_number < 100:
type_ = 'primary'
direction = 'north/south' if highway_number % 2 == 1 else 'east/west'
else:
type_ = 'auxiliary'
primary_number = highway_number % 100
direction = 'north/south' if primary_number % 2 == 1 else 'east/west'
return type_, primary_number, direction
def main():
highway_number = input('Enter an interstate highway number: ')
type_, primary_number, direction = classify_interstate_highway(highway_number)
print('I-{} is {}'.format(highway_number, type_))
if type_ == 'auxiliary':
print('It serves I-{}'.format(primary_number))
print('It runs {}'.format(direction))
if __name__ == '__main__':
main()
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
Complete the implementation of the following methods:__init__hasNext()next()getFirstToken()getNextToken()nextChar()skipWhiteSpace()getInteger()
Answers
From method names, I am compelled to believe you are creating some sort of a Lexer object. Generally you implement Lexer with stratified design. First consumption of characters, then tokens (made out of characters), then optionally constructs made out of tokens.
Hope this helps.
What transport layer protocol does DNS normally use?
Answers
Explanation:
DNS uses the User Datagram Protocol (UDP) on port 53 to serve DNS queries. UDP is preferred because it is fast and has low overhead. A DNS query is a single UDP request from the DNS client followed by a single UDP reply from the server.
The transport layer protocol that DNS normally use is the User Datagram Protocol (UDP).
What is transport layer protocol?The Internet Protocol (IP) is a network layer protocol, and the Transmission Control Protocol (TCP) is a transport layer protocol.
A network communication between applications is established and maintained according to the Transmission Control Protocol (TCP) standard. The Internet Protocol (IP), which specifies how computers send data packets to one another, works with TCP.
User Datagram Protocol (UDP) on port 53 is how DNS serves DNS requests. Due to its speed and low overhead, UDP is recommended. A single UDP request from the DNS client and a single UDP response from the server makes up a DNS query.
Therefore, the transport layer protocol used by DNS is User Datagram Protocol (UDP).
To learn more about transport layer protocol, refer to the link:
https://brainly.com/question/4727073
#SPJ12
I need help with excel

Answers
Answer:
B. Use a VBA macro that checks the Age column for....
Explanation:
Almost anything can be accomplished with code ;)
Hope this helps! :)
please mark brainiest
What is a soulmate sketch
Answers
(Geometry: area of a regular polygon)
A regular polygon is an n-sided polygon in which all sides are of the same length and all angles have the same degree (i.e., the polygon is both equilateral and equiangular). The formula for computing the area of a regular polygon is
area = (n * s^2) / (4 * tan(PI / n)
Here, s is the length of a side. Write a program that prompts the user to enter the number of sides and their length of a regular polygon and displays its area.
Answers
Answer:
import math
n = int(input("Enter the number of sides: "))
s = float(input("Enter the length of a side: "))
area = (n * s**2) / (4 * math.tan(math.pi/n))
print("The area is: " + str(area))
Explanation:
*The code is in Python.
Import the math to be able to compute the pi and tan
Ask the user to enter the number of sides and the length of a side
Calculate the area using the given formula
Print the area
ZCS Exercise 1
CASE STUDY
Time 10 min.
Exercise: Understanding the Organizational Structure of Zambikes.
Task: Based on the Zambikes video and the above case study, map the organizational structure of
Zambikes. Your organogram should include the head of departments and employees where
possible.
Answers
Zambikes is a social enterprise based in Zambia that produces and distributes bicycles designed for rugged terrain and rural communities.
What is the structure about?From the available information, we can infer the following organizational structure:
Founders: Zambikes was founded by two Americans, Vaughn Spethmann and Dustin McBride, who are still involved in the company's operations.
Board of Directors: The company has a board of directors that oversees its strategic direction and provides guidance to the management team. The board includes both Zambian and international members.
Management team: The management team is responsible for the day-to-day operations of the company. It includes:
Executive Director: The executive director is responsible for the overall management of the company and its staff. The current executive director is a Zambian woman named Mukuka Mwenechanya.
Operations Manager: The operations manager oversees the production and distribution of bicycles.
Sales and Marketing Manager: The sales and marketing manager is responsible for promoting and selling Zambikes products.
Finance and Administration Manager: The finance and administration manager oversees the financial and administrative functions of the company.
Production team: The production team is responsible for manufacturing Zambikes bicycles. It includes:
Production Manager: The production manager oversees the manufacturing process and ensures that production targets are met.
Welders and Assemblers: The production team includes skilled welders and assemblers who build the bicycles by hand.
Learn more about structures on
https://brainly.com/question/364311
#SPJ1